Using CCP Express Advanced Mode
This section explains how to configure
Cisco IR routers using CCP Express advanced mode. The screens and
configuration steps may slightly vary depending on the WAN configuration
options and the software features supported by the Cisco IR routers.
The Advanced Mode contains the following options:
■
 CCP Express Home Page
CCP Express Home Page
■
 General Settings
General Settings
■
 DHCP/DNS
DHCP/DNS
■
 Interfaces
Interfaces
■
 Identity
Identity
■
 Static Routing
Static Routing
■
 Dashboard
Dashboard
■
 Troubleshooting
Troubleshooting
■
 Access Control Lists (ACLs)
Access Control Lists (ACLs)
■
 IOx
IOx
■
 Wireless
Wireless
■
 Security Features
Security Features
CCP Express Home Page
Once the configuration is pushed, you will be automatically redirected to the Dashboard page in the Advanced Settings section.
CCP Express by default loads in the
New UI from version 3.5.1 onwards. User can switch back to the old UI by
using the Option in Preferences-> Classic View. All existing
features are arranged under 4 groups on the left: Dashboard,
Configuration, Administration and Troubleshoot. The quick access utility
pages/options are on the top right.
Figure 25 New UI in Release 3.5.1 and Later Releases

You can switch between the two UIs using the option in Preferences section.
Below are samples of the old UI.
Figure 26
CCP Express Home Page (IR 829)
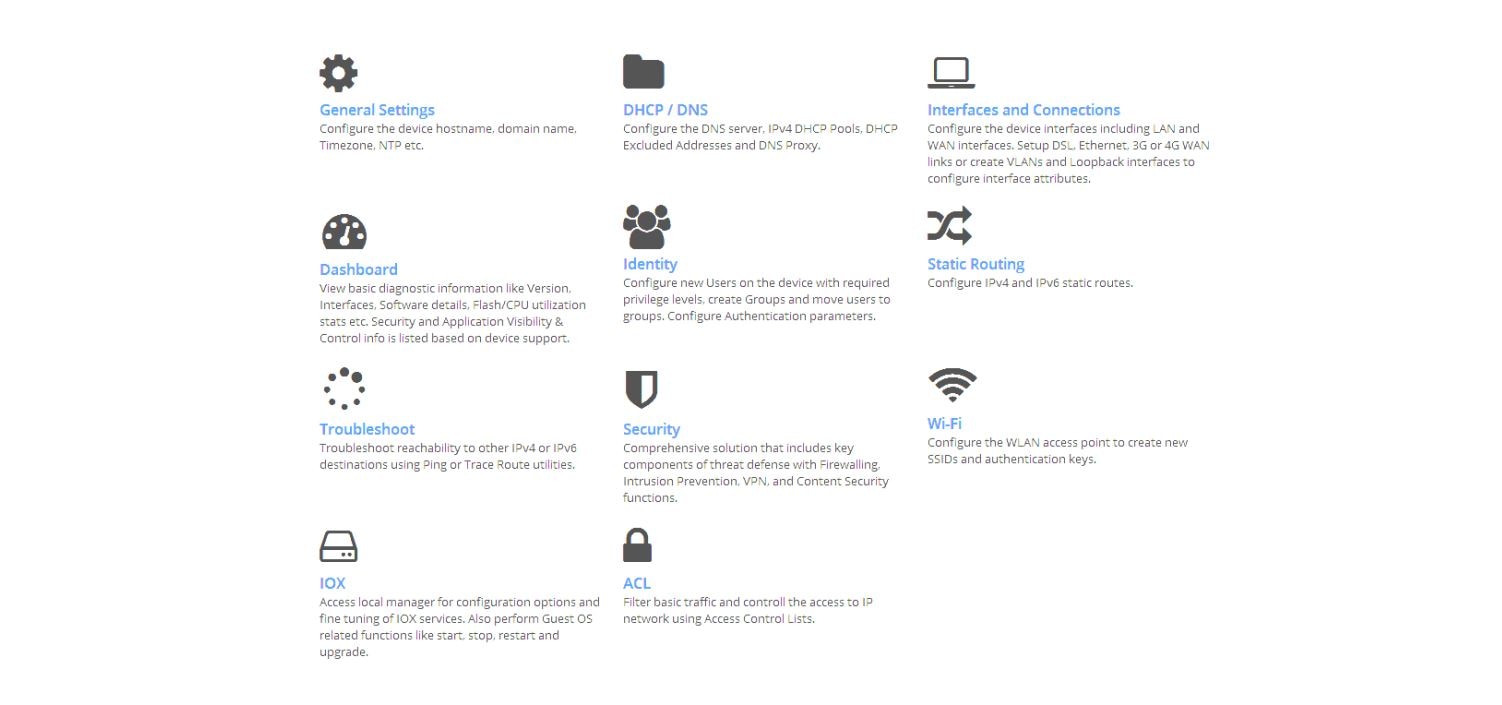
You can get to the CCP Express Home
page by clicking on Advance Mode after going through the Quick Setup
Wizard or by clicking the home icon on the right side of the page:
 CCP Express Home Page (IR 829)
CCP Express Home Page (IR 829) shows CCP Express home page where you can navigate to all the features.
Note: Since the IR809 does not support Wi-Fi, the Wireless option is not available.
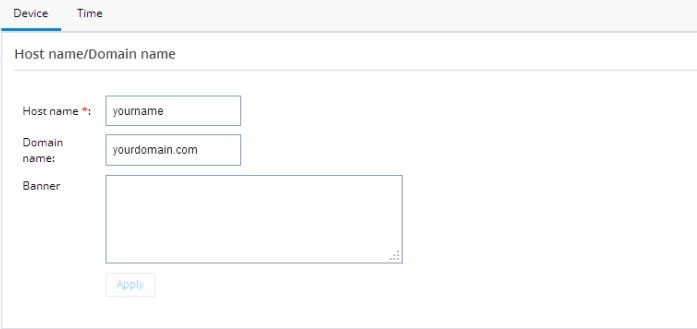
General Settings
Click this option to configure Device and Time.
If you used the Quick Setup Wizard to configure your router, the device settings shown in
Device Settings are automatically listed here. If not, enter the Host name and Domain name.
Figure 27
Device Settings
Use the Time tab to change the timezone. You can also synchronize to the NTP server or make the router an NTP master.
Figure 28 Time Settings

SNMP Configuration
To enable SNMP configuration:
1.
Go to General Settings
2.
Click the SNMP Tab.
All options are available under different tabs once SNMP is enabled on the box.
Figure 29 General SNMP Settings

Figure 30 SNMP Communities
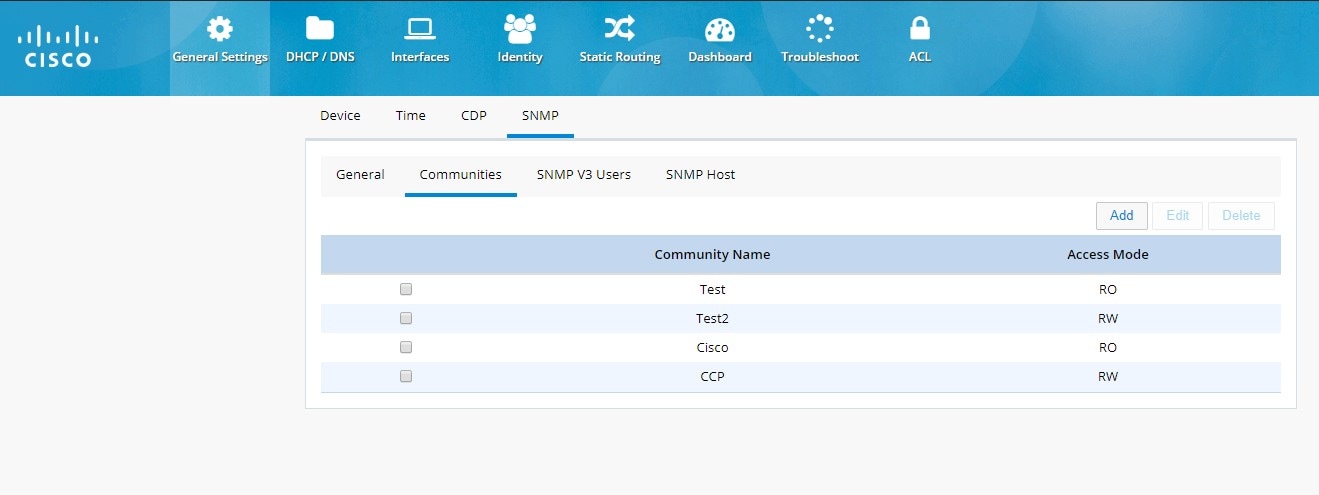
Figure 31 SNMP V3 Users

Figure 32 SNMP Host

Gyroscope
Gyroscope is used to determine the position of the device.
1.
Go to General Settings
2.
Click the Gyroscope Tab.
Figure 33 Gyroscope
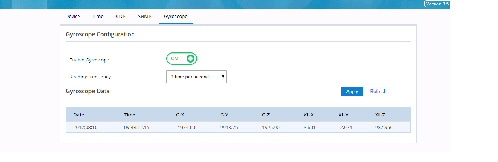 3.
3.
Click the Enable Gyroscope.
4.
Select the Reading frequency from the menu.
5.
Click
Apply.
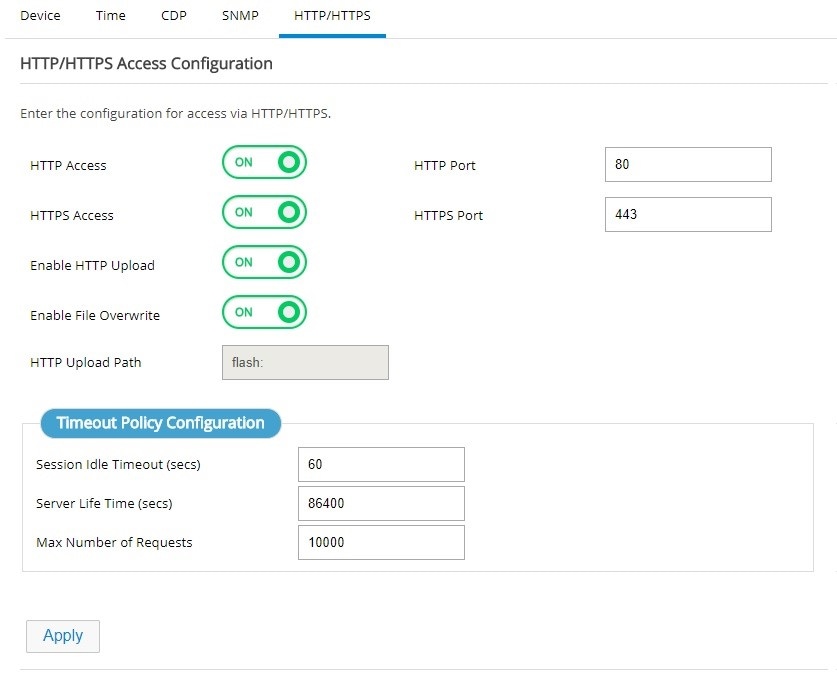
HTTP/HTTPS Configuration
Http/Https configuration is available under General Settings -> HTTP/HTTPS tab.
Note: This feature is available in Release 3.5.1 and later.
Figure 34 HTTP/HTTPS Configuration
DNS
Figure 35 Primary and Secondary DNS
DDNS
If you have not completed setting up your WAN interface, you see the following message:

DHCP
Figure 36 DHCP
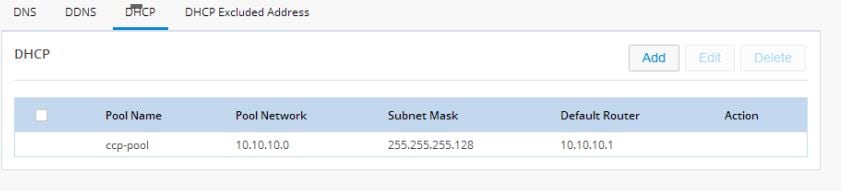
Configuring a LAN with DHCP
Perform the following steps to create a DHCP pool.
1.
Click DHCP/DNS and DHCP to open the DHCP tab.
2.
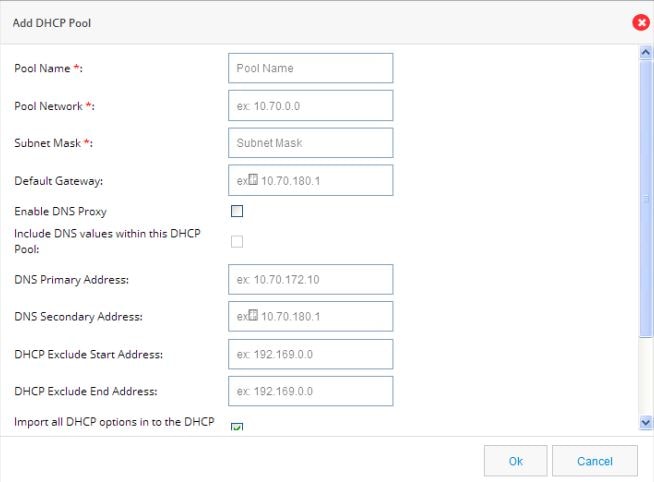
From the DHCP interface, click Add to create a new DHCP pool by specifying:
■

Pool Name:—The name of the DHCP pool.
■

Pool Network:—The IP address of the subnet that represents all IP addresses allocated to the wired or wireless clients.
■
 Subnet Mask:
Subnet Mask: —The subnet mask.
■

Import
all DHCP options in to the DHCP server database: Check this check box
to import all DHCP options into the DHCP server database. This ensures
that the DNS is read from your service provider and is propagated to all
DHCP clients.
Figure 37 Add DHCP Pool
 3.
3.
Click OK to create the DHCP pool.
DHCP Excluded Addresses
To configure DHCP Excluded Addresses:
1.
Click DHCP/DNS and DHCP to open the DHCP tab.
2.
Click
Add to create a new pool with the excluded addresses. Or, click
Edit to add the excluded addresses to an existing pool.
Figure 38 Configure DHCP Excluded Addresses
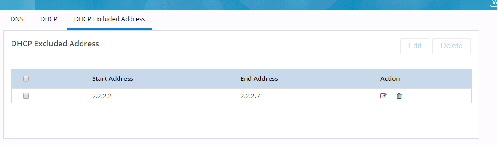 3.
3.
Enter the Start and End DHCP excluded addresses. Ensure the start address value is smaller than the end address value.
To edit an existing DHCP Excluded Address:
1.
Click DHCP/DNS and DHCP Excluded Addresses tab.
2.
Select the address, and click
Edit.
Figure 39
Edit a DHCP Excluded Address
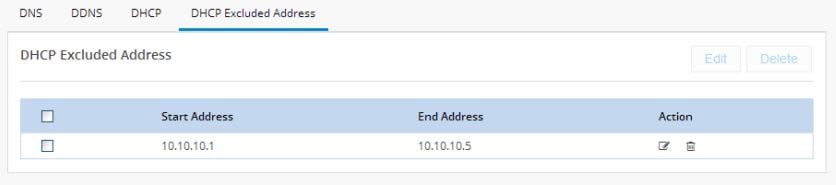 3.
3.
Specify the IPv4 address which is the starting for the range to be excluded.
4.
Specify the IPv4 address which is the end of range to be excluded.
5.
Click OK.
To delete an existing DHCP Excluded Address:
1.
Click DHCP/DNS and DHCP Excluded Addresses tab.
2.
Select the address, and click
Delete. See Edit a DHCP Excluded Address.
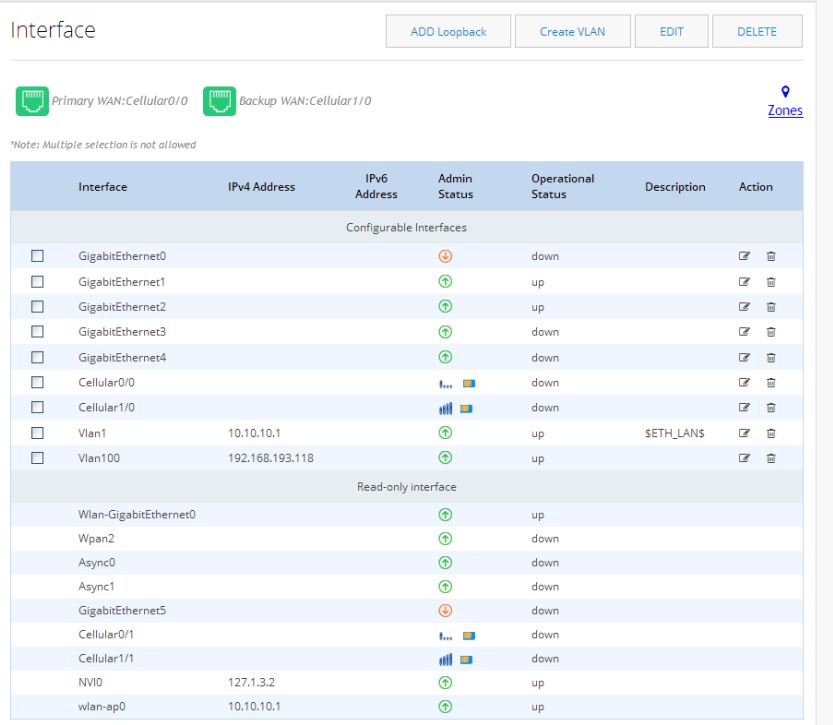
Interfaces
Use this option to configure primary and/or backup for Ethernet and Cellular interfaces.
Figure 40 Interfaces List
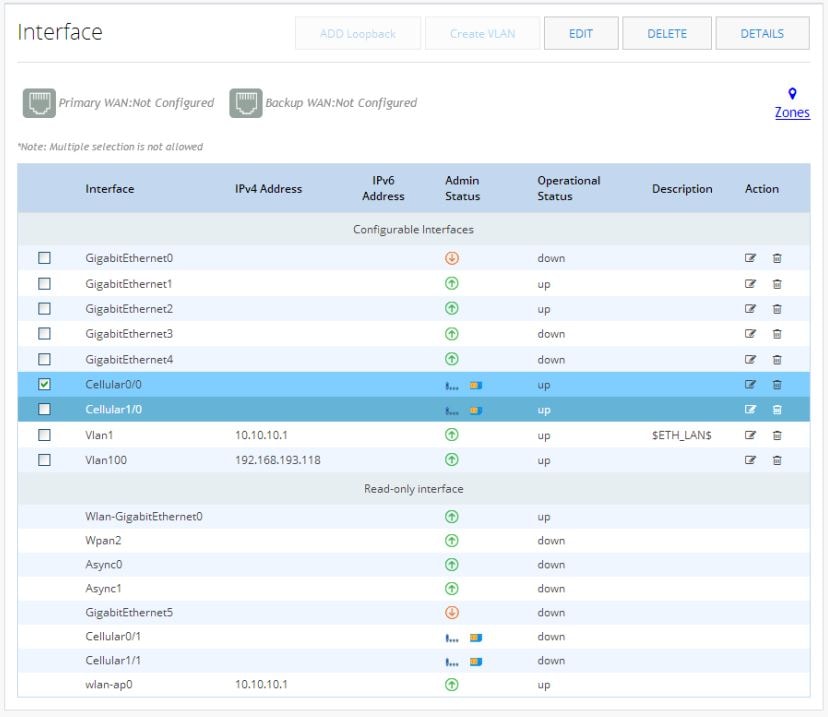
The Zones link takes you to the Zones page under the Security option. See
The Zones Page.
Setting Up a Primary Ethernet WAN Interface
1.
Click
Interfaces to open the Interfaces page.
2.
Select the GigabitEthernet Interface you want to configure and click
Edit. The Edit GigabitEthernet Configuration page is displayed.
Figure 41 GigabitEthernet Interface Configuration
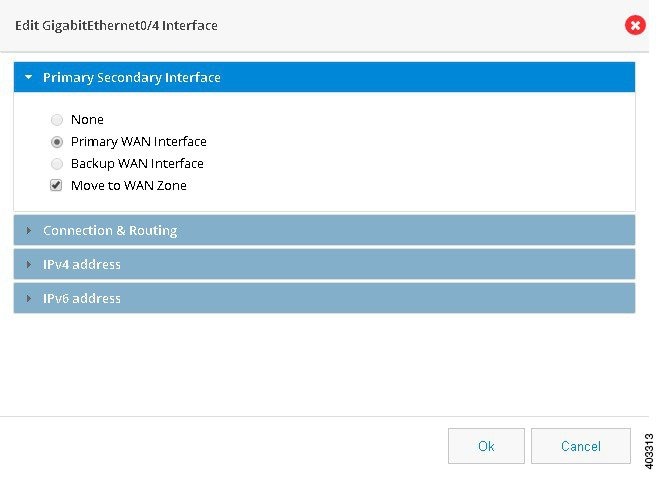 3.
3.
Select Primary WAN Interface from Primary Secondary Interface tab.
4.
From the Connection & Routing tab, check Enable PPPoE check box,
and enter the description in the description field. For IPv4 Routed
Protocol, you may configure Ipv6oE with options of Bridge or DHCP
configuration.
5.
From the Connection tab, check Enable PPPoE check box, and enter the description in the Description field.
6.
Based on whether you are configuring an IPv4 or IPv6 address, select
the appropriate tab. Specify the details for the IP address depending on
whether the IP address is dynamically or statically assigned.
For configuring an IPv4 address:
This can be either Easy IP (IP
Negotiated), Static IP Address, or No IP Address. By default, the IPv4
address is IP negotiated. There is an option to enable NAT configuration
and the recommendation is to enable NAT for WAN interfaces. This will
create NAT overloading configuration hence all LAN IPs are translated to
public IP before being sent to WAN uplink.
For configuring an IPv6 address:
Select the IPv6 address type. The IPv6
address can be either AutoConfig, Use Prefix from Provider, Static IP
Address, or No IP Address.
7.
From the Authentication tab, check CHAP or PAP check box and specify the username and password given by Service provider.
8.
Click
OK to confirm the configuration.
Setting up a Primary Cellular Interface
1.
Click on the cellular interface you want to create as a primary.
Figure 42 Edit Cellular Interface
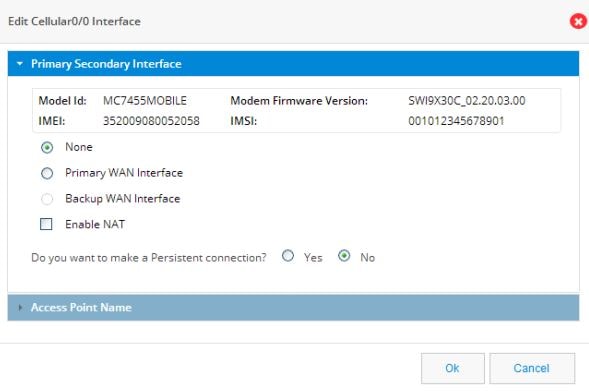 2.
2.
Select Primary WAN Interface.
3.
(Optional) Enable NAT.
4.
(Optional) Select Move to WAN Zone to add this interface to a zone. If you select this option, the following message appears:
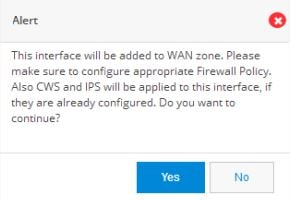 5.
5.
Click Yes to continue.
6.
If you want to establish a persistent connection to your service
provider, select Yes. By default, this is set to No to disable
persistent connection.
7.
Click OK.
In the main Interfaces list, the Primary WAN Interface is green and lists the primary interface.
Figure 43 Configured Cellular Primary Interface
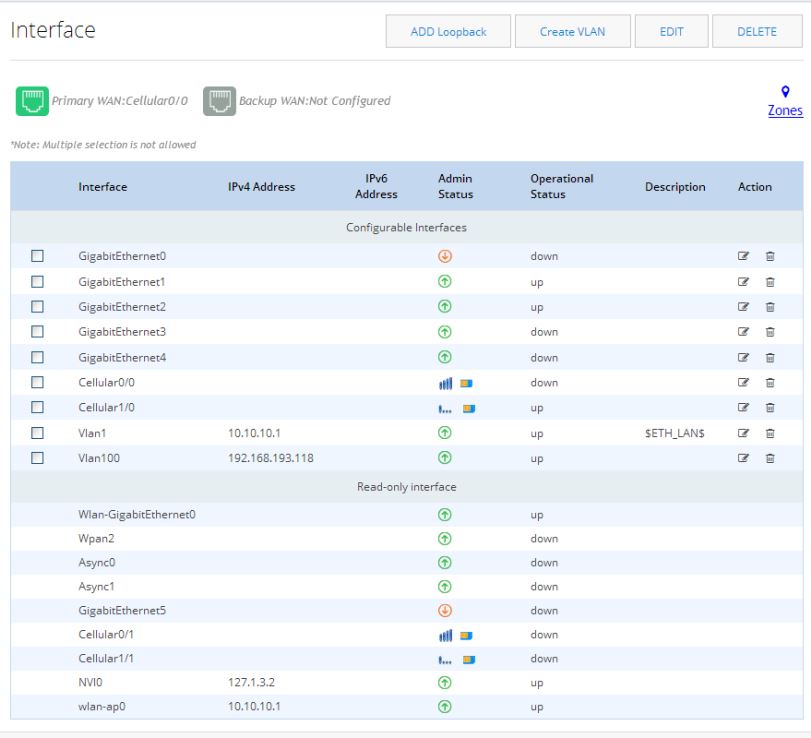
Setting up a Backup Cellular Interface
1.
Click on the cellular interface you want to create as a primary.
Figure 44 Edit Cellular Interface
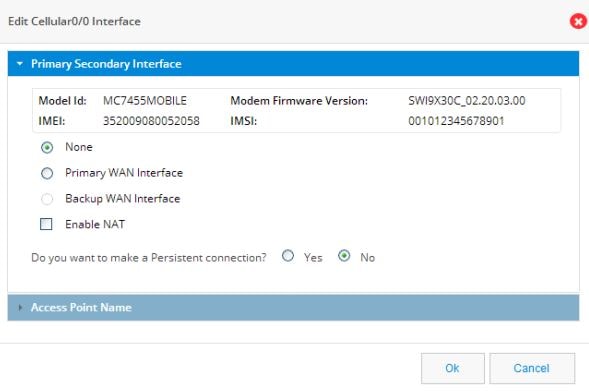 2.
2.
Select Backup WAN Interface.
The SLA Configuration box displays.
3.
(Optional) Enter the IP address of a reliable website to check connectivity.
4.
(Optional) Enable NAT.
5.
(Optional) Select Move to WAN Zone to add this interface to a zone. If you select this option, the following message appears:

In the main Interfaces list, the Backup WAN Interface is green and lists the backup interface.
Figure 45 Configured Cellular Backup Interface
Create VLANs (only for IR 829)
Note: VLANs are not supported on IR 809.
1.
Click
Add VLAN to open the Add VLAN dialog box and specify a unique ID for the VLAN being created.
2.
From the IPv4 address tab, choose Select from DHCP, and then select the
DHCP pool from the drop-down list.This enables you to assign the IP
addresses from the DHCP pool that is created.
or
Select Static IP to assign a unique IP address to the VLAN.
3.
Click
OK to confirm the configuration.
Identity
Identity awareness is a key
requirement for any Security solution. It is defined as the ability of
the device to be aware of end-user identities. Also this supports User
and Group management that allows administration of user authentication
and authorization profiles using either local or external service.
Authentication
To configure authentication:
1.
Click Identity > Authentication.
2.
In Authentication Servers section, select the local or remote option.
–

Enable local (on-box) server—Router acts as the local authentication server.
–

Enable remote (external) server—Active Directory is supported.
If remote option is selected, the ADD new server option appears.
a.
Click ADD new server.
b.
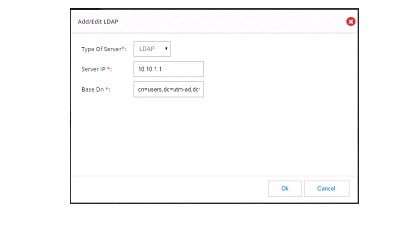
Enter the LDAP details: IP address of the server and Base DN information. Click
OK.
Note: You can choose to
configure both the server options. If both are configured, first attempt
with authentication is with the remote server. If the remote server is
not reachable, authentication falls back to the local server.
3.
In the Authentication Services section, you can select Web Auth or NTLM.
The authentication method can be
chosen for different zones, but in the current release only LAN zone is
supported. If LAN Zone is configured, all interfaces coming under LAN
zone are configured accordingly. NTLM option is supported only for
remote server option. If the you configure both on-box and remote server
options, selecting NTLM option is not allowed.
Figure 46 Authentication Page
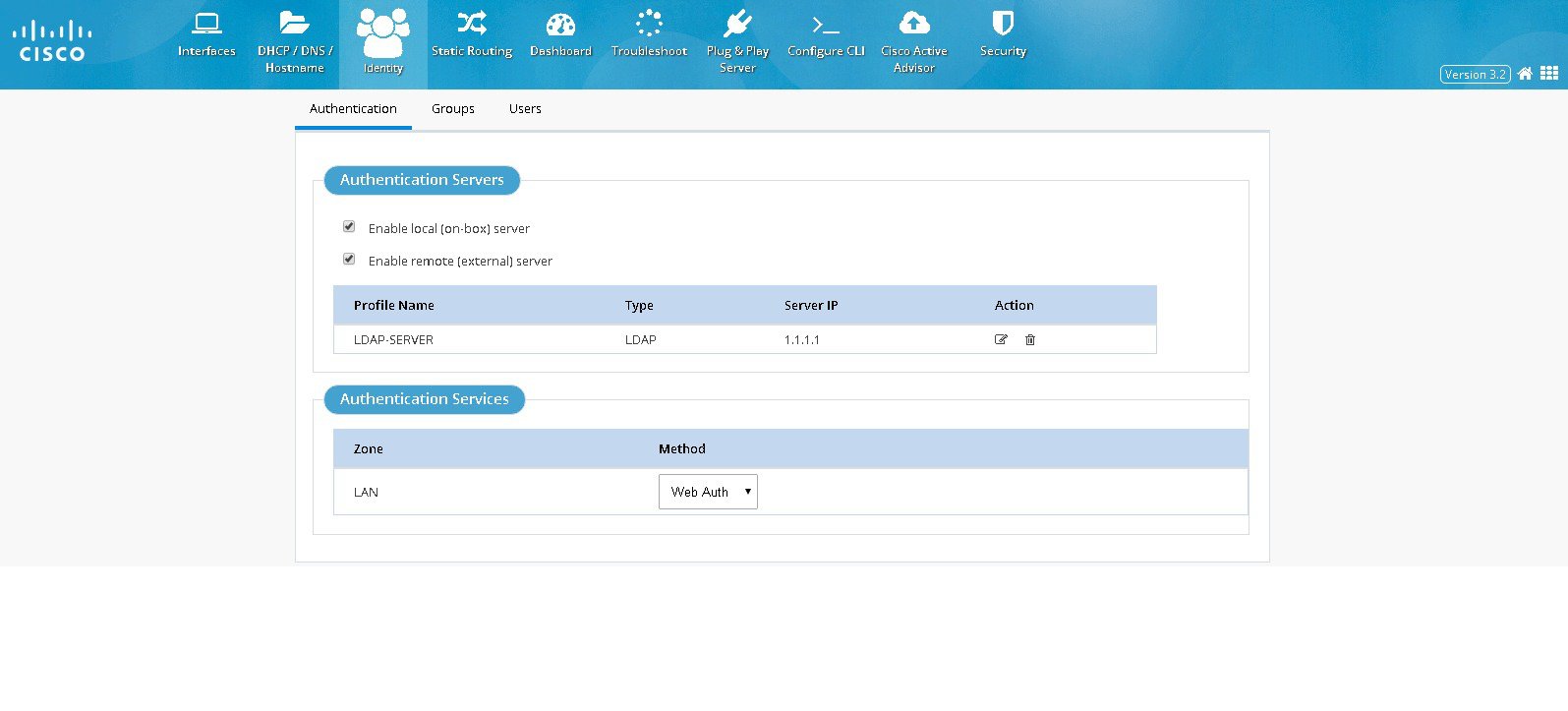
Figure 47 Add/Edit LDAP Page
Managing User Groups
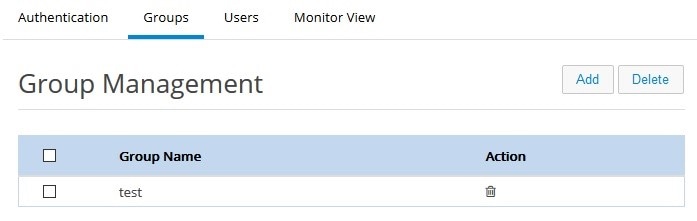
To create or delete user groups or to see the list of created user groups:
1.
Click Identity > Groups. The list of available groups is displayed.
2.
Click Add. Enter the user name in the popup.
3.
Enter the group name to be created.
Figure 48 Group Management Page
 4.
4.
To delete any group, select the check box and click on Delete and confirm.
Managing Users
Steps to create a new user and associate/dissociate a user with a group are listed below:
1.
Click Identity > Users. All created user names are listed. (
User Management Page)
2.
Click Add. The add user popup is displayed.
3.
Enter the user details and click
Ok.
Figure 49
User Management Page
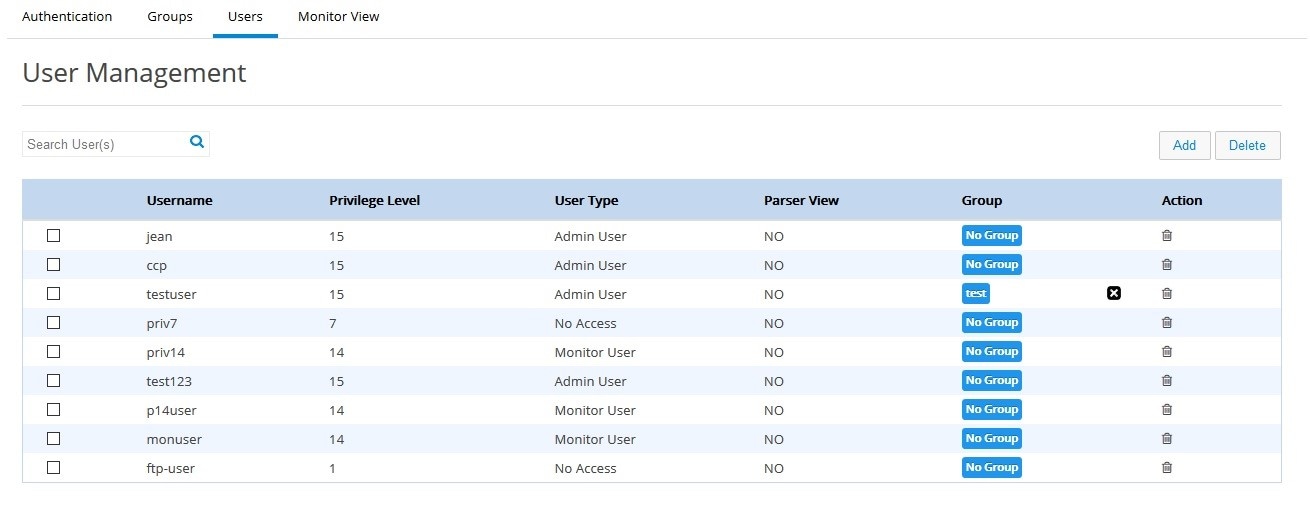
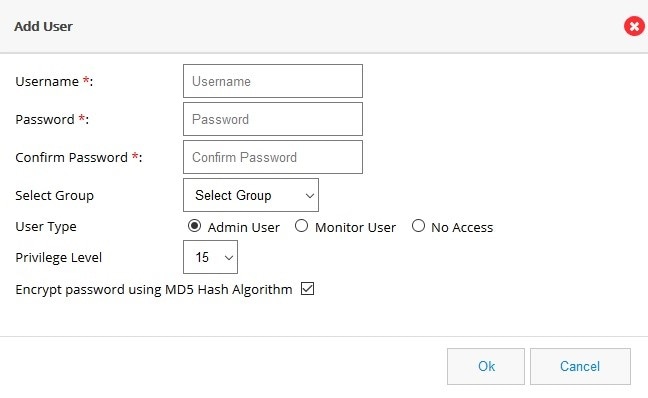
Figure 50 Add User Page
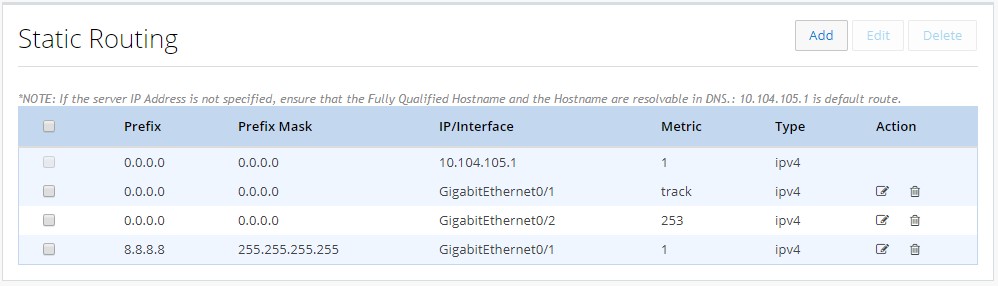
Creating a Static Route
To create a static route:
1.
Click Static Routing to open the Static Routing page.
Figure 51 Static Routing
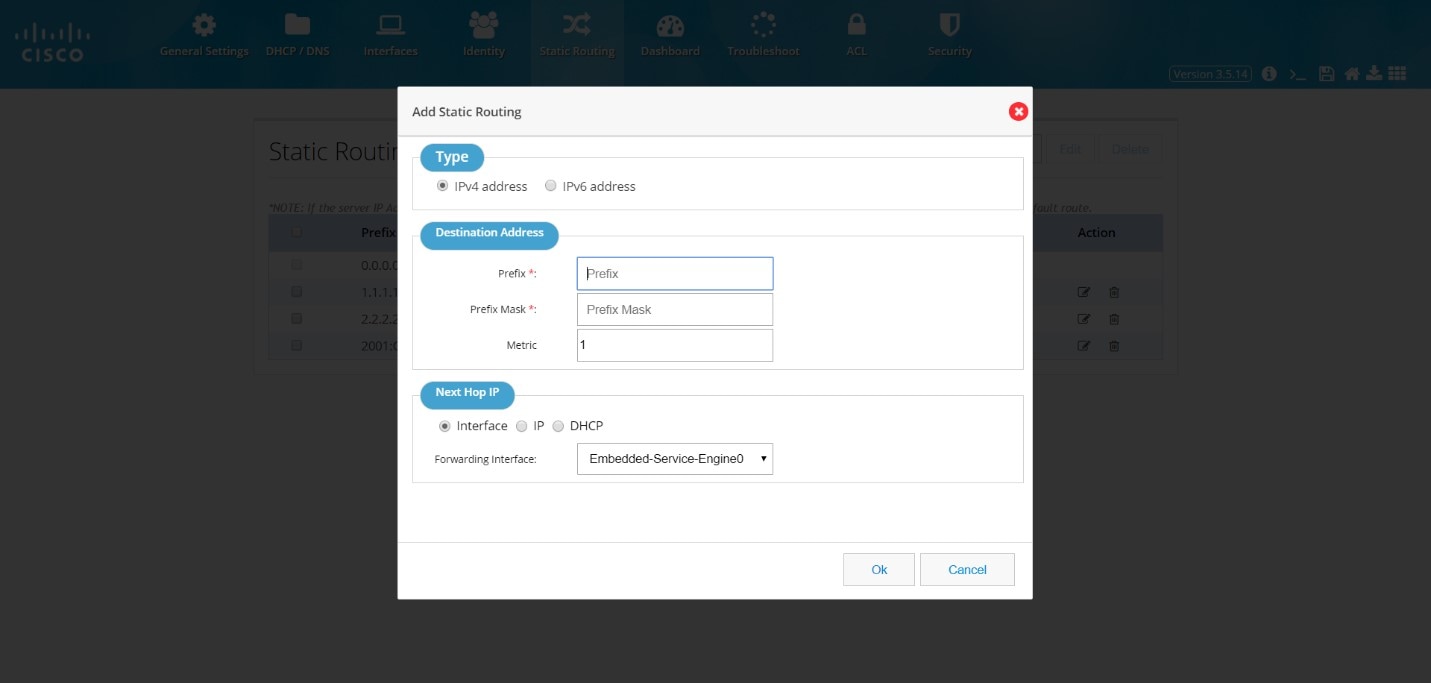
 2.
2.
Click Add to open the Add Static Routing dialog box with options to specify an IPv4 or IPv6 static route.
Figure 52 The Static Routing page
 3.
3.
Based on whether the IP address is an IPv4 or IPv6 address, select the IPv4 or IPv6 tab, and specify the following:
■

Destination address: Specify the prefix and prefix mask for your IPv4 or IPv6 address.
■

Next Hop IP:
If you select Interface as the next hop IP, select the forwarding interface from the drop-down list.
If you select IP as the next hop IP, specify the Next Hop IP that must be used.
You can also specify DHCP address.
4.
Click OK to add the static route.
Editing a Static Route
To edit an existing static route:
1.
Click Static Routing to open the Static Routing page.
2.
From the list of static routes, select the static route you want to edit, and click Edit.
The Edit Static Routing page is displayed.
3.
Specify these fields for your static route:
■

Destination address: specify the prefix and prefix mask for your IPv4 or IPv6 address
■

Next Hop IP:
If you select Interface as the next hop IP, select the forwarding interface from the drop-down list.
If you select IP as the next hop IP, specify the Next Hop IP that must be used.
4.
Click OK to edit the static route.
Deleting a Static Route
To delete a static route:
1.
Click Static Routing to open the Static Routing page.
2.
From the list of static routes, select the static route you want to delete, and click Delete.
Dashboard
The Dashboard view shows the vital
hardware health status of the router along with the flash and system
memory, CPU utilization, and WAN Interface status and security aspects
of network. The Dashboard has two sections Router and Security.
Viewing Router Dashboard
To view the router diagnostics using the dashboard view, perform these steps:
1.
Click on Dashboard> Router to open the Router Diagnostics dashboard view.
The Dashboard page
Hardware Health
section shows the total Power Consumption of the router, Number of Fans
on the system and their status, CPU Temperature and Battery health. If
the router does not expose its hardware information, then this section
will not be visible in the UI.

If Primary and Backup WAN Interfaces
are configured, then the status of the same is displayed along with the
interface Name. The status is shown in green only when both admin and
operational status are up. This also shows the amount of traffic flowing
through WAN Interfaces.
Note: The following sections
have been moved to the System Information Popup: Hostname, Device Type,
IOS Version, System Uptime from last reload, current System Time, and
the Reason for Last Reload of the router. The Interfaces chart is moved
under the Interfaces tab.
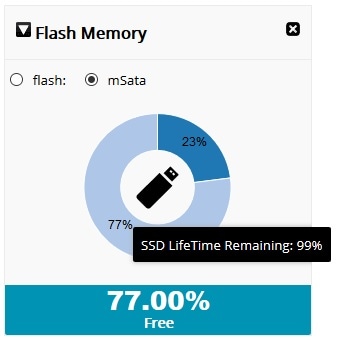
Beginning with CCP Express Release
3.5.2, for IR829M series devices, the Flash Memory dashlet will display
two radio buttons: “flash” and “mSata.” The flash option retains the
current dashlet data which is the pie chart that shows used and free
space on the flash memory. If you select the mSata option, the used and
free data of the SSD is displayed. You can hover on the flash icon and
get the remaining lifetime for the SSD also.
Figure 53 Flash Memory Dashlet
 2.
2.
To update the charts, click on the refresh button given at the top of the charts section.
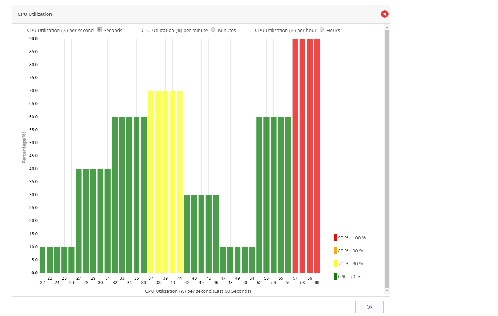
CPU Utilization Dashlet
To access the new CPU Utilization dashlet:
1.
Go to the Router Dashboard.
2.
Under the CPU dashlet, click Details.
A new dashlet is shown in a popup
dialog. The details of CPU usage are in percents for different intervals
available in the new dashlet.
Security Dashboard
To view the security dashboard view, perform these steps:
1.
Click on Dashboard> Security to open the Security dashboard view.
Figure 54 Security Dashboard (Dashlets displayed are Top 10 Applications and Top Users)
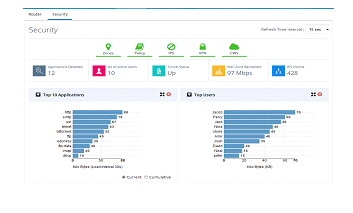
Figure 55 Security Dashboard (Dashlets displayed are VPN, Policy, Top 10 Threats and IPS Drilldown)
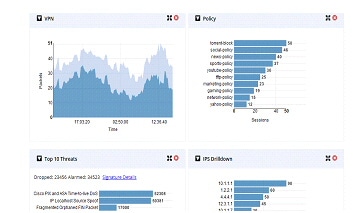
Figure 56 Security Dashboard (Dashlets displayed are Firewall Drop and CWS Connections)

The top portion shows the security
features enabled on the device. The green icon indicates they are
enabled. User can click on a specific icon and navigate to that feature.
If any security feature is not enabled, then the relevant charts are
not visible. They will be minimized and shown in the tray above the pane
which is showing the security features ennoblement status. To close any
chart click on the close button of the chart and the chart will be
minimized into the tray. The icons can be clicked to enable it again.
Security Snapshot
■

Applications
Detected—Total number of Application protocols discovered by NBAR.
While moving the mouse over, the list of applications will be displayed.
■

Number of Active Users—Top users contributing to the traffic currently traversing the device.
■

Tunnel Details—Hover over this option to list the VPN tunnels present along with the status (up or down).
■

WAN Zone Bandwidth—Traffic going through the WAN Interfaces.
■

IPS Victims—Total number of users impacted by some attack. The information is obtained by enabling the IPS feature.
Security Charts
Following is the list of various
charts supported to show the security information and bandwidth
consumption statistics of the network. These charts will update
periodically. The refresh interval can be modified.
■

Top
Applications—This dashboard will list the top 10 application protocols
contributing to the traffic through the router in terms of bandwidth
consumption at any point of time. This chart will also provide the
cumulative bandwidth consumption of the device from the time of router
reload. CCP Express will get the update from device at configured
regular intervals.
■

Top
Users—This dashboard will list the top users in the router in terms of
bandwidth consumption at any point of time. It supports both current
bandwidth consumption.
■

VPN—VPN chart shows encrypted and decrypted traffic through the configured VPN tunnel.
■

Policy—Policy
chart shows the amount of data that matched a specific Firewall Policy
configured on the device. This gives the snapshot view of which policy
is hit the most in the network.
■

Top Threats—This dashboard shows the Top 10 threats in the network in terms of malicious packets.
■

IPS Drilldown—This dashboard shows the total attacks made by the attackers and attacks received by the victims.
■

Firewall drop—This dashboard shows the Top 10 firewall drops and the cause of the drops.
Application Visibility and Control (AVC) Dashboard
To view the AVC dashboard, perform these steps:
1.
Click Dashboard> AVC to open the AVC dashboard view.
2.
Enable AVC, a screen appears where you can drag and drop the interfaces to AVC interfaces.
Figure 57 Configuring AVC
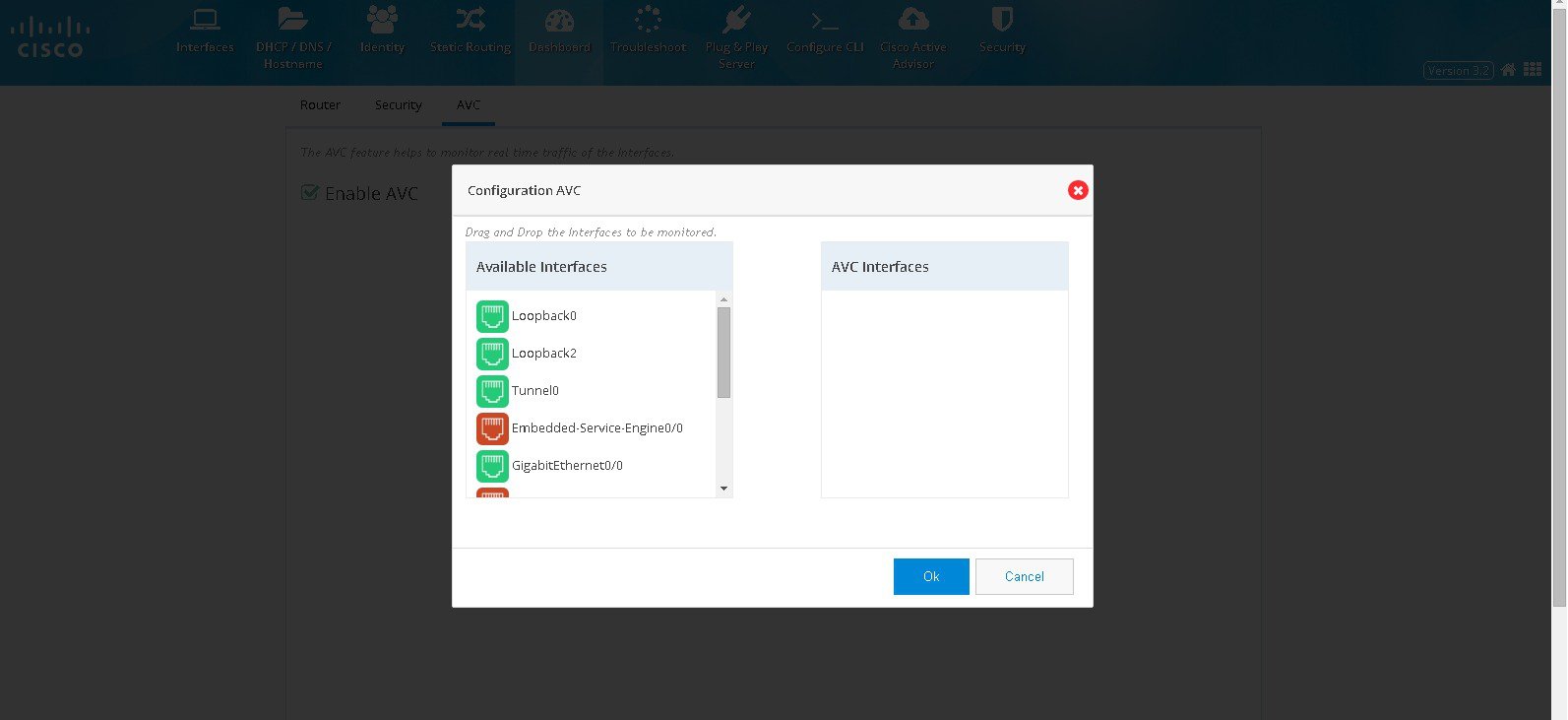 3.
3.
Click OK.
AVC Dashboard
displays. This page displays all the applications and the relevant
data. At a time 8 applications are listed in the page. You can filter
applications using the search option.
Figure 58
AVC Dashboard
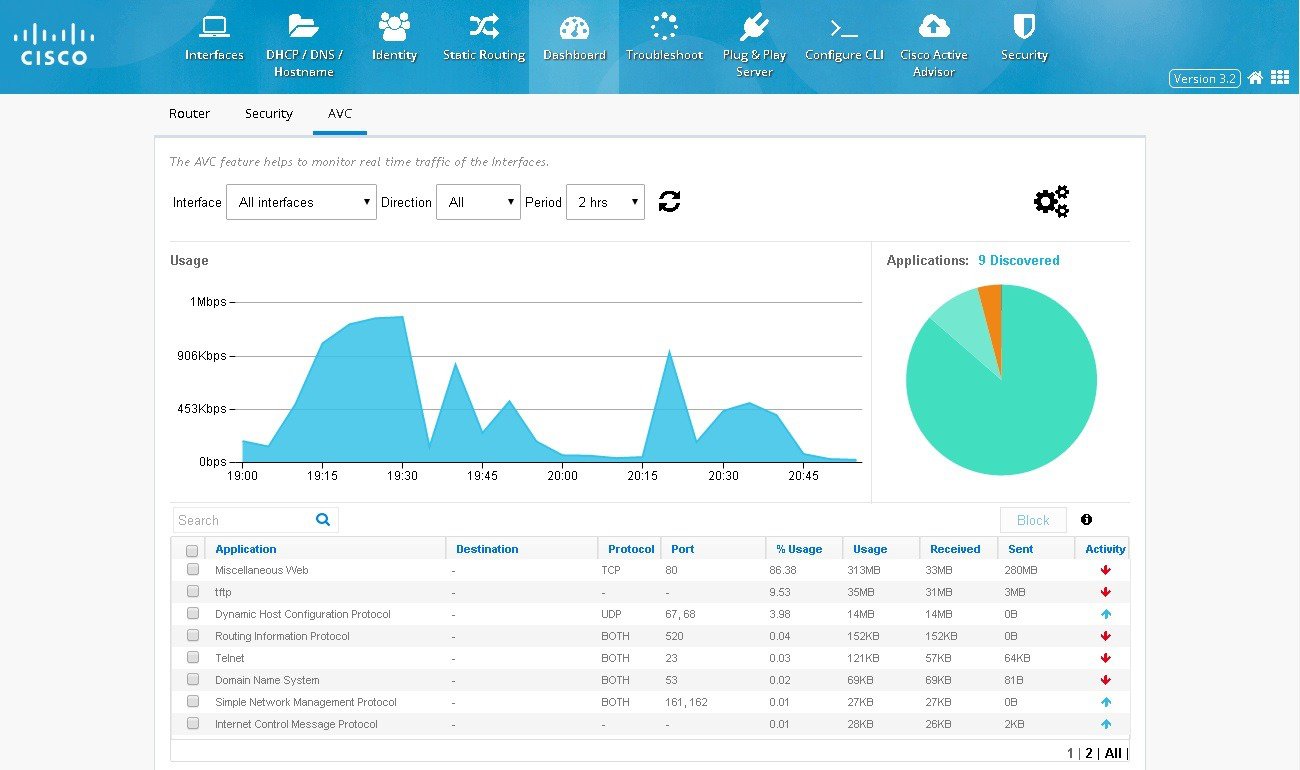 4.
4.
You can also click Settings icon to add or remove interfaces for AVC.
5.
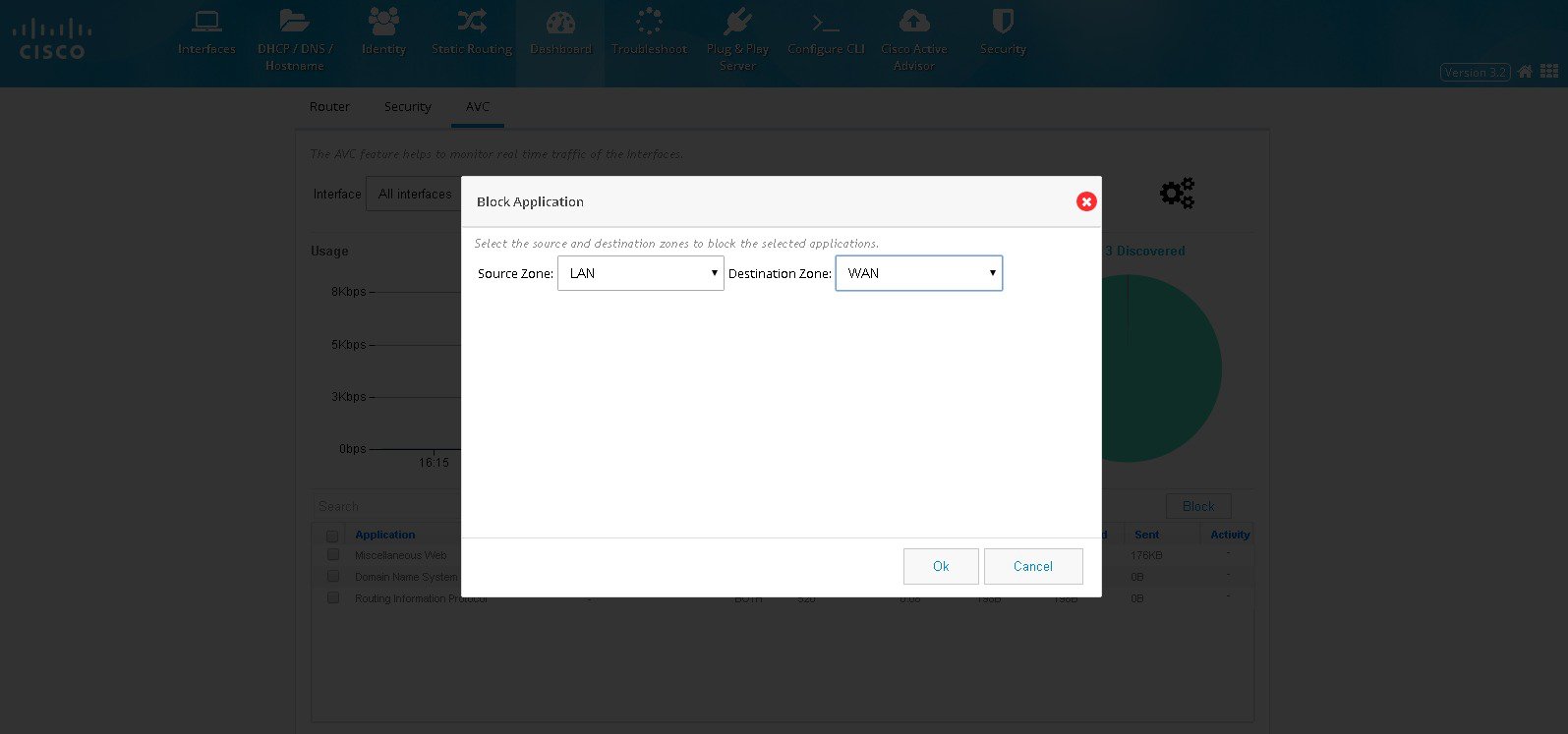
If security is enabled, you can block the applications in AVC screen.
Select the applications and click BLOCK. Select the Source and
Destination Zone and click OK. (
Blocking Applications).
Selected application will be blocked. When an application is blocked, a
policy is automatically created by the name avc-app-block-1. The
subsequent blocking of applications will add policies with the same name
format with only the numbering incremented.
Figure 59
Blocking Applications
Interfaces Dashboard
To view the Interfaces dashboard, perform these steps:
1.
Click Dashboard> Interfaces to open the Interfaces dashboard view.
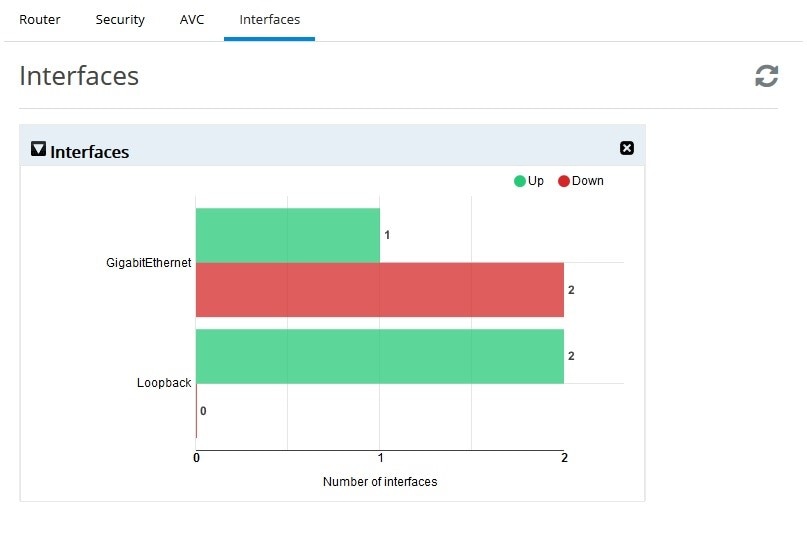
Interfaces chart groups the Interfaces
by type and shows the number of interfaces that are up and down. If the
user moves the cursor over the chart, then the specific interfaces will
be displayed as tool tip.
Figure 60 Interfaces Dashboard
Ping and Traceroute
The Ping and Traceroute utility allows you to do a basic troubleshooting of the network and device connectivity.
To troubleshoot the device connectivity, perform these steps:
1.
Click Troubleshoot to open the Ping and Traceroute tab.
Figure 61 Ping and Traceroute
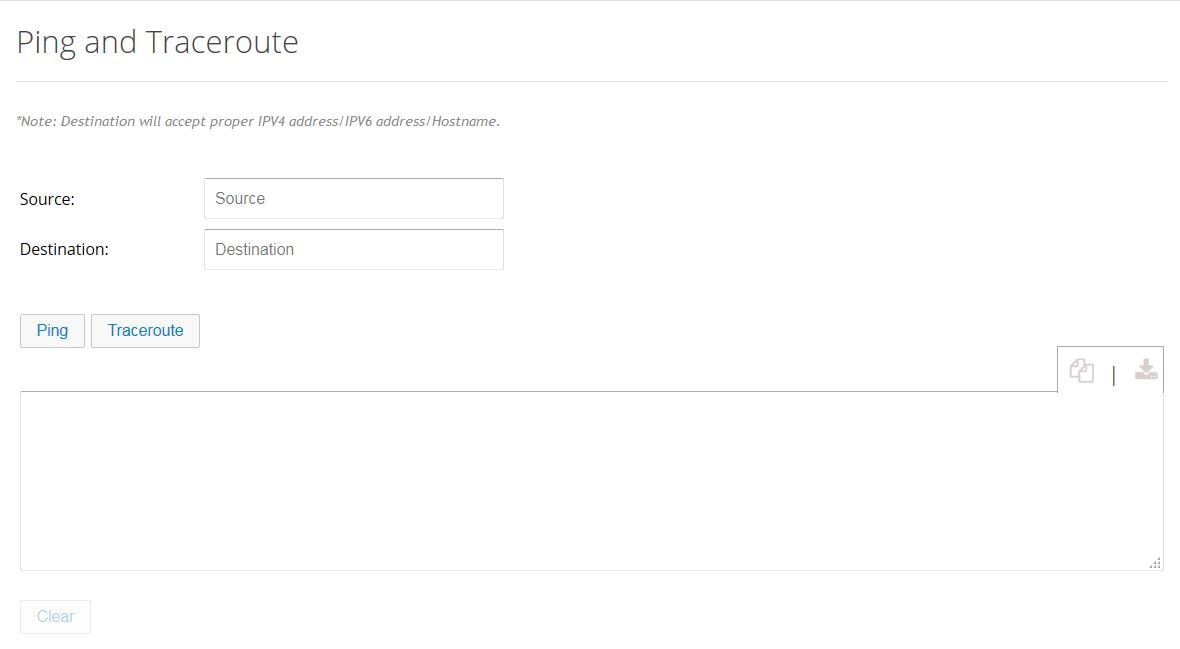 2.
2.
(Optional) Specify the source IP address (IPv4 or IPv6 address) or interface.
3.
Specify the destination IP address (IPv4 or IPv6 address) or hostname.
4.
Click Ping to verify whether the destination IP address is reachable.
5.
Click Traceroute to view the list of routes traversed between the source and destination IP addresses.
6.
You can also copy-to-clipboard or download the retrieved data by
clicking on COPY or DOWNLOAD icons to the right of the details box.
Test WAN Connection
If you do not have a primary interface configured, the following message appears:
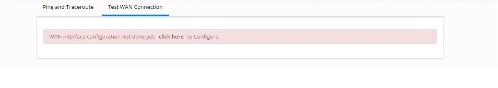
If a primary interface is configured without an IP address, the following information appears:
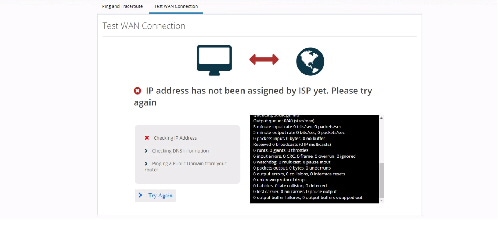
If a primary interface is configured with an IP Address and DNS details, the following information appears:
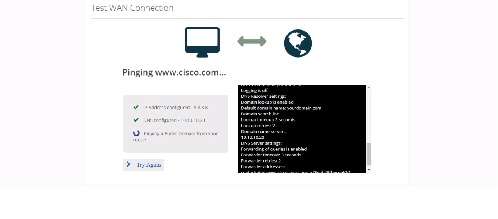
For a successful connection, the following information appears:

Access Control Lists (ACLs)
Filter traffic and control access to the IP network using the ACL option from the main menu.
Figure 62 ACL Summary
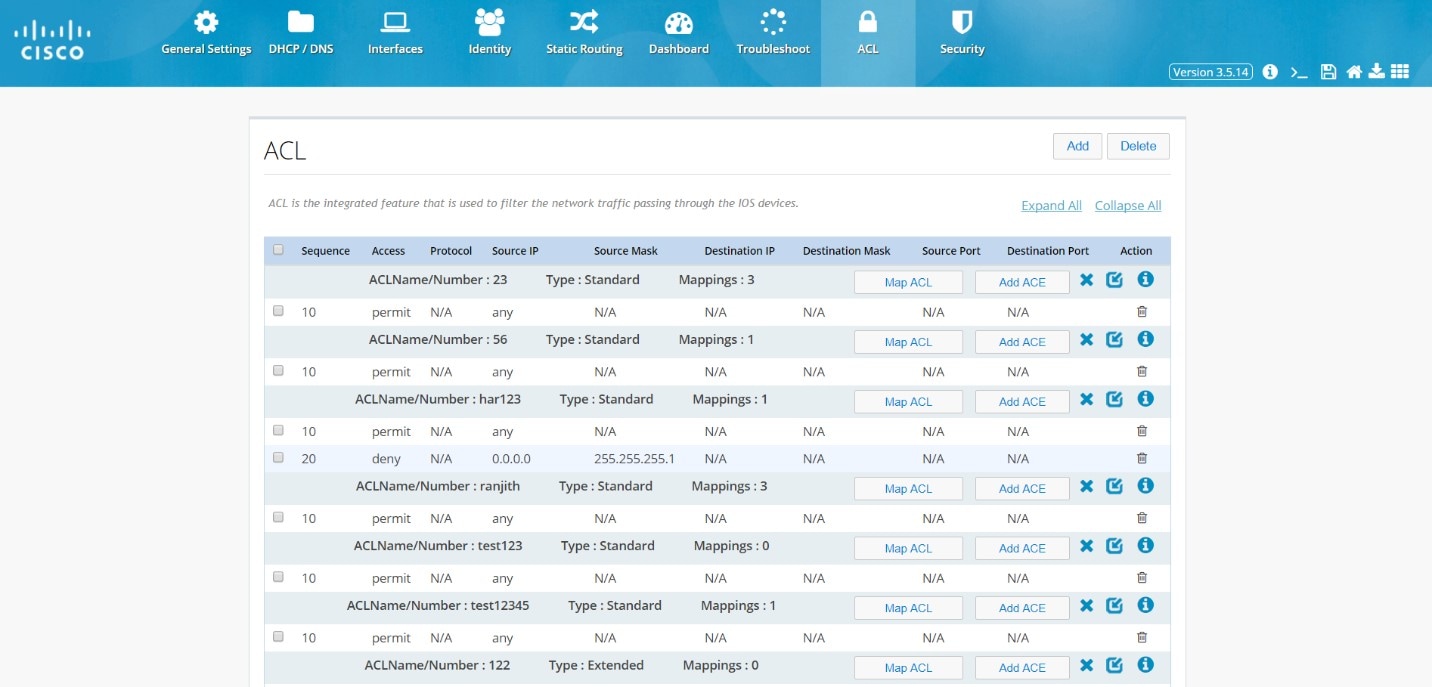
This page includes the Map ACL and Add
ACE buttons for each ACL. Hover over the icons on the right to remove
an ACL, expand and collapse an ACL.
Add an ACL
To add an ACL:
1.
From the Summary screen, click
Add.
Figure 63 Add ACL
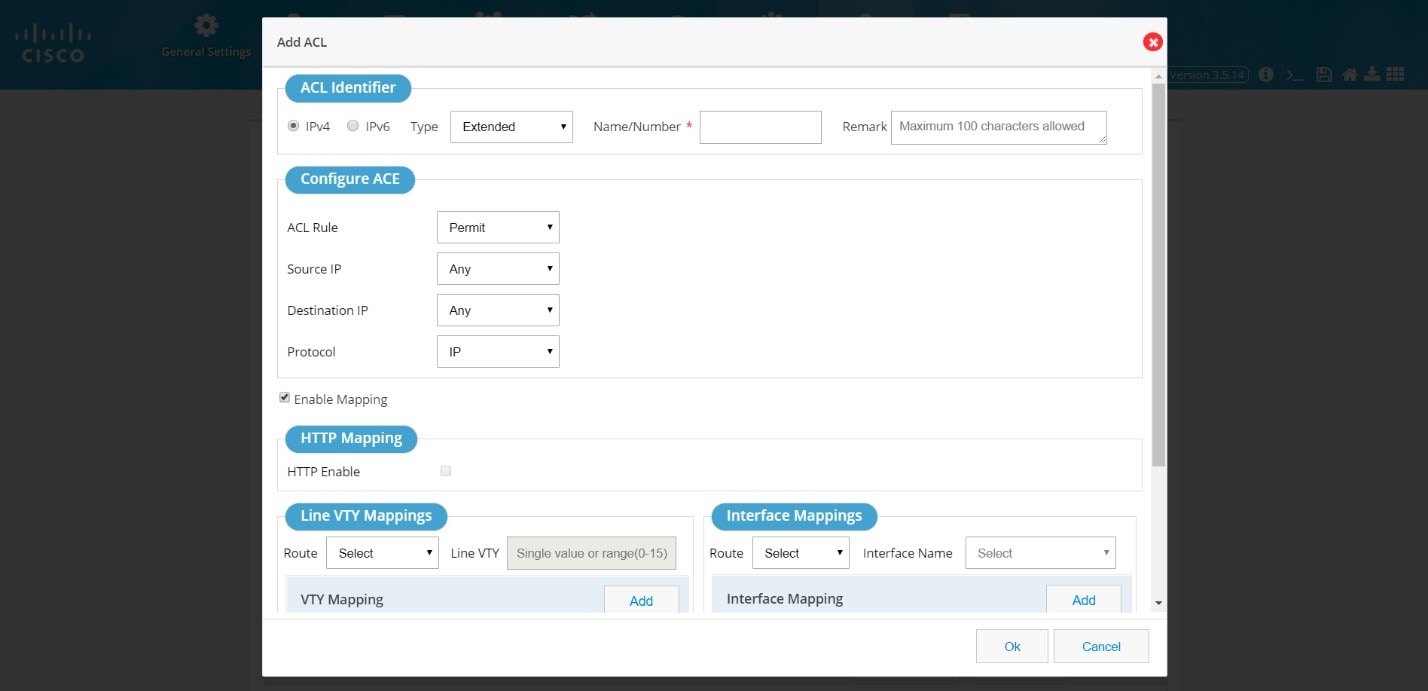 2.
2.
Select the standard option from the Type menu and provide an ACL Name/Number (0-99 for standard).
3.
Select the ACL Rule to permit or deny.
4.
Select the IP address option with either ‘any’ or ‘valid IP address and wildcard Mask’.
You can also add mappings while adding the ACL through this window.
Add an Extended ACL
1.
From the Summary screen, click
Add.
2.
Select the extended option from the Type menu and provide an ACL Name/Number (0-100 for extended).
Figure 64 Add an Extended ACL
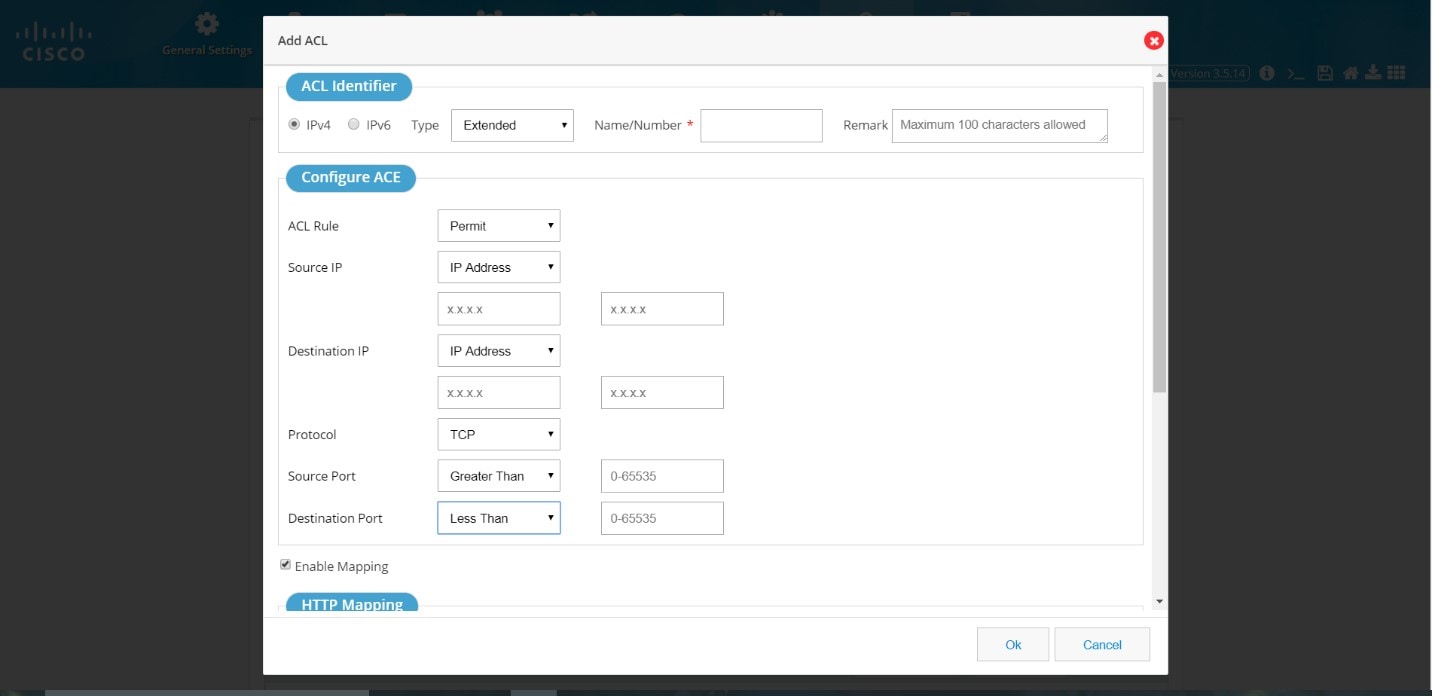 3.
3.
Select a protocol. For TCP/UDP, select the source port and destination port from the lists.
Map an ACL
To map an ACL:
1.
Select the ACL, and click Map ACL. Existing mapping values are listed under one ACL.
Figure 65 Map ACL
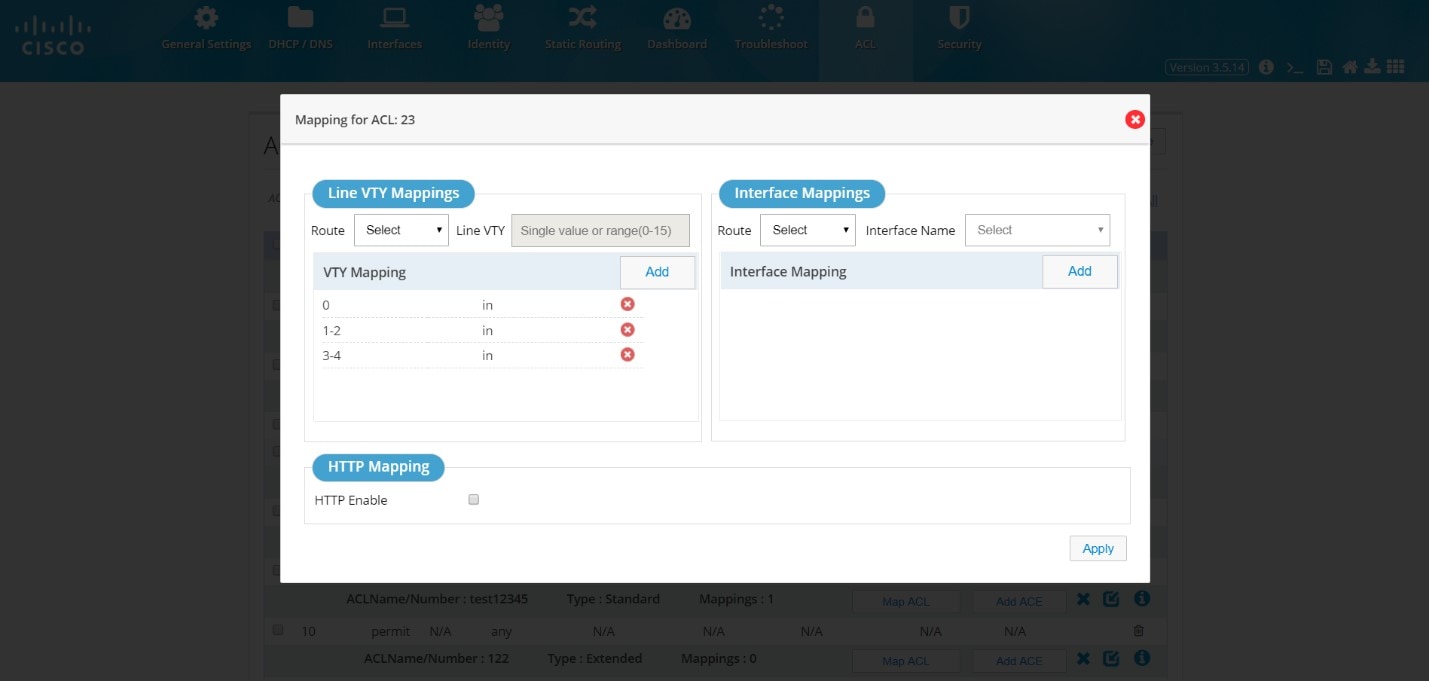 2.
2.
Select Interface and add its route.
or
Select the VTY route, and add the VTY value.
Note: HTTP option will be enabled only for Standard numbered ACL.
Add an Access Control Entry (ACE)
To add an ACE, click the ACE.
Figure 66 ACE
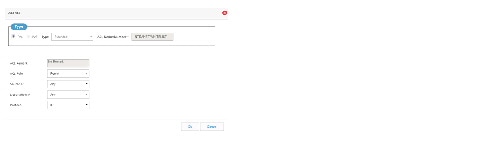
IOx
Use this option to access IOx services through the local management interface.
If IOx is not configured on the router, the following message displays:
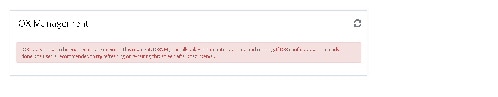
After you configure IOx on the router, select IOx from the Home menu.
Depending on your configuration, you can access IOx Manager through LAN or WAN.
Click either option to launch the Local Manager.
Figure 67 IOx Management

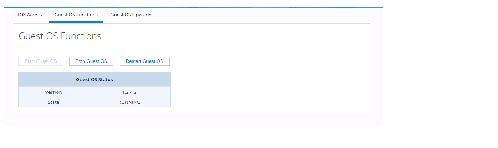
Guest OS Functions
Use this window to start, stop, or restart Guest OS
Figure 68 Guest OS Stopped

Figure 69 Guest OS Start
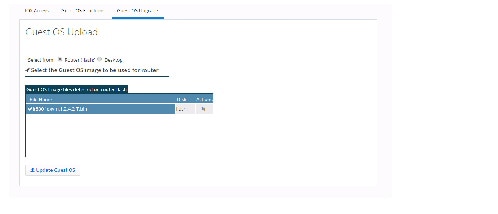
Guest OS Upgrade
1.
Click IOX from the main menu.
2.
Select the Guest OS Upgrade tab to view the existing Guest OS images on the device.
3.
To upload a Guest OS image, click the Desktop option.
Figure 70 Guest OS Upgrade
 4.
4.
Click on the link to download the latest Guest OS version. You are taken to the Cisco.com download page.
5.
Download the recommended latest version for the device.
If you do not have a Cisco.com login, ensure you register.
After you upload the file, the following message displays:
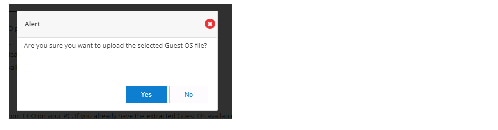 6.
6.
Click Select Guest OS image file, and choose the Guest OS file from the folder in which you downloaded it.
7.
Click on Upload Guest OS File.
 8.
8.
Proceed with the upload of the file to the box by clicking Yes. If the upload fails, click TRY AGAIN.
Once the upload is completed, the
application automatically comes back to the Guest OS Update main page
which lists all the available IOS images on the router.
9.
Choose the Guest OS image you would like to add to the boot list.
10.
Click Update Guest OS to install the new version
Figure 71 Guest OS Upload Completed
For more information about IOx, refer to the IOx documentation at the following URL:
http://www.cisco.com/c/en/us/support/cloud-systems-management/iox/tsd-products-support-series-home.html
Wireless
Wireless configuration is done through the Wi-Fi Manager which is external to CCP Express.
When you click Wi-Fi, you receive the following message with a link to Wi-Fi Manager:
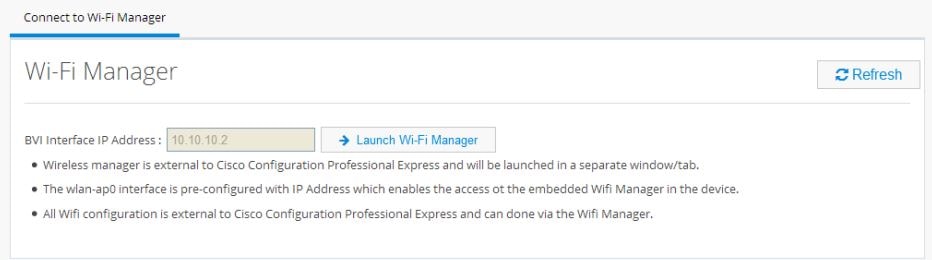 1.
1.
Click
Launch Wi-Fi Manager.
2.
Select Network Configuration under the Easy Setup menu.
Figure 72 Wi-Fi Manager (External to CCP Express)
For more information about configuring
access points, refer to the Cisco IOS Configuration Guide for
Autonomous Aironet Access Points documentation at:
http://www.cisco.com/c/en/us/td/docs/wireless/access_point/15_2_4_JB/configuration/guide/scg15-2-4-Book.html
3.
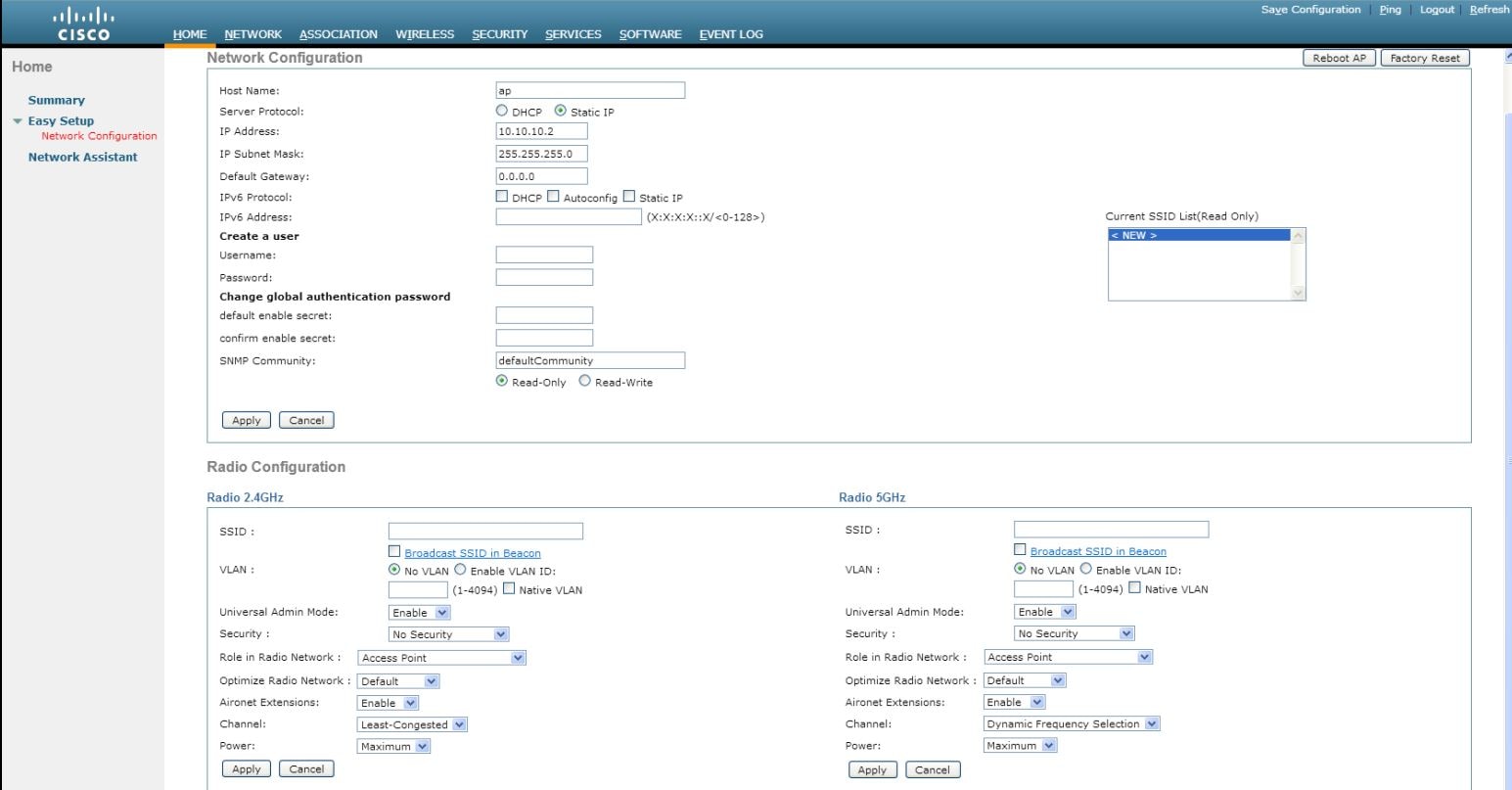
Specify an SSID that will be used to uniquely identify your wireless device.
The SSID can contain up to 32 alphanumeric characters.
4.
To broadcast the SSID in the access point beacon, check the Broadcast SSID in Beacon check box.
When you broadcast the SSID, devices that do not specify an SSID can
associate with the access point. This is a useful option for an SSID
used by guests or by client devices in a public space. If you do not
broadcast the SSID, client devices cannot associate to the access point
unless their SSID matches this SSID. Only one SSID can be included in
the access point beacon.
5.
Select the Enable VLAN ID and specify the ID of the VLAN.
This will enable the clients that connect to the SSID to use the IP addresses from the DHCP pool associated with this VLAN.
6.
Select the security setting for the SSID.
■

Static
WEP Key: choose the WEP key index and key size, and enter the static
WEP encryption key. The key index can be between 1 and 4. The key size
can be either 40 bits or 128 bits.
■

WPA2: specify the WPA2 encryption key and select the key type. The Key type can be either ASCII or Hexadecimal.
7.
Click Apply.
The SSID appears in the SSID table on the bottom of the page.
Zones
Zones establish the security borders
of your network. A zone defines a boundary where traffic is subjected to
policy restrictions as it crosses to another region of your network.
ZFW’s default policy between zones is deny all. If no policy is
explicitly configured, all traffic moving between zones is blocked.
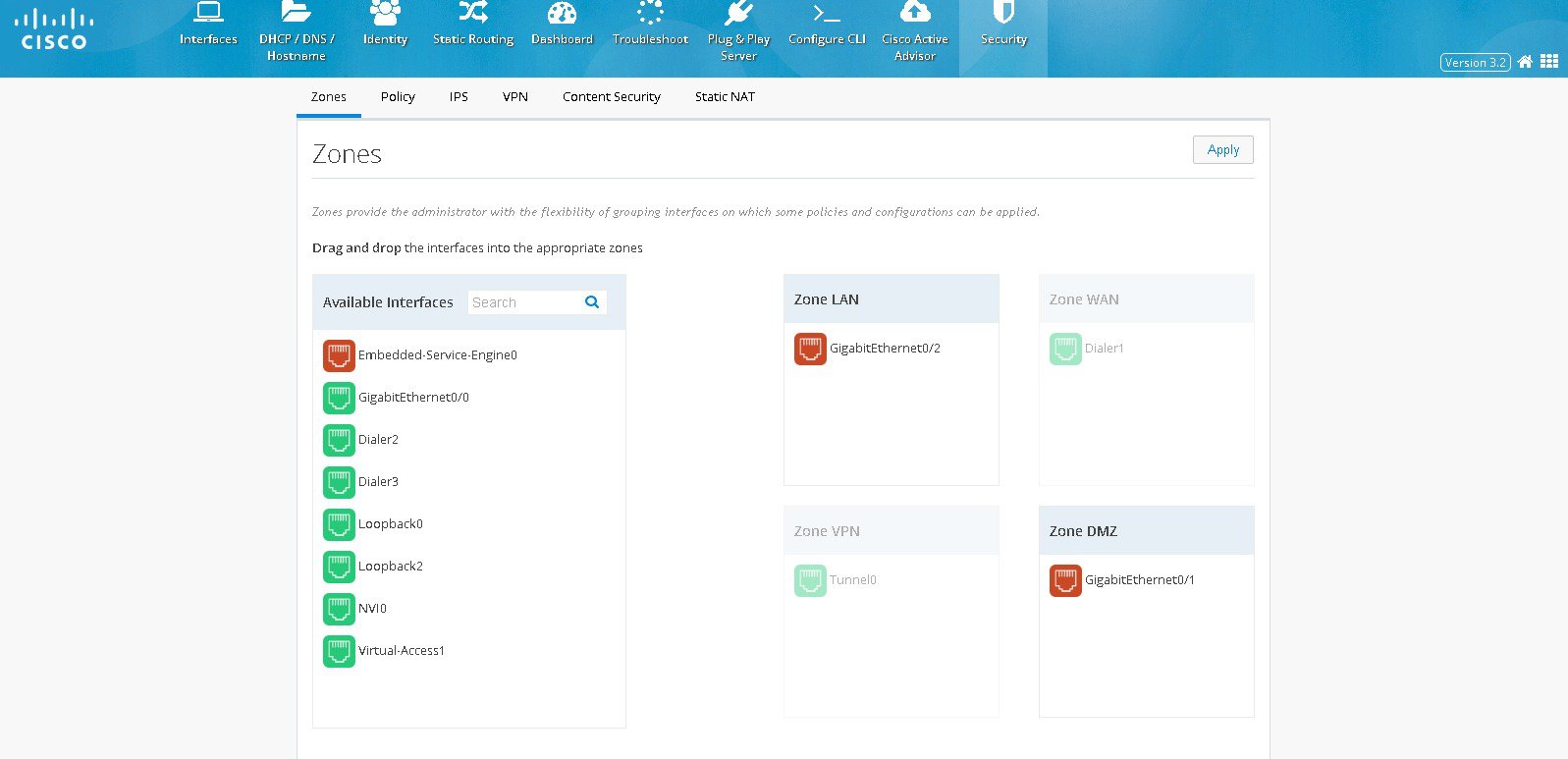
■

Click
Security > Zones. The left side list shows the list of available
interfaces which can be moved to appropriate security zones. The
supported zones are WAN, LAN, VPN, and DMZ.
■

If
any interface needs to be moved to any security zone, it can be just
dragged and dropped into the zone. WAN and VPN zones are grayed out here
and moving the WAN interface under WAN zone can be done in interface
screen. Also when VPN is configured, the respective Tunnel interface
will be moved to VPN zone internally.
Figure 73
The Zones Page
Policy
With the Zones and Policy pages
configured, users can enable Zone based Firewall on the device. Policy
page applies user-defined rules or policy on the traffic that flows
between source and destination zones. The source and destination zones
are tied together to make a zone pair under which the policy is applied.
Prior to creating and applying policy, user needs to configure and
assign the interfaces under the right zones.
Policy feature provides more
granularity in identifying and filtering the traffic. Within the traffic
between source zone and destination zone, the user can filter the
traffic further based on the source and destination network, application
type, the source and destination ports, domains, and the user groups.
Policy Summary
To view the policy summary, perform these steps:
1.
Click Security >Policy to display the summary screen of Policy. The
summary screen lists all existing policies and option to add, edit and
delete an existing policy
–

The
Policy display in the summary screen is based on the zone pairs. For
e.g in the picture below there are two groups of policies and the groups
based on zone pairs viz. LAN-WAN and LAN-VPN
–

The
order of policies can be changed by just dragging and dropping the
policies within the zone pair section table. The changes can be reverted
by clicking the arrow icon placed on top of the zone pair section
Figure 74 The Policy Page
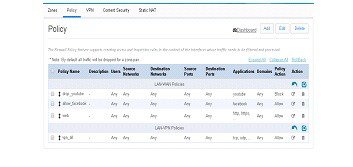
Prerequisite for Creating Any Policy
■

Prerequisite for creating a policy is assigning the specific interfaces to Zones.
■

Provide Zone link here
Some sample use case scenarios are explained below
Block a Specific Application
To block a specific application, perform these steps:
1.
Click Security > Policy, and click Add. The Policy Dialog appears.
2.
From the Policy Dialog, provide Policy Name, description, and the
source and destination zones whose traffic needs to be processed. Also,
the action needs to be taken on the selected traffic whether we need to
block it or allow it.
3.
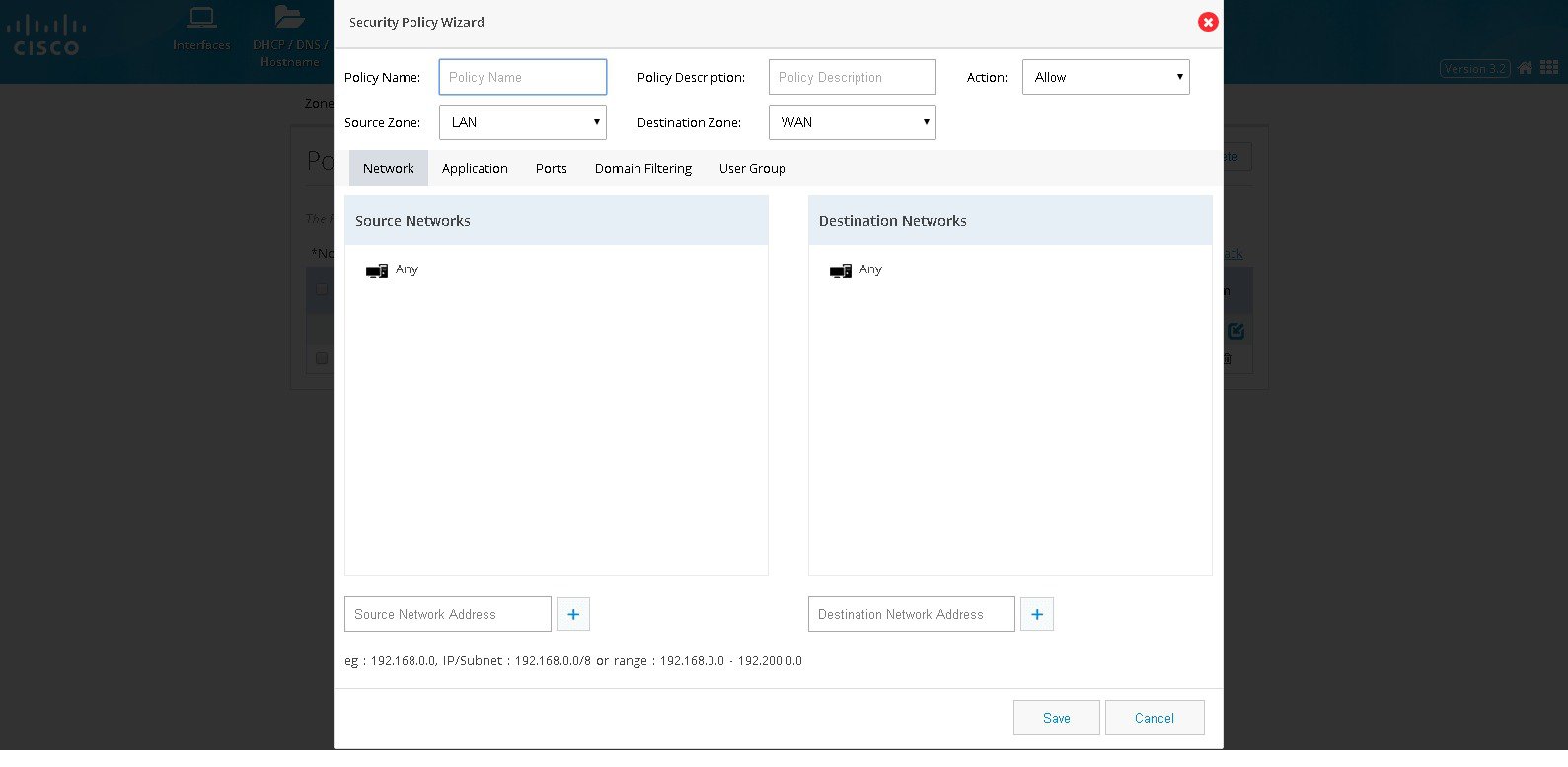
Click Network. Add source and destination network if any specific
network within the zone-pair is to be handled. Add the source network by
specifying the network in the text field and add plus button. The same
procedure needs to be followed for any destination network as well. By
default, source and destination network would be ‘any’.(
The Security Policy Wizard (Landing screen with Network tab contents))
Figure 75
The Security Policy Wizard (Landing screen with Network tab contents)
 4.
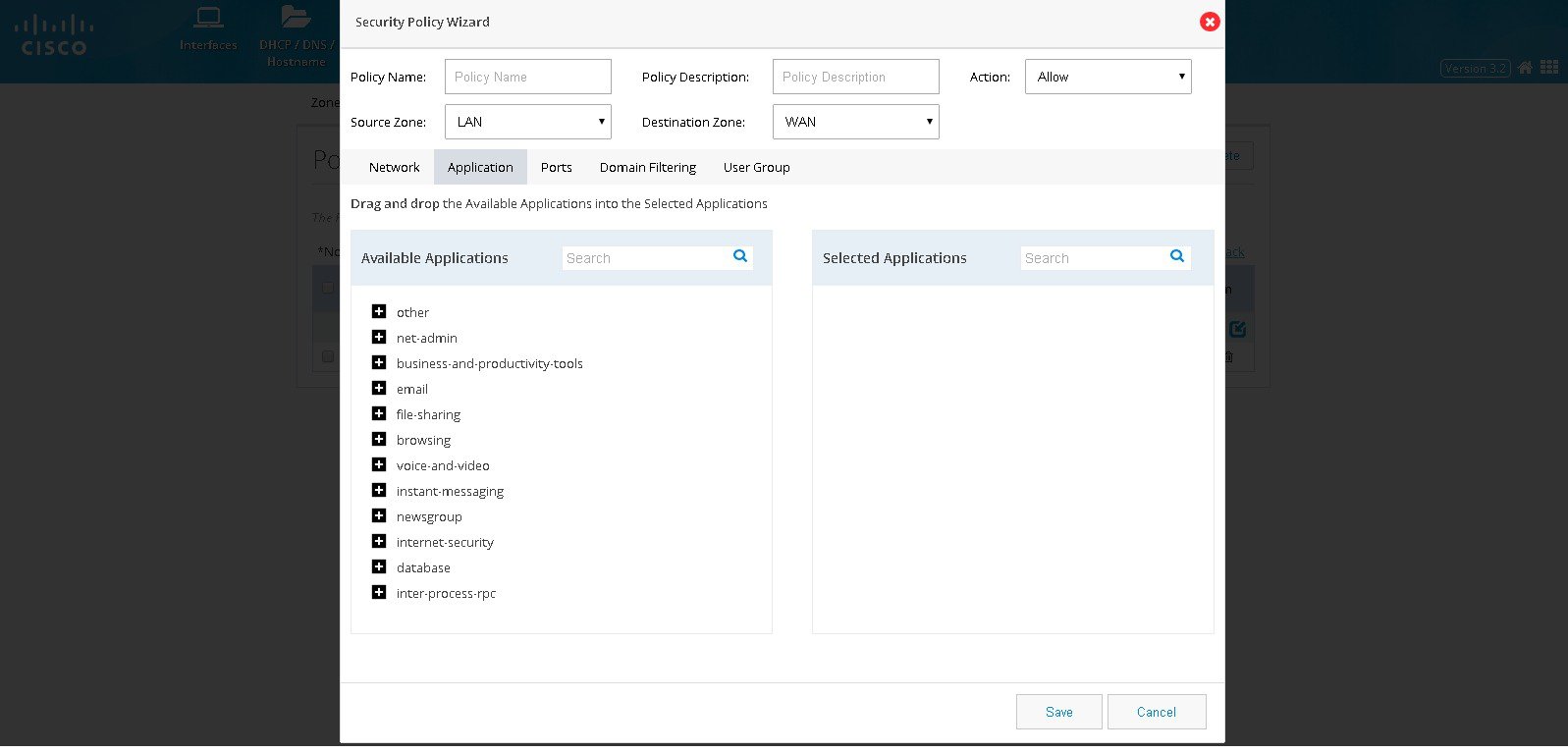
4.
Click Application to select the application to be inspected or blocked.
The Available Applications shows the list of applications grouped as
per the known category. The needed application or group can be dragged
and dropped in the Selected Applications list.
Figure 76 The Security Policy Wizard (Application tab contents)
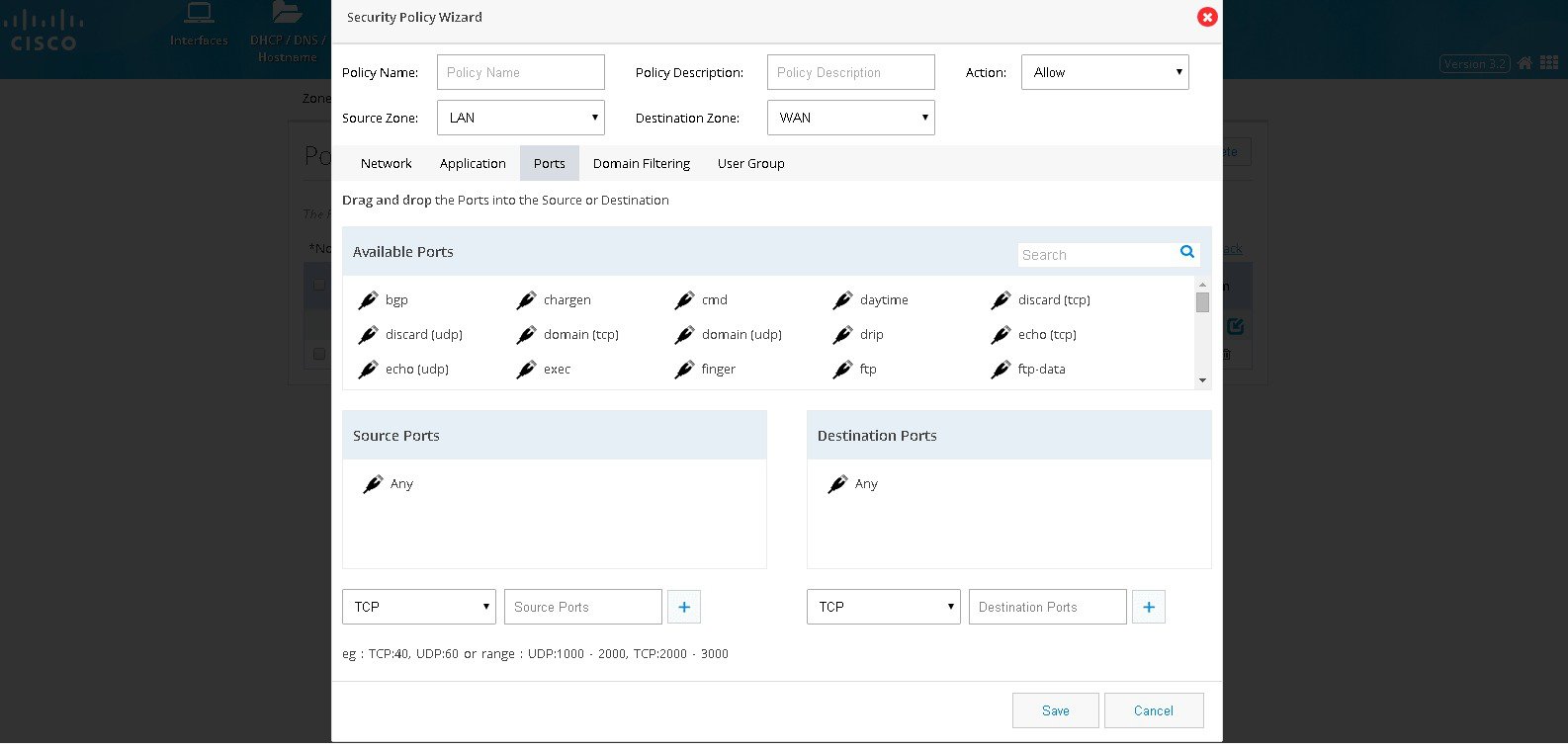
 5.
5.
Click Ports if it is required to classify the application based on
source and destination ports. By default, traffic originating from any
ports of the selected networks will be processed. User can add a
required source and destination ports. List of popular applications is
given based on their Category and by dragging and dropping the needed
one will handle the port specific to that.
Figure 77 The Security Policy Wizard (Ports tab contents)
 6.
6.
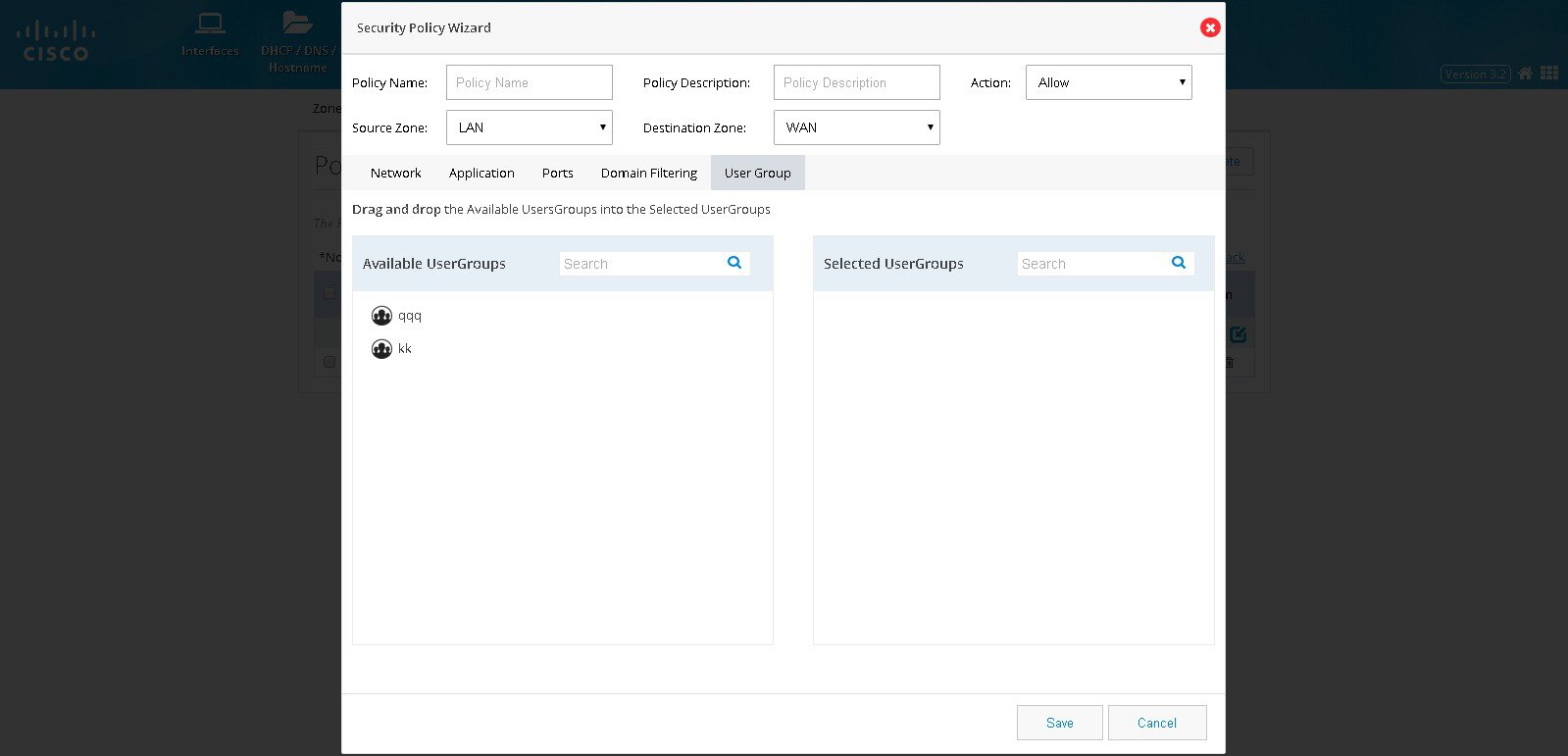
Click User Groups if the traffic filtering is to be handled based on the user or group originating the traffic.
Figure 78 The Security Policy Wizard (User group tab contents)
Block a Specific Domain
To block a specific domain, perform these steps:
1.
Click Security > Policy, and click Add.
2.
Policy Dialog will appear. Provide Policy Name, description, and the
source and destination zones whose traffic needs to be processed. Also
the action needs to be taken on the selected traffic whether we need to
block it or allow it.
3.
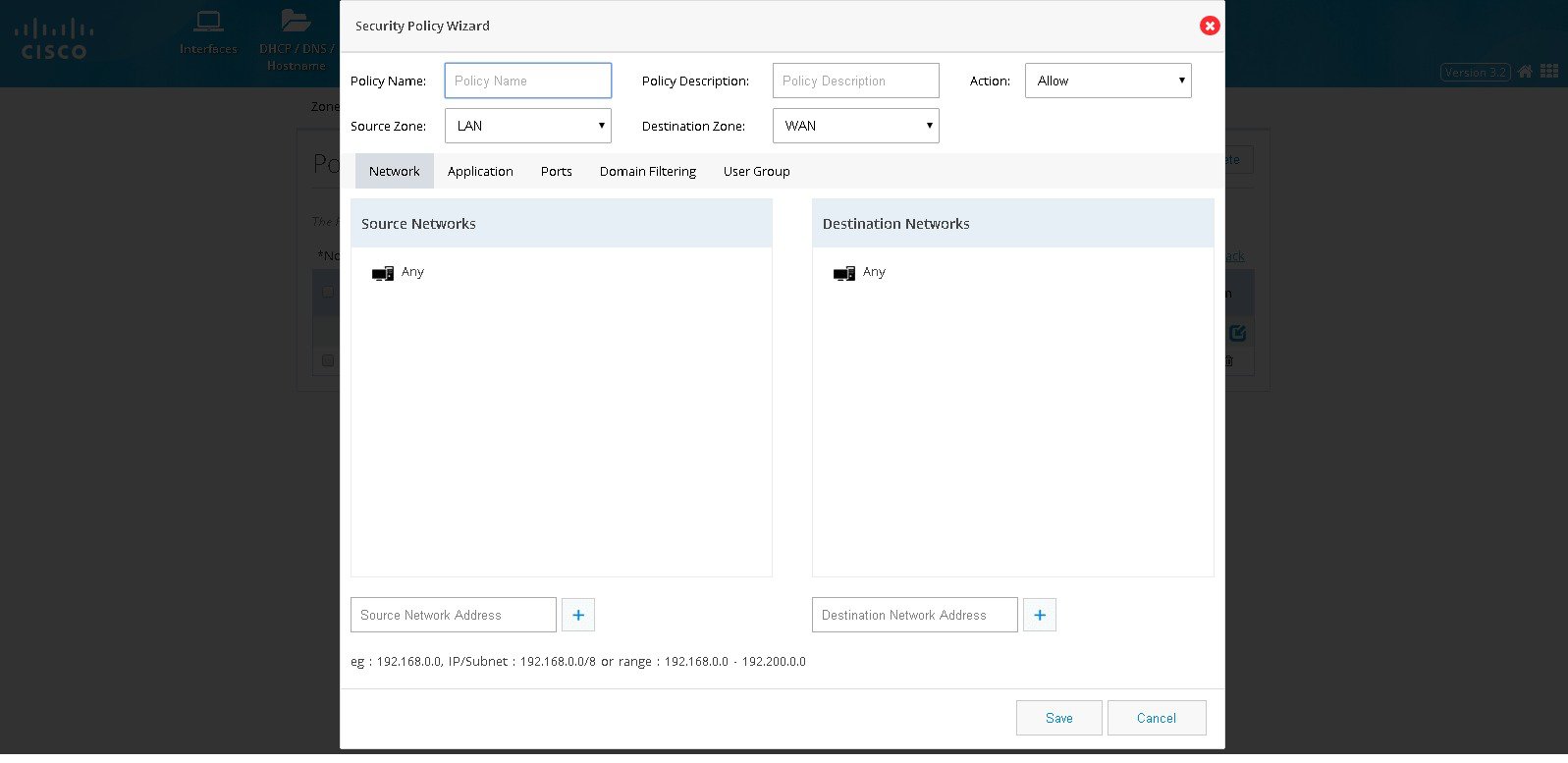
Click Network. Add source and destination network if any specific
network within the zone-pair is to be handled. Add the source network by
specifying the network in the text field and add plus button. The same
procedure needs to be followed for any destination network as well. By
default all the networks in the Zone pair is processed.
Figure 79 The Security Policy Wizard (Landing screen with Network tab contents)
 4.
4.
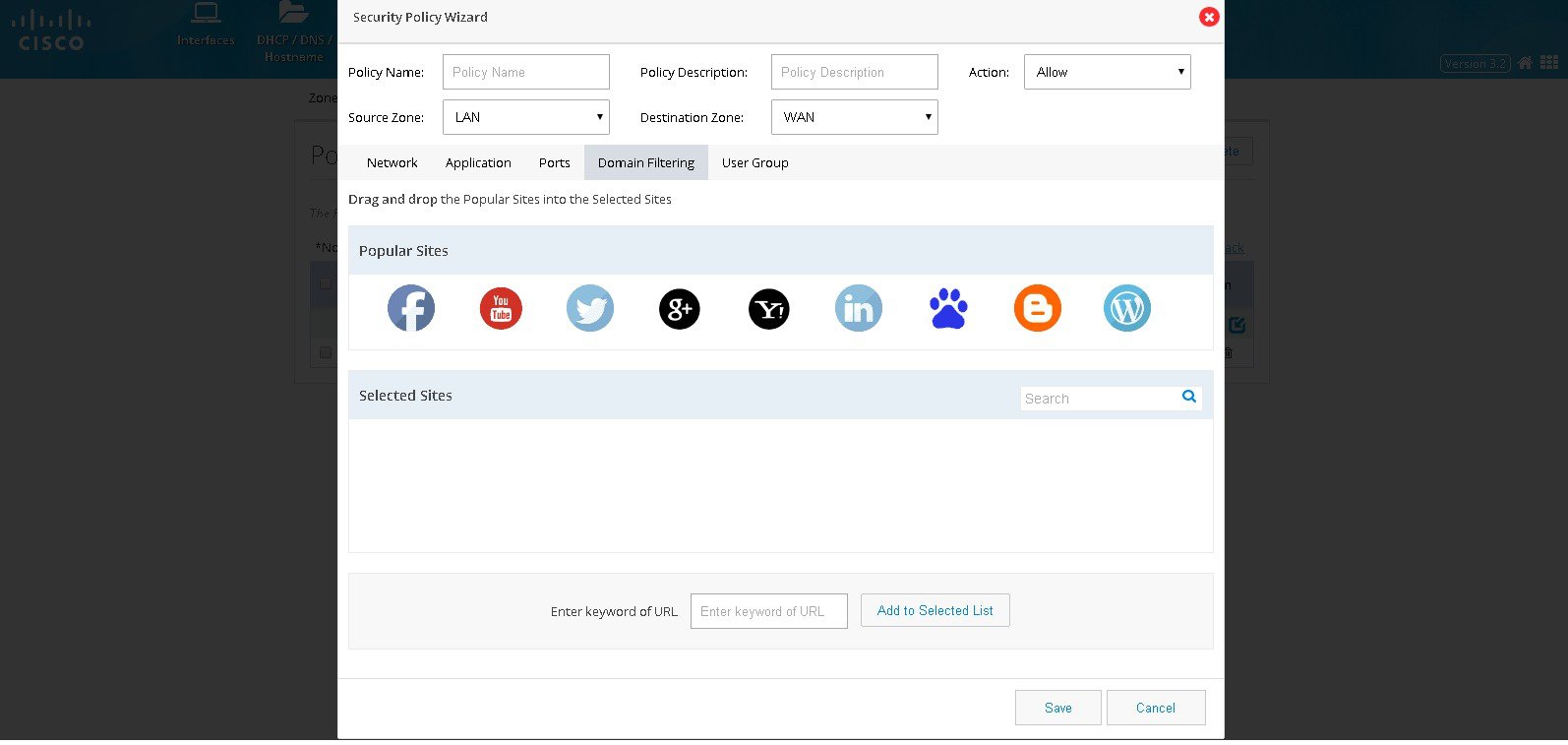
Click Domain Filtering and the screen shows list of popular sites. User
can drag and drop if any of the popular websites need to be blocked. If
any unlisted domain needs to be added that URL (wild card pattern
accepted) can be given in the text box.
Figure 80 The Security Policy Wizard (Domain Filtering tab contents)
 5.
5.
Click User Groups if the traffic filtering is to be handled based on the user or group originating the traffic.
Note: To select the specific User group it should have been already added through the Identity feature.
IPS
Cisco IOS Intrusion Prevention System
(IPS) is an inline, deep-packet inspection feature that effectively
mitigates a wide range of network attacks. A component of the Cisco IOS
Integrated Threat Control framework and complemented by Cisco IOS
Flexible Packet Matching feature, Cisco IOS IPS provides your network
with the intelligence to accurately identify, classify, and stop or
block malicious traffic in real time.
Prerequisites for Using IPS
■

Ensure the IPS Signature Packages are present on the router under flash:
■

Enable Security License on the router.
■

Complete WAN interface configuration.
If these conditions are not met, respective error messages are displayed when the IPS feature is accessed.
Enabling IPS
If all the prerequisites are met, you receive the option to enable IPS.
1.
Click Security > IPS, and choose the Enable IPS check box.
2.
When you enable IPS for the first time, a popup window lists all of the
IPS Signature Packages available on the box. The first one is selected
by default. Even if there is only a single package, you get this dialog
box.
Figure 81 IPS Signatures
 3.
3.
Select appropriate one and click OK.
4.
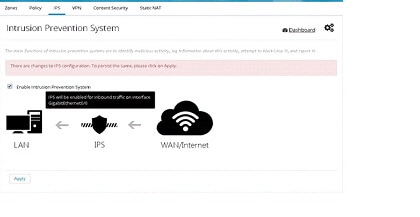
You get the message that there are changes to IPS configuration. Upon
applying the changes, IPS is enabled on inbound traffic (depicted in the
image below the check box). The selected signature package is compiled
and applied too. To view the interface(s) on which this will be applied,
hover on the image to view the tool tip containing that information.
Figure 82 Intrusion Prevention System Page
 5.
5.
Click on the Apply button to persist changes. You have to wait for a
minute (depending on the signatures selected) as the signature
compilation is occurring in the background.
6.
After the settings are applied and the signature compilation is
completed, the IPS screen with the information on the package version
and count of failed signatures (if any) is displayed.
Note: For all further
disable/enable cycles, you are not prompted to select the package. In
those cycles, after enabling, you get a message that “Signature
compilation is in progress”. You can choose to visit other pages and
come back later or to hit “Refresh” after a while to see the IPS
settings screen.
Disabling IPS
To disable IPS at any point, uncheck the Enable IPS check box and click Apply.
Uploading IPS Signature Packages
You have the option to upload
signature packages onto the router at any point in time. To upload IPS
signature packages, perform these steps:
1.
Hover your cursor over the Configure icon that is available on the right pane. The settings menu appears.
2.
Click on the Upload IPS Signature Packages option. A dialog box appears.
3.
Click on the Folder button and select the file from the file selection dialog box and click OK.
CCP Express validates for the file
name, duplication and free space on the router. If any of these
validations fail, appropriate error message are displayed. If the file
validations are completed, you receive the message that file is ready
for upload and the “Upload” button is enabled.
4.
Click on the Upload button to initiate the upload.
Upload takes a while as the file size
is around 20MB. You are notified when the upload is completed. You can
upload more files or quick the dialog.
Changing IPS Signature Packages
When IPS is enabled, if the box has
more than one Signature Package file, you are provided with an option to
change the signature package. To change IPS signature packages:
1.
Hover your cursor over the Configure icon that is available on the right pane. The settings menu appears.
2.
Click on the Change IPS Signature Packages option.
A dialog box with the list of
available packages on the box is displayed. The currently selected one
is listed, but selection is disabled for this one. The packages are
sorted in reverse alphabetical order to have the latest one at the top
for easy selection.
3.
Select the package of your choice and click OK. Signature compilation may take several seconds.
4.
After the settings are applied and signature compilation is completed,
the IPS screen with the information on the newly selected package
version and count of failed signatures (if any) is displayed.
Download Link for IPS Signature Packages
You can download the relevant
signature package files from the link that is shared with you. This is a
link that connects you to an internal CISCO page. To download IPS
signature package:
1.
Hover your cursor over the Configure icon that is available on the right pane. The settings menu appears.
2.
Click on the Download IPS Signature Packages option. Upon clicking on
the link, you are taken to the CISCO IPS Services page (external to CCP
Express), from where the you can download signature packages that are
needed.
Enabling/Disabling Notifications/Log
You are provided with links to enable
and disable SDEE and syslog notifications. The menu is smart to toggle
between the enable and disable options for each based on the setting in
the system.
SDEE Notifications
To enable SDEE notifications:
1.
Hover mouse on the Configure icon that is available on the right pane. The settings menu appears.
2.
Click on the Enable SDEE Notifications option.
3.
After the setting is applied, the menu item changes to Disable SDEE
Notifications. This is because in the device, it is enabled. If you
click on this option again, it toggles the state on the device as well
as on the menu.
Syslog
Use this section to check the Syslog on the device. This feature is available in CCP Express Release 3.5.2 and later releases.
To enable Syslog:
1.
Click Troubleshoot and navigate to the Log option.
Figure 83 Syslog View
 2.
2.
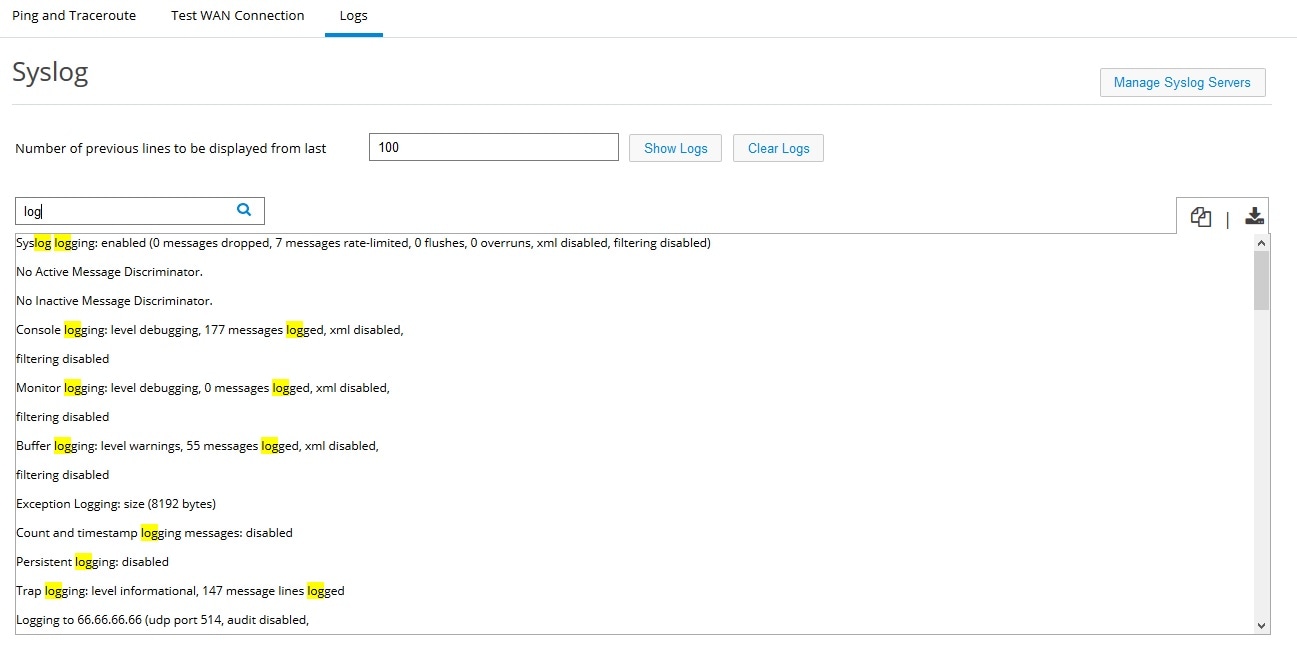
Enter the number of lines to be displayed and click on “Show Logs”.
Once logs are listed user can search for a particular string and all the
occurrences will be highlighted.
Figure 84 Syslog - Show Logs
 3.
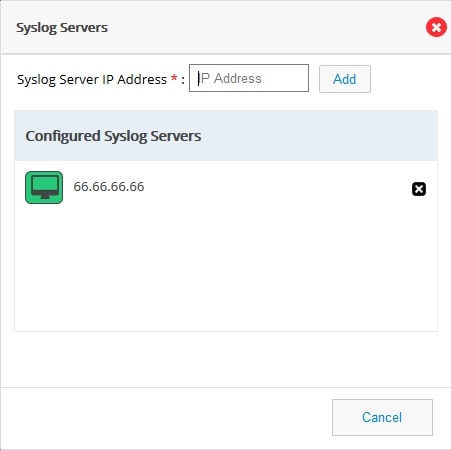
3.
You can also configure Syslog servers.
Figure 85 Syslog Servers
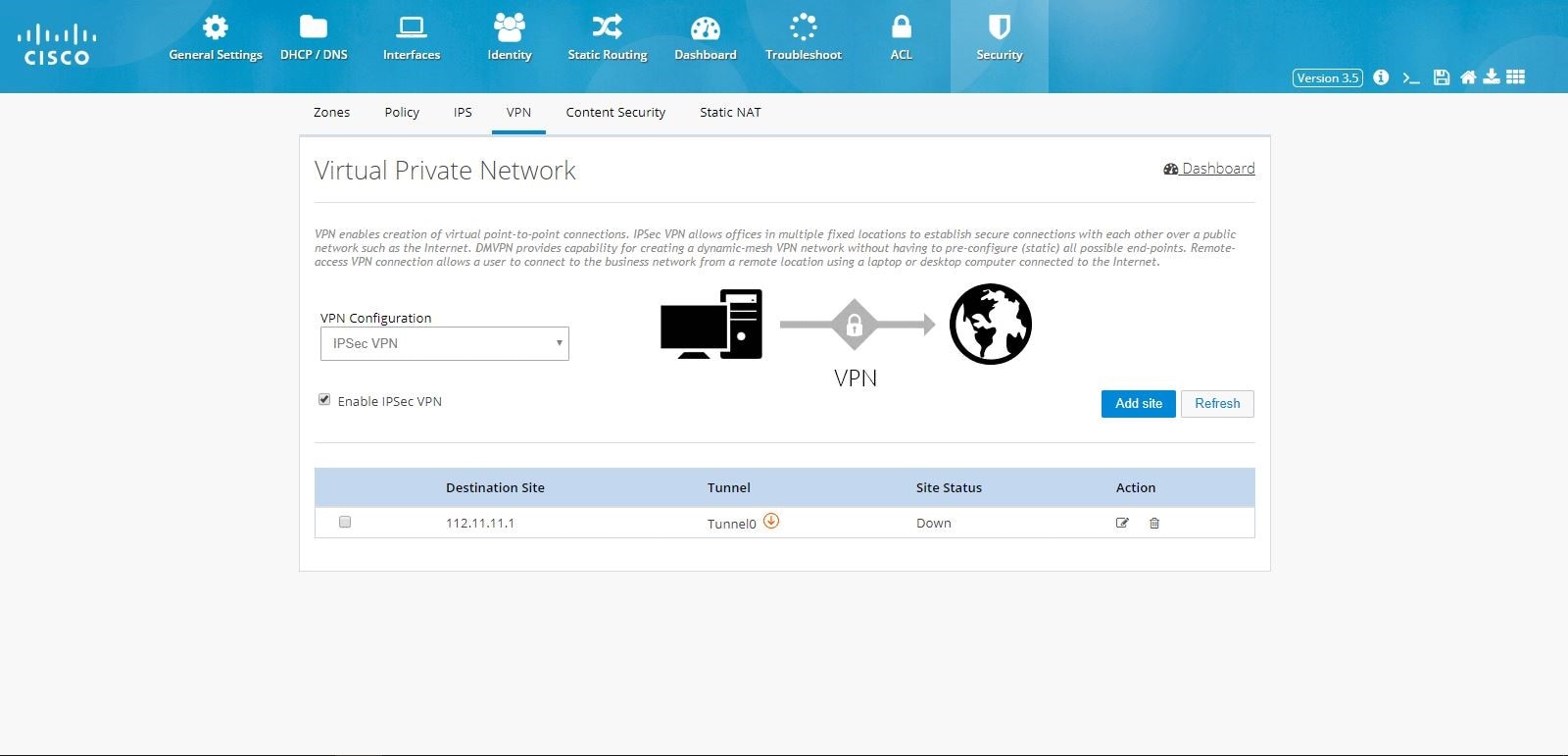
VPN
CCP Express supports creation of IPSec
multi-site VPN configuration, DMVPN spoke side configuration, DMVPN hub
configuration, remote access configuration, a combination of IPSec
multi-site with remote access configurations, and a combination of DMVPN
hub with remote access VPN configurations.
Prerequisite for VPN
Primary WAN interface must be
configured and should be part of WAN Zone. Also, LAN interfaces should
be part of LAN Zone before configuring any VPN.
IPSec Multi-Site Configuration
To configure multi-site VPN:
1.
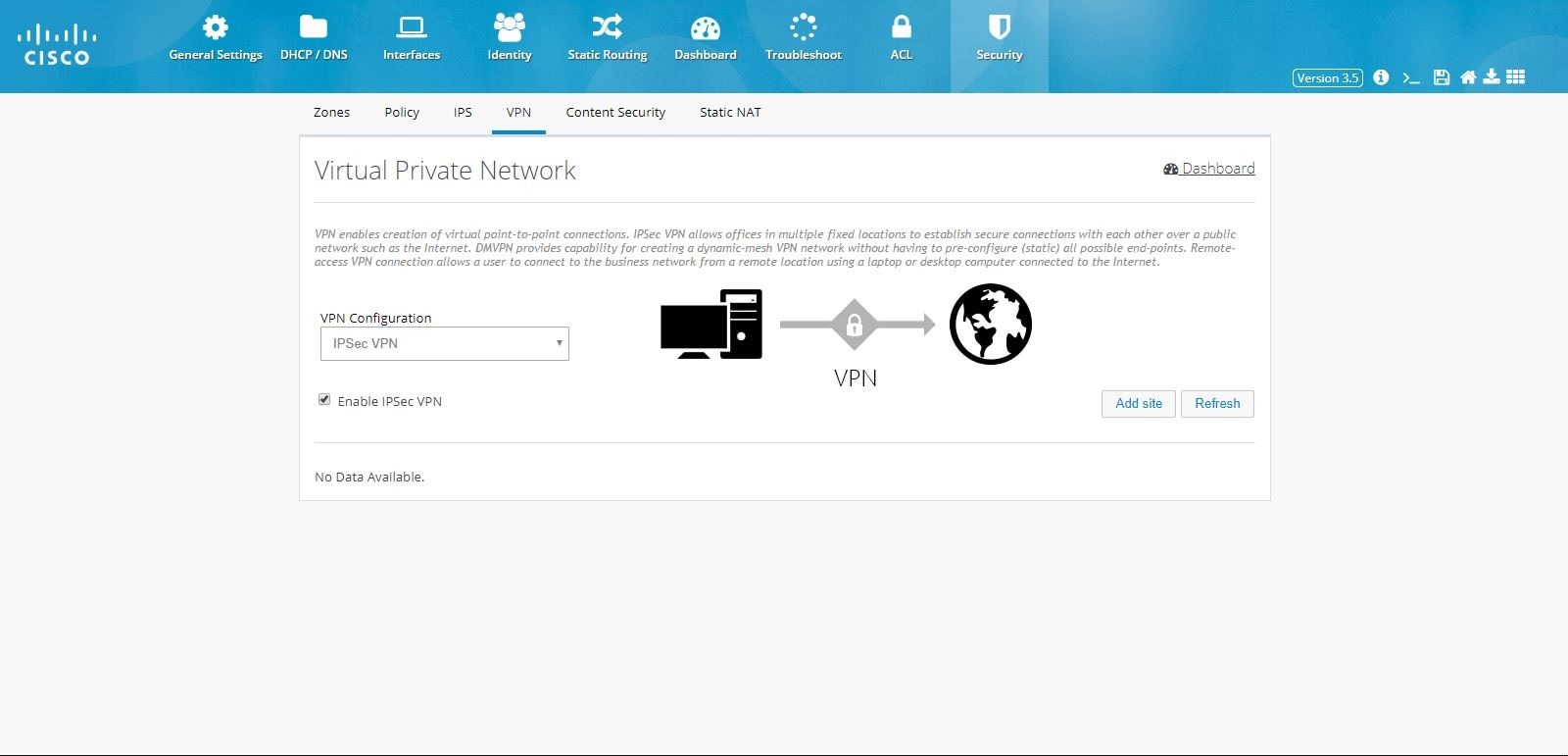
Click Security > VPN and select IPsec option from the VPN Configuration drop-down list.
2.
Click the Enable VPN check box and click Add Site. The VPN wizard is displayed as a popup dialog.
Figure 86 IPSec Multi-Site VPN
 3.
3.
Provide Tunnel IP and Mask for the site being configured.
Figure 87 IPSec Multi-Site VPN (Tunnel Configuration)
 Note:
Note: By default, from configuring site end, all the LAN side networks are allowed to access the other end through VPN tunnel.
4.
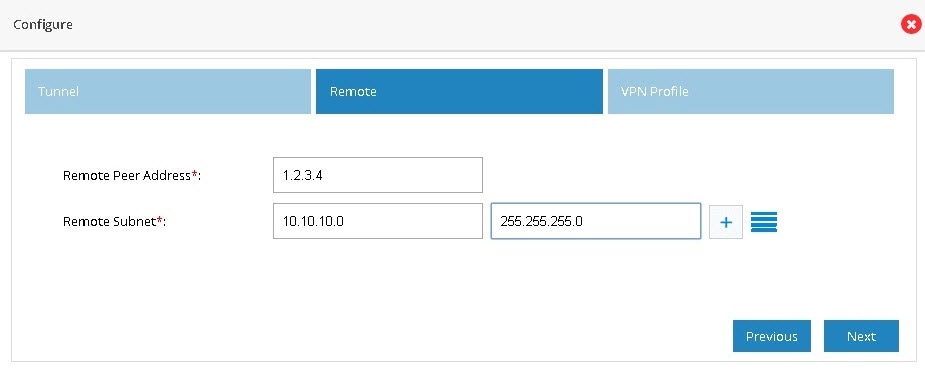
Provide the remote peer address (WAN IP address of the other end).
Figure 88 IPSec Multi-Site VPN (Remote Configuration)
 5.
5.
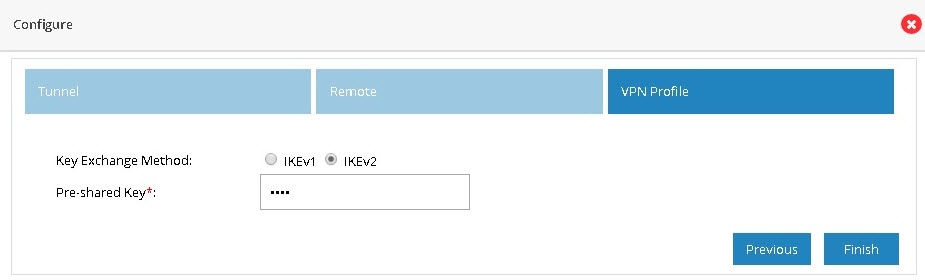
Select an appropriate Key Exchange model (either IKEv1 or IKEv2). By default, IKEv2 is selected and that is recommended.
6.
Provide Pre shared Key.
Figure 89 IPSec Multi-Site VPN (Profile)
 7.
7.
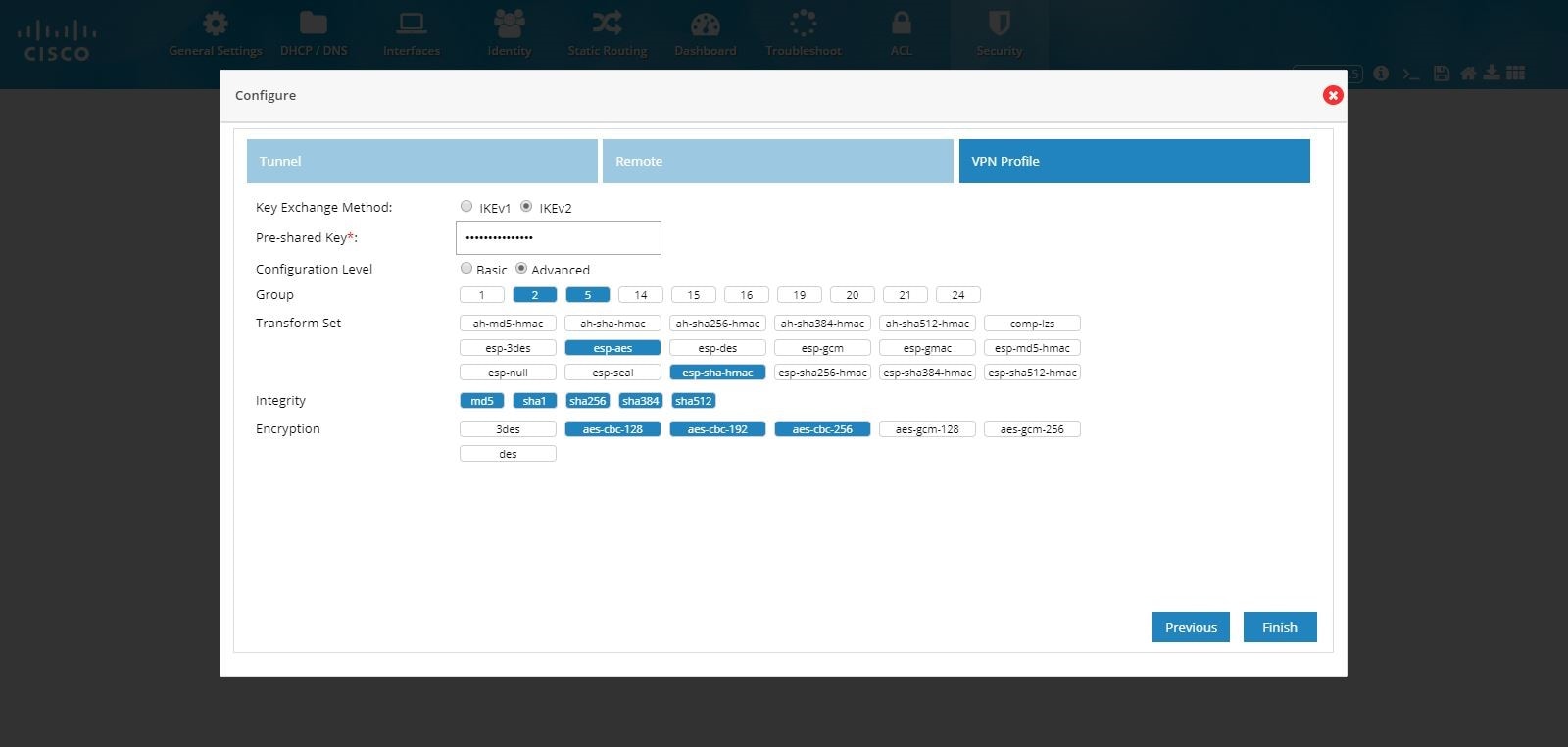
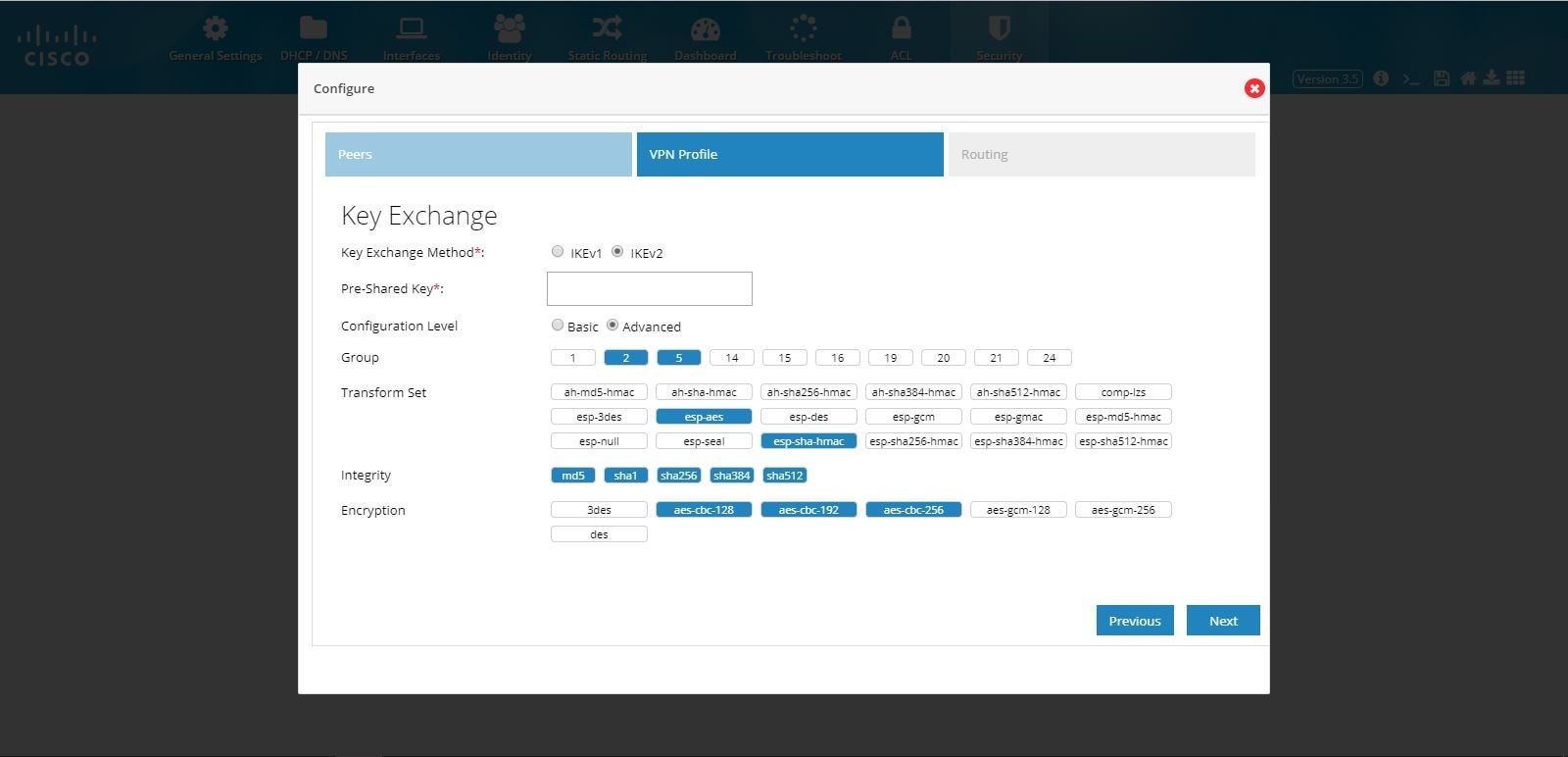
(Optional) Select Advance to manually configure IKE and IPSec parameters.
Figure 90 IPSec Multi-Site VPN (Advanced Options)
 8.
8.
Click Finish.
After the configuration is complete,
the list of sites is displayed. You can choose to add more or delete
sites from the available list.
Figure 91 IPSec Multi-Site VPN (Completed)
 Note:
Note: If CCP Express is used
to configure the Multi-Site VPN, ensure that both the ends are
configured with CCP Express only. CCP Express internally uses the
transform set as esp-aes, esp-sha-hmac and IKEv2 Proposal with
encryption as 3des, integrity as md5 and Diffie Helman group as 2.
DMVPN Spoke Configuration
To enable DMVPN Spoke configuration:
1.
Click Security > VPN and select DMVPN Spoke option from the VPN Configuration drop-down list.
2.
Click Enable DMVPN Spoke check box, and click
Configure.
Figure 92 DMVPN Spoke Configuration
 3.
3.
Provide Tunnel IP, Backup Tunnel IP, and Tunnel Mask for site being configured.
4.
Provide the Remote Tunnel Address (WAN IP address of the other end). You can also provide the FQDN of the Hub device. Click
Next.
Figure 93 DMVPN Spoke Configuration (VPN Peers)
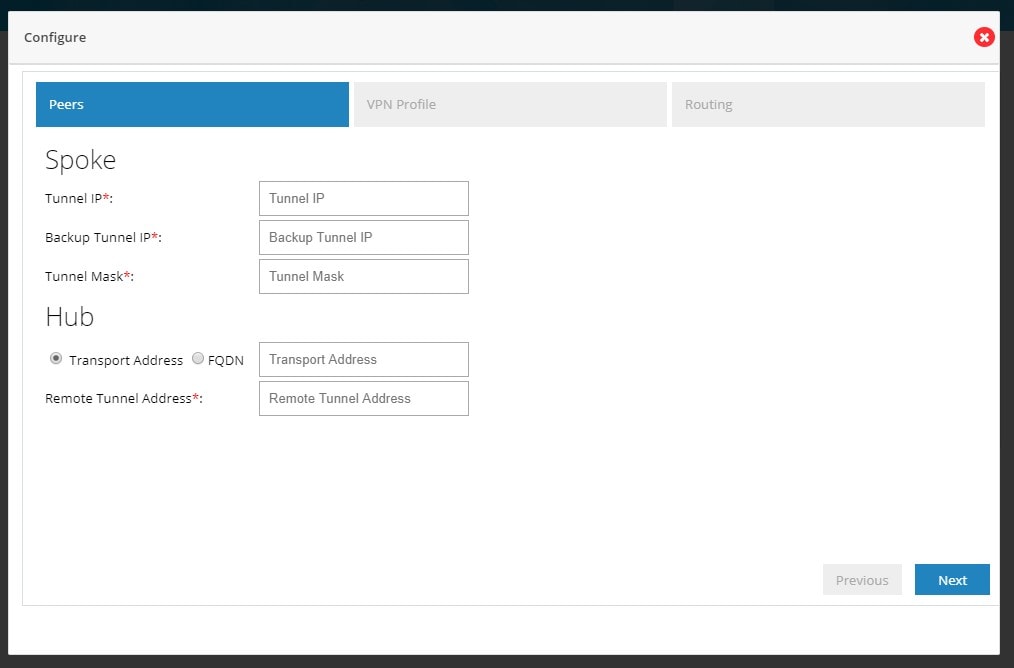
By default from configuring site end all the LAN side networks are allowed to access the other end through VPN Tunnel.
When DMVPN Spoke configuration is
successfully completed, and the Hub is configured and active, the tunnel
will come up between Hub and Spoke.
5.
Select an appropriate Key Exchange model (either IKEv1 or IKEv2). By default, IKEv2 is selected and is recommended.
6.
Provide the Pre-Shared Key.
Figure 94 DMVPN Spoke Configuration (VPN Profile)
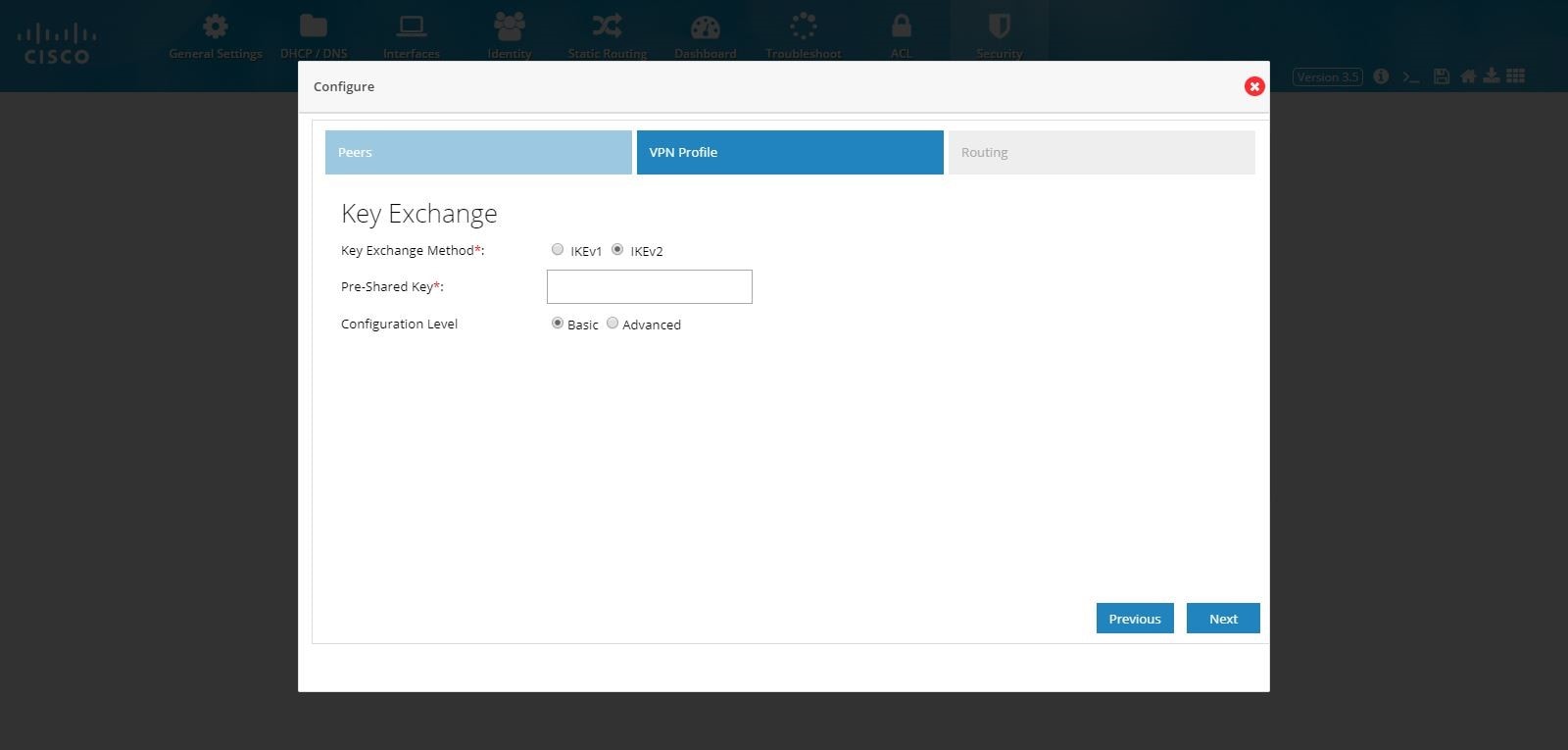
Figure 95 DMVPN Spoke Configuration (VPN Profile Advanced Options)
 7.
7.
Provide an EIGRP Autonomous number in the range of 1–65535.
Figure 96
DMVPN Spoke Configuration (Routing)
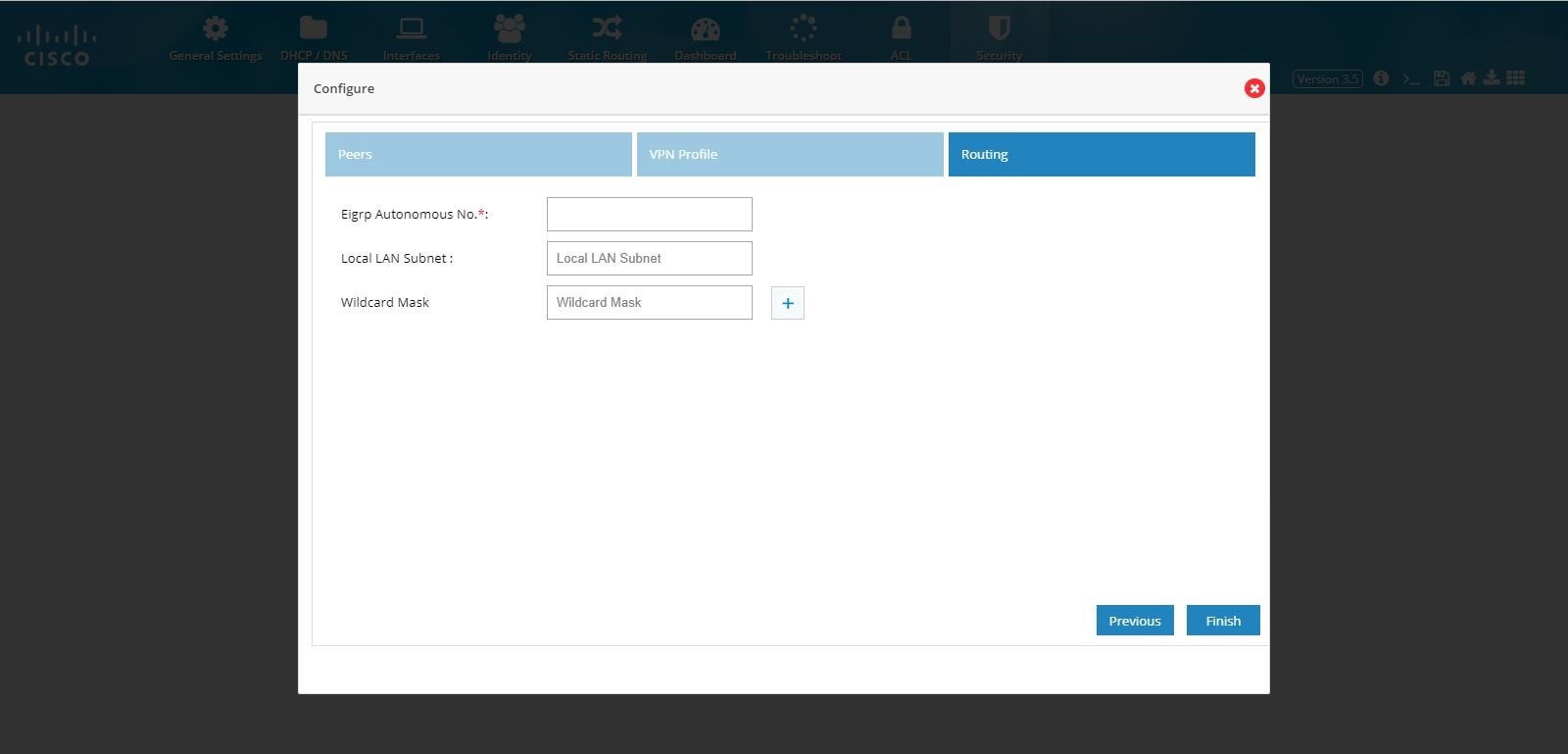 8.
8.
Click
Finish.
Figure 97 DMVPN Spoke Configuration (Completed)
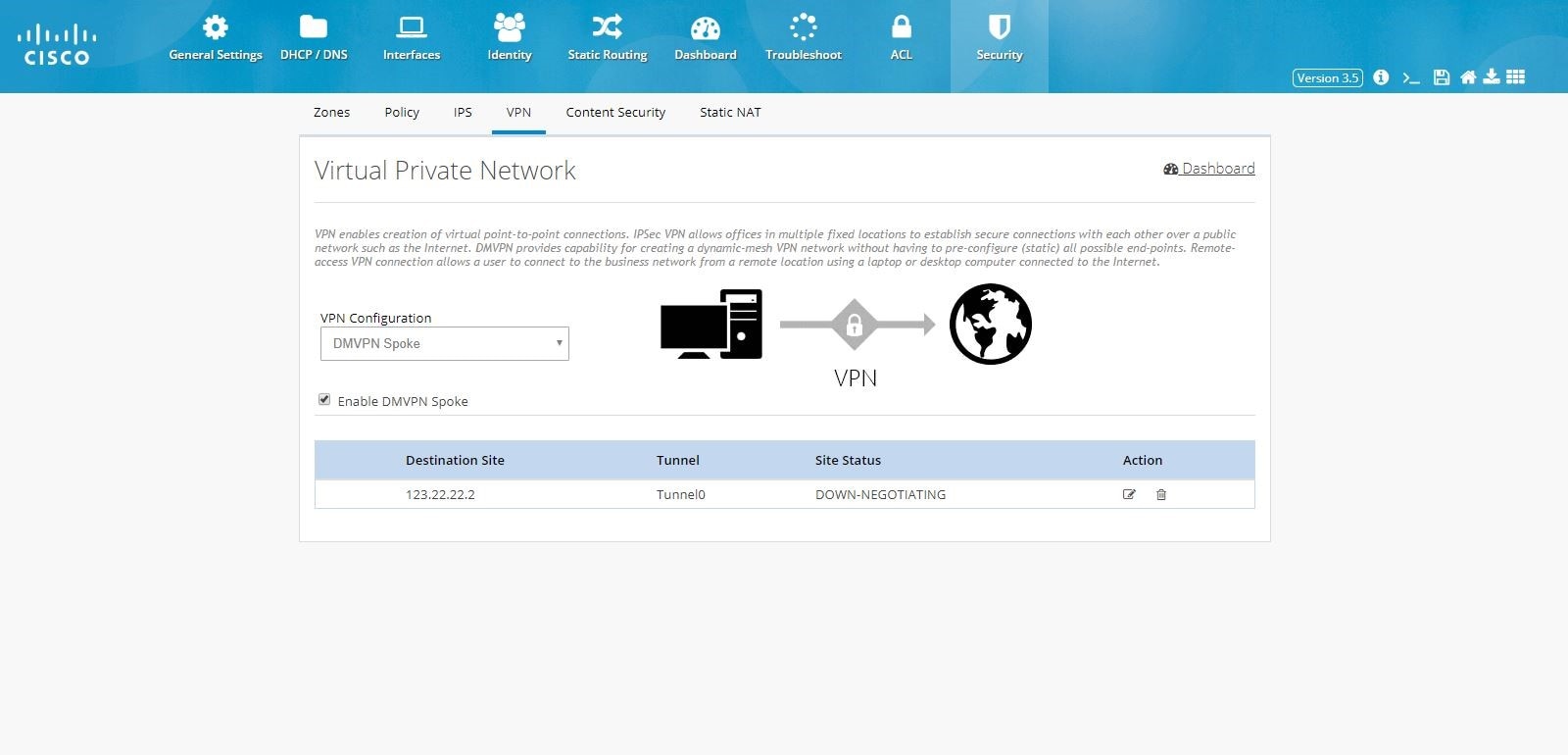
DMVPN Hub Configuration
To configure DMVPN Hub:
1.
Click Security > VPN and select DMVPN Hub option from the VPN Configuration drop-down list.
2.
Click Enable DMVPN Hub check box, and click
Configure.
Figure 98 DMVPN Hub Configuration
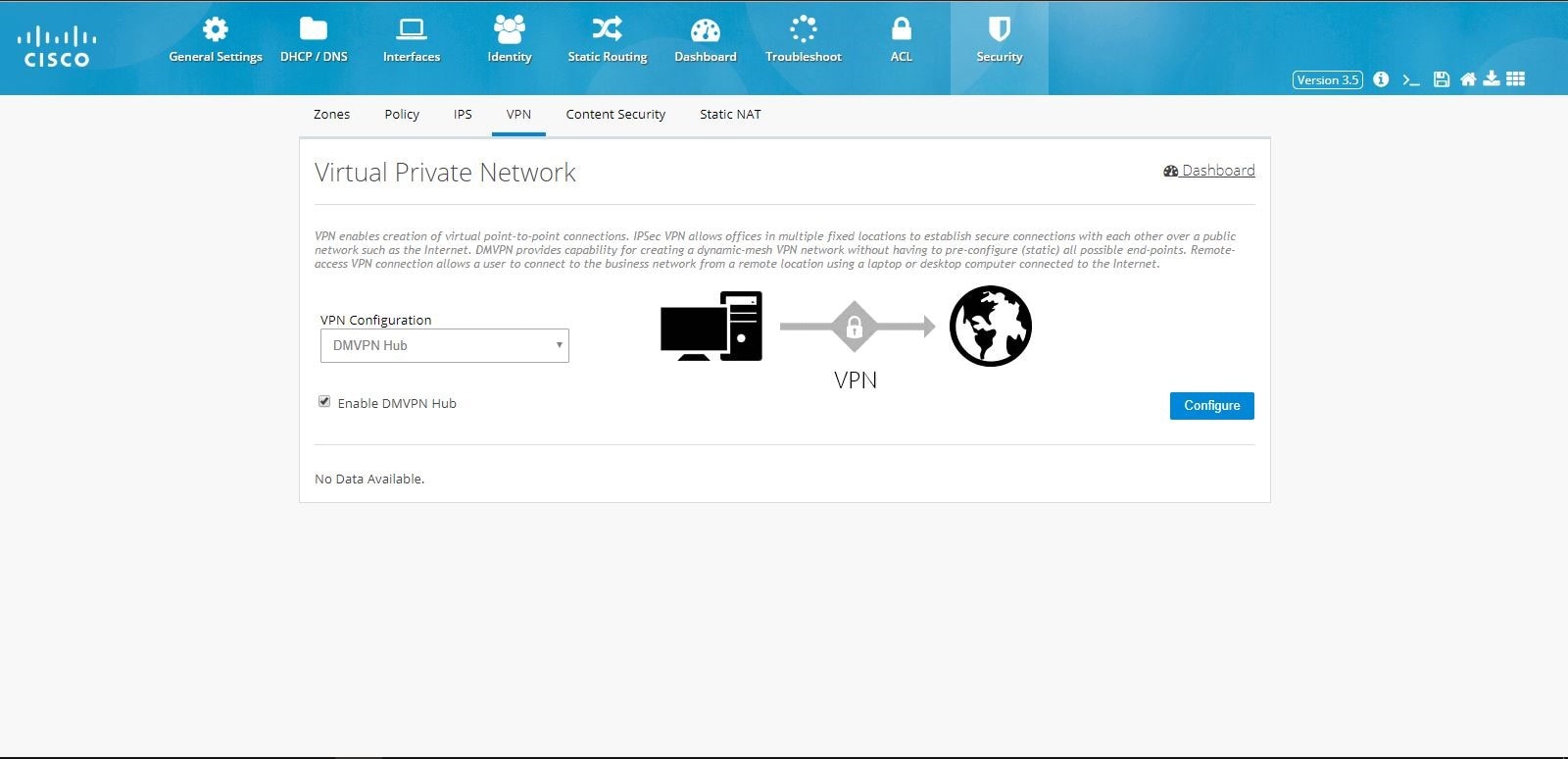 3.
3.
Provide Tunnel IP and Mask for the hub being configured.
Figure 99 DMVPN Hub Configuration (VPN Peers)
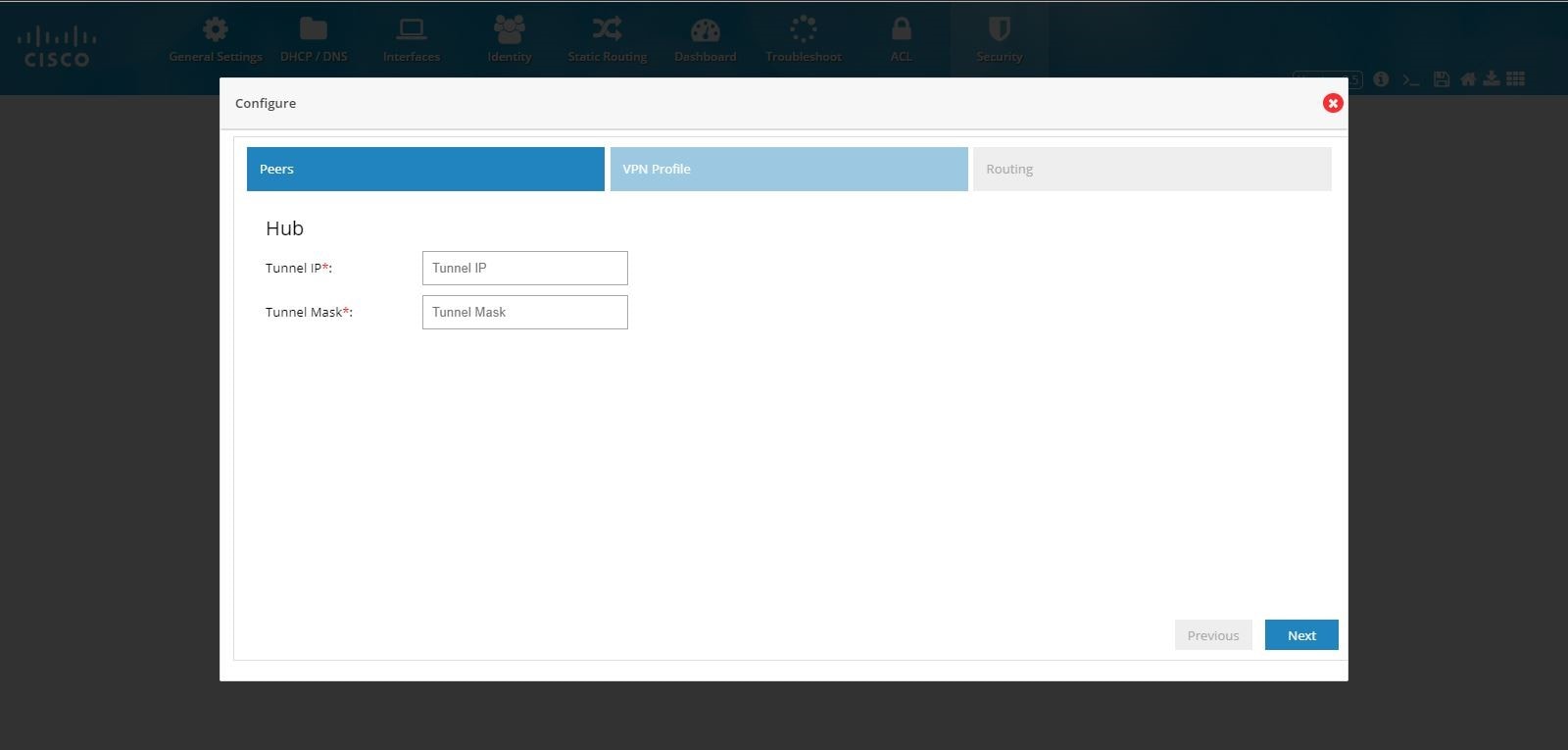 4.
4.
Select an appropriate Key Exchange model (either IKEv1 or IKEv2). By default, IKEv2 is selected and is recommended.
5.
Provide the Pre-Shared Key.
Figure 100 DMVPN Hub Configuration (VPN Profile)
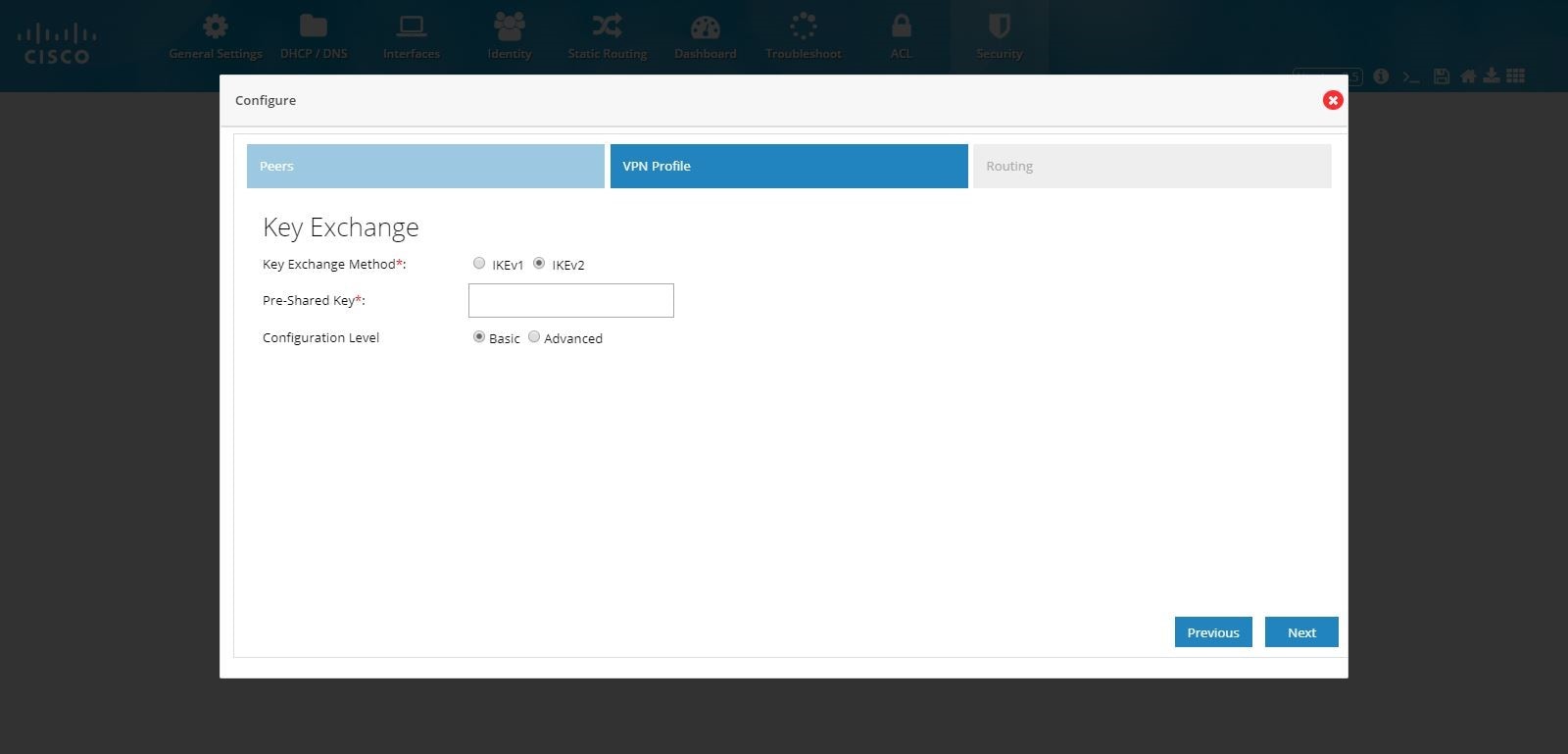
Figure 101 DMVPN Hub Configuration (VPN Profile Advanced Options)
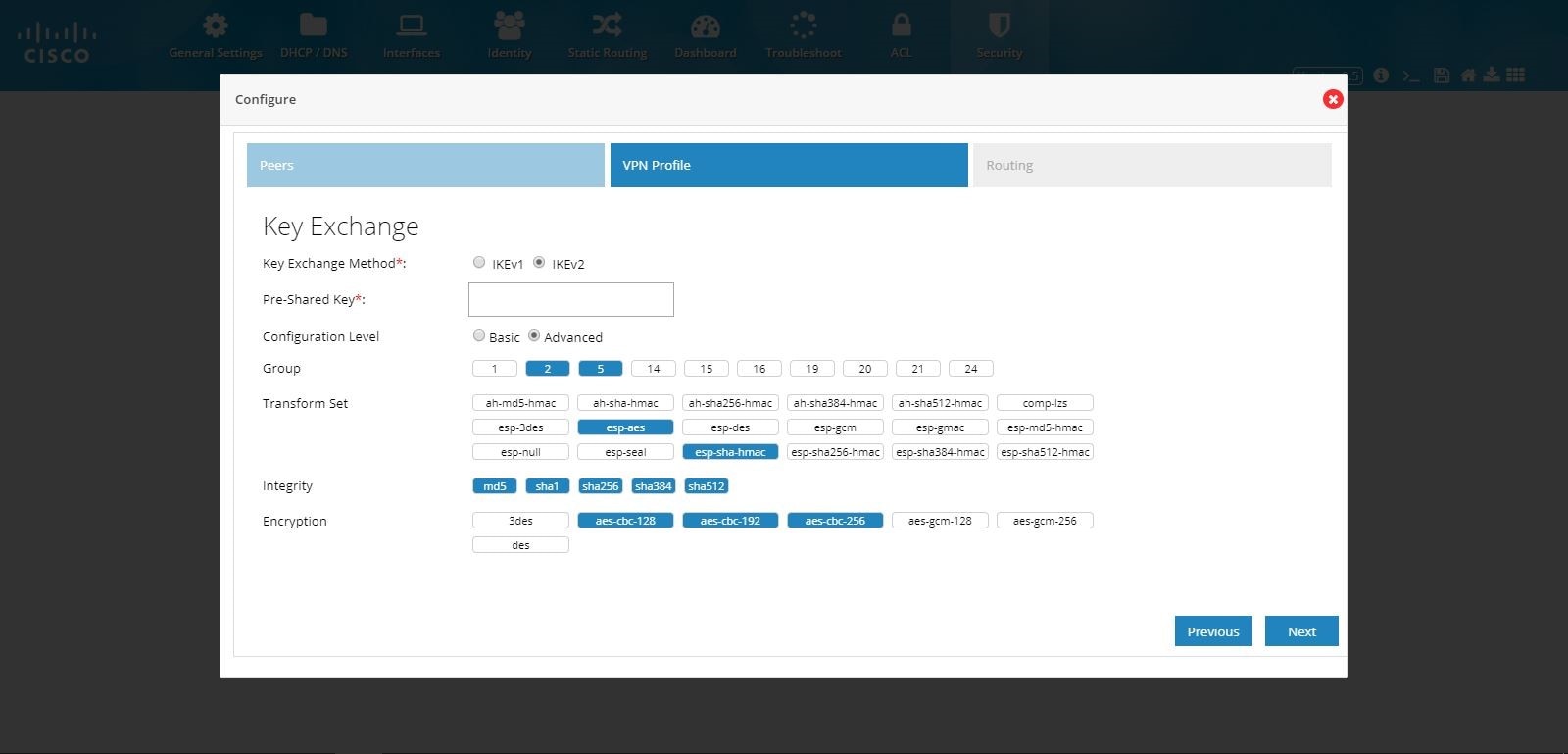 6.
6.
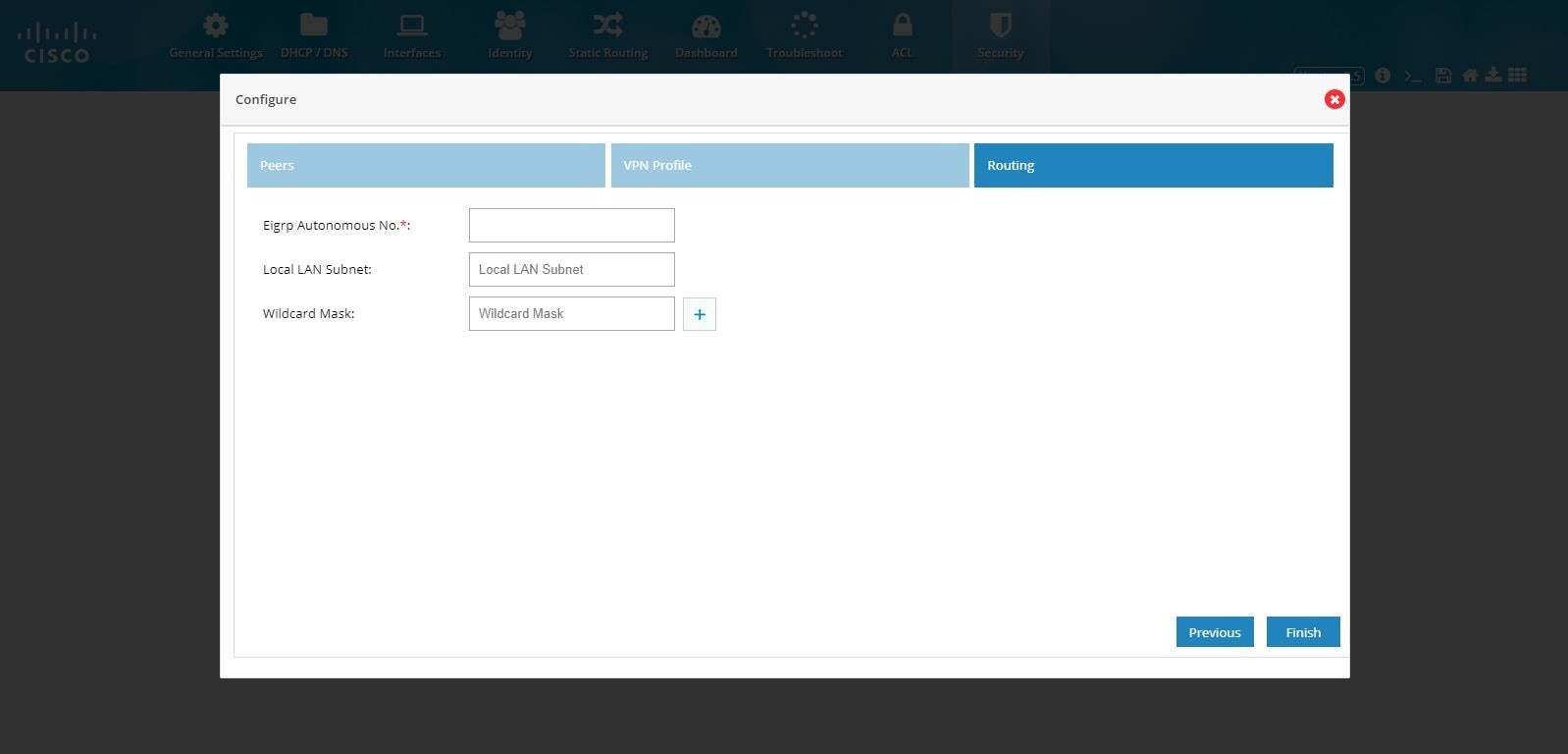
Provide the routing configuration.
7.
Provide an EIGRP Autonomous number in the range 1–65535.
Figure 102 DMVPN Hub Configuration (Routing)
 8.
8.
Click
Finish.
Figure 103 DMVPN Hub Configuration (Completed)
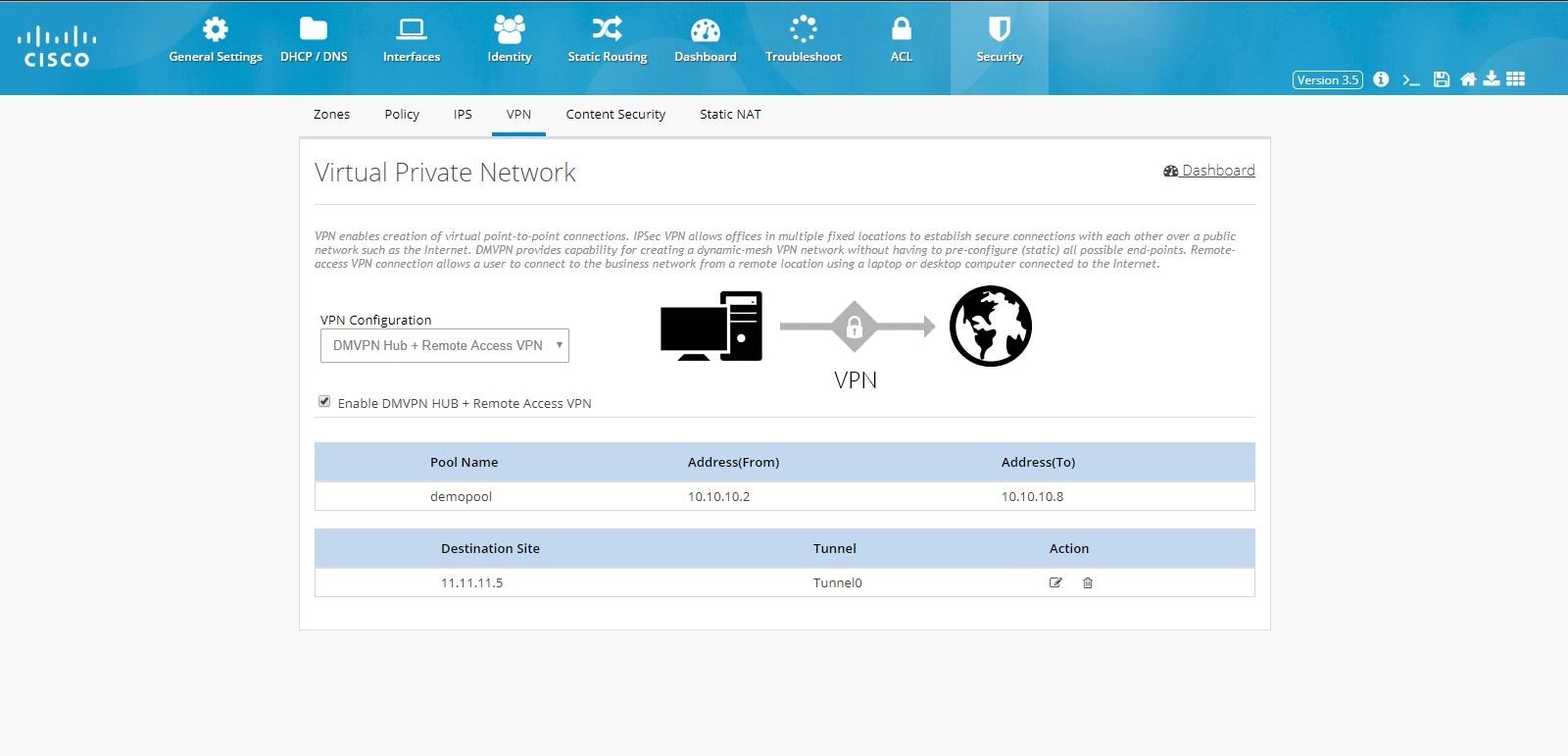
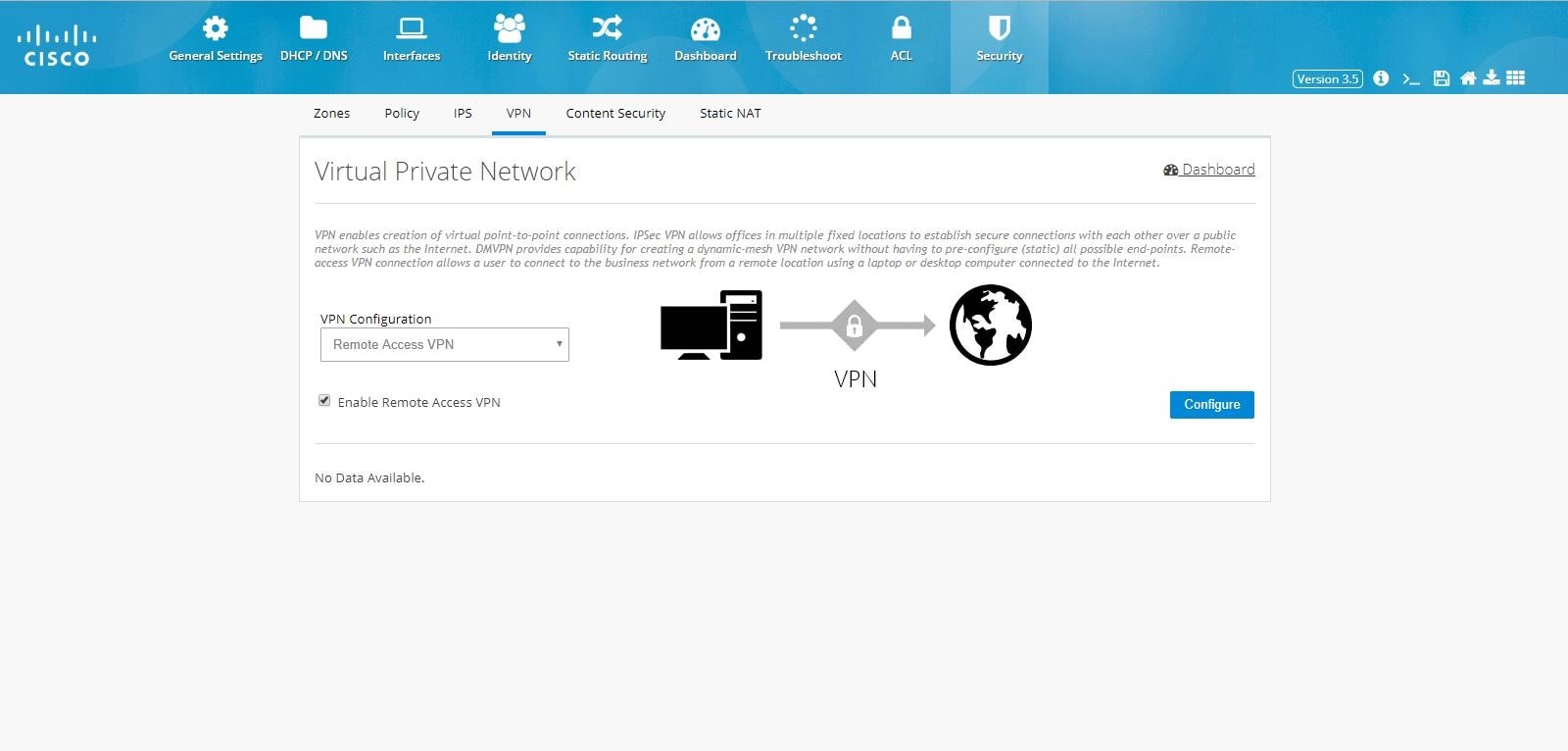
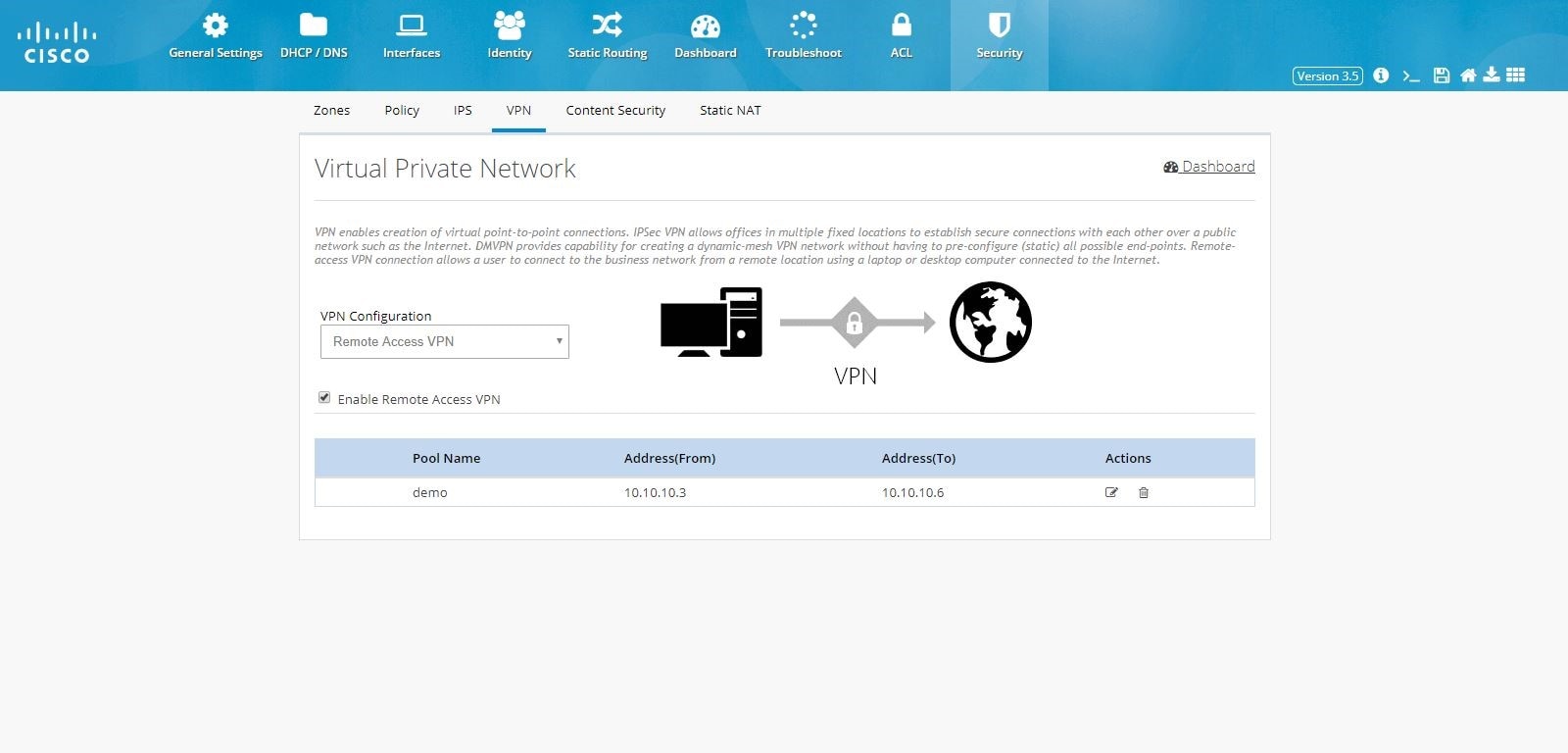
Remote Access VPN Configuration
To configure Remote Access VPN, perform these steps:
1.
Click Security > VPN and select Remote Access VPN option.
2.
Click the Enable Remote Access VPN check box, and click
Configure.
Figure 104 Remote Access Configuration
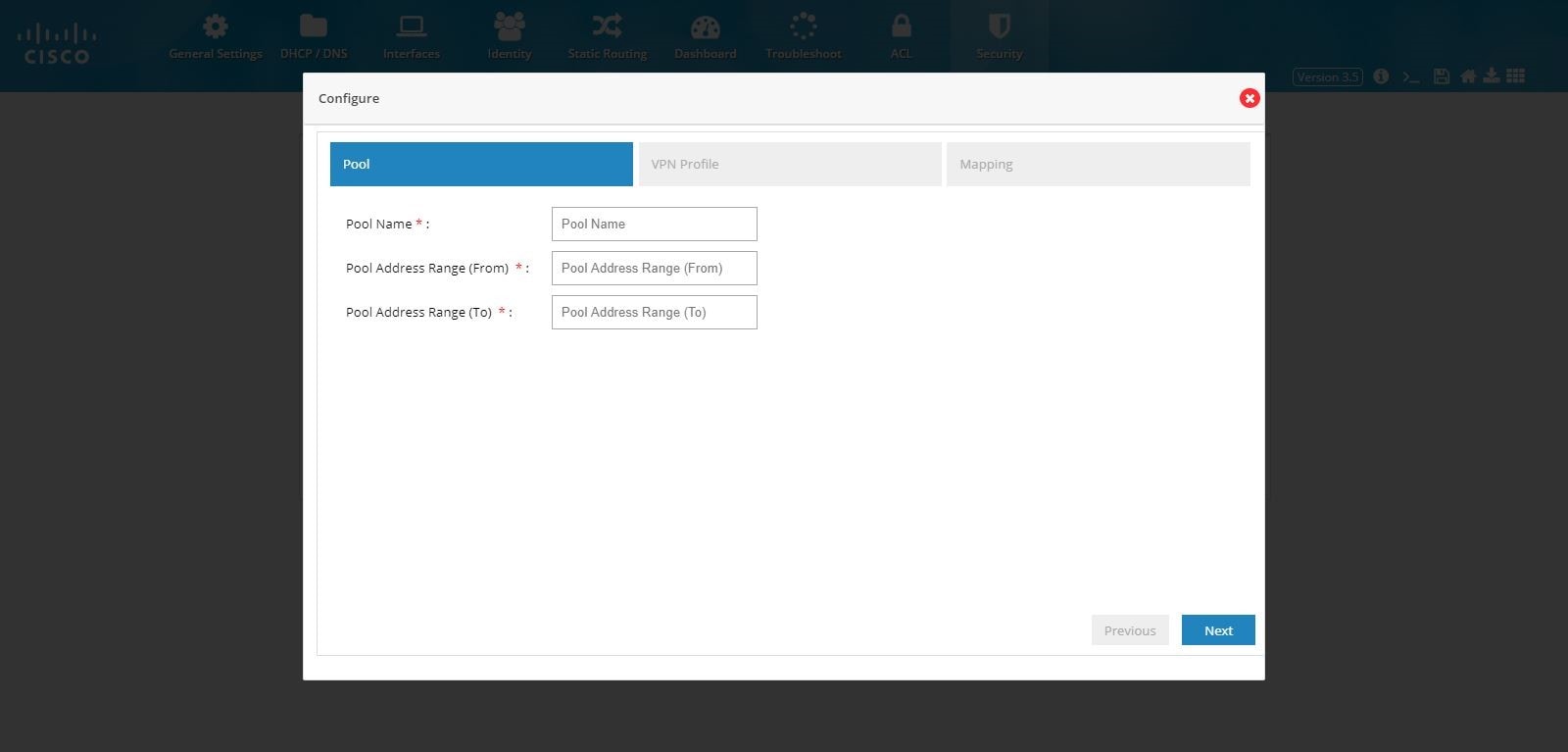
 3.
3.
Provide Pool Name and the range of IP Addresses for the pool.
Figure 105 Remote Access Configuration (Pool)
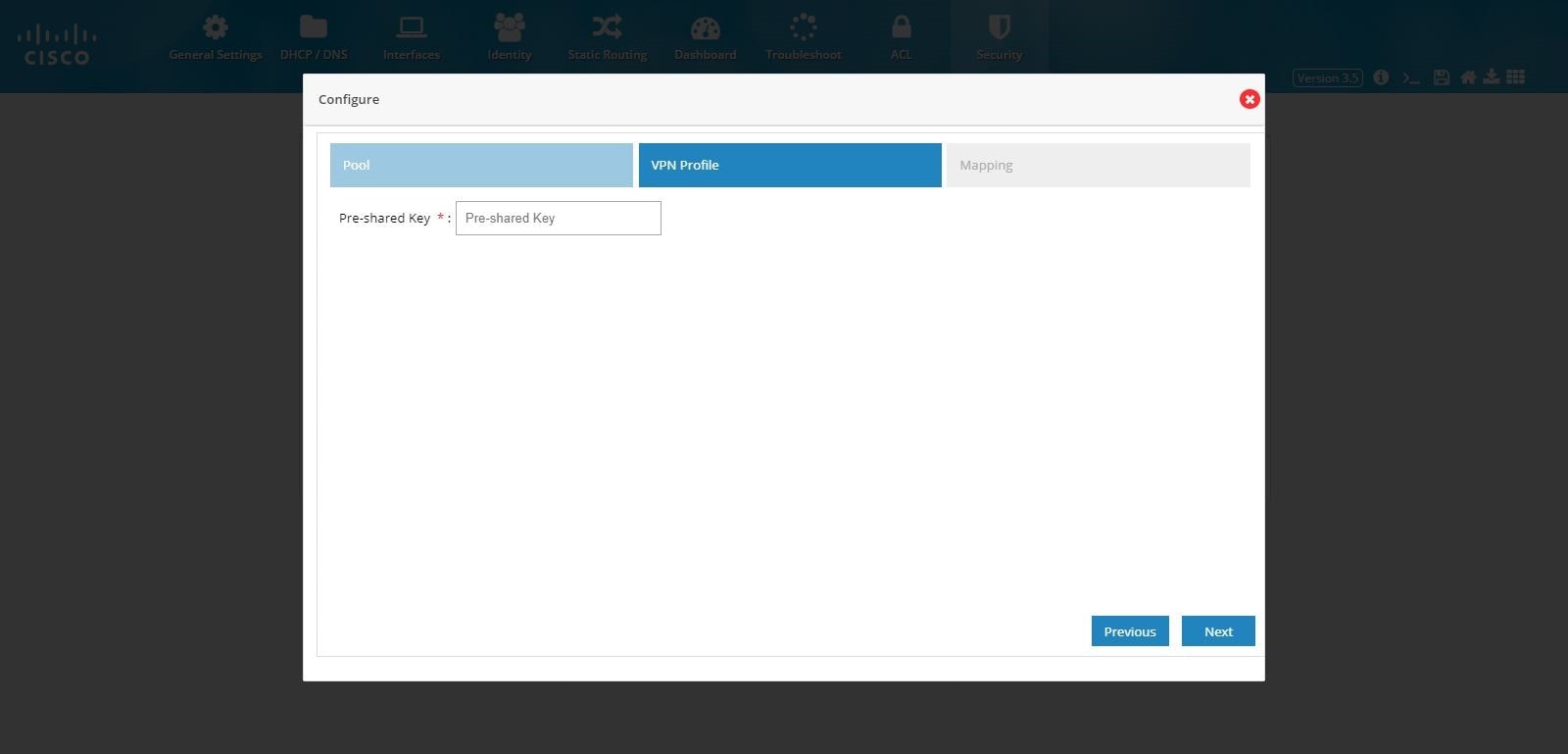
 4.
4.
Provide the Pre shared Key.
Note: By default, Remote Access VPN configuration supports only IKEv1 Key Exchange model and IP Sec enabled L2TP protocol.
Figure 106 Remote Access Configuration (VPN Profile)
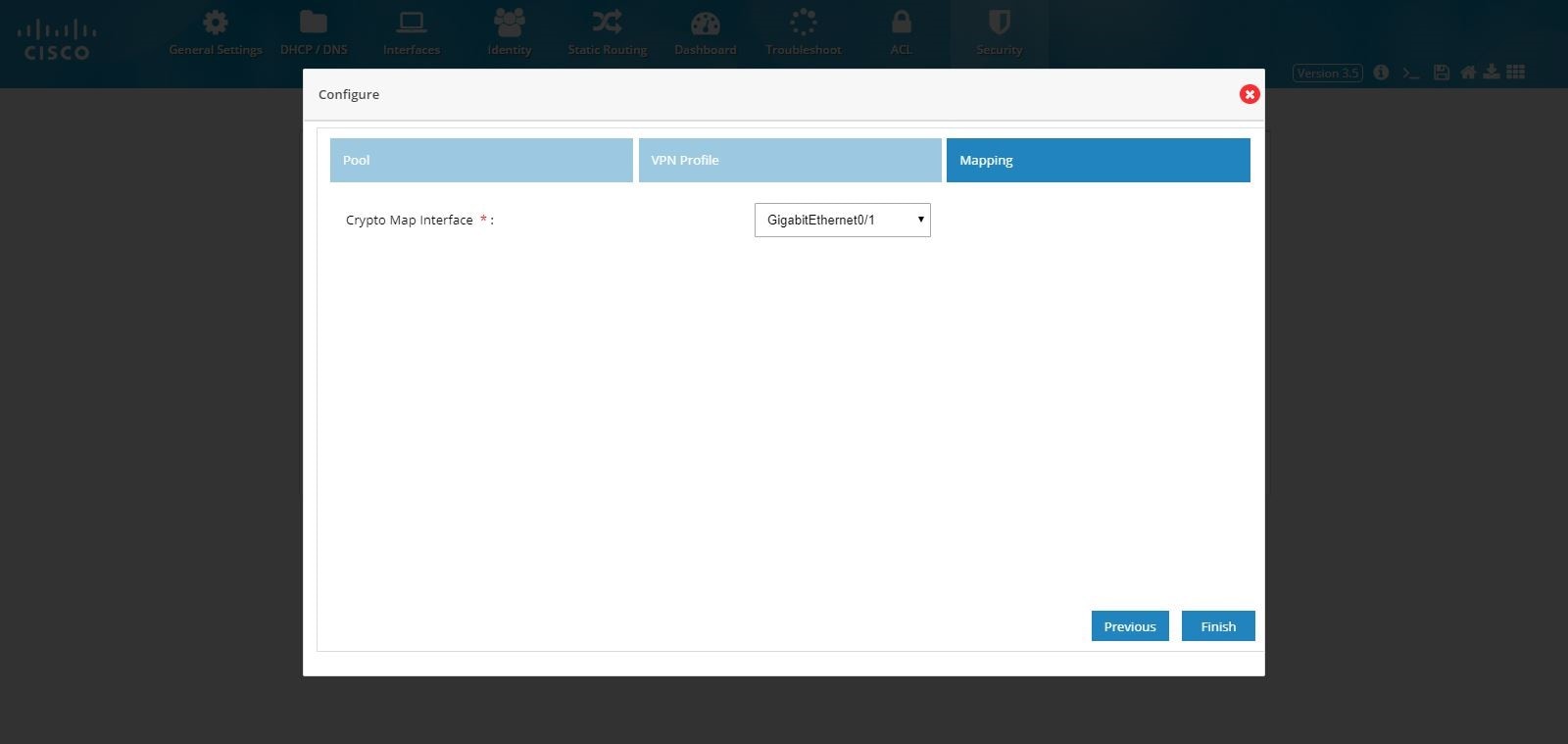
 5.
5.
Select the Crypto Map interface.
Figure 107 Remote Access Configuration (Mapping)
 6.
6.
Click
Finish.
Figure 108 Remote Access Configuration (Completed)
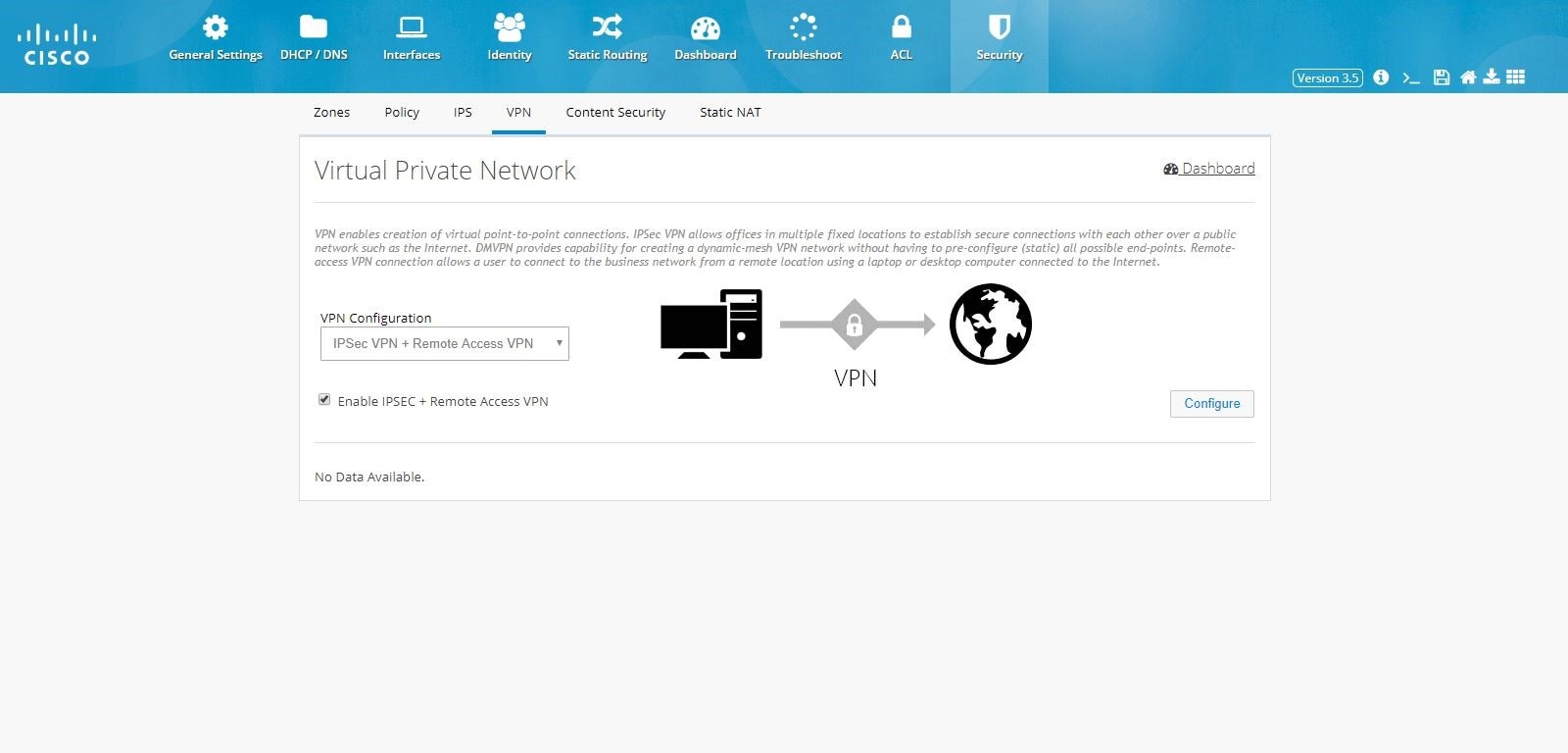
IPSec Multi-Site and Remote Access VPN Configuration Combination
To configure the combination of IPSec Multi-Site and Remote Access VPN configurations:
1.
Click Security > VPN and select
IPSec VPN + Remote Access option from VPN Configuration option.
2.
Click the Enable IPSEC + Remote Access VPN check box, and click
Configure.
Figure 109 IPSec Multi-Site and Remote Access Configuration Combination
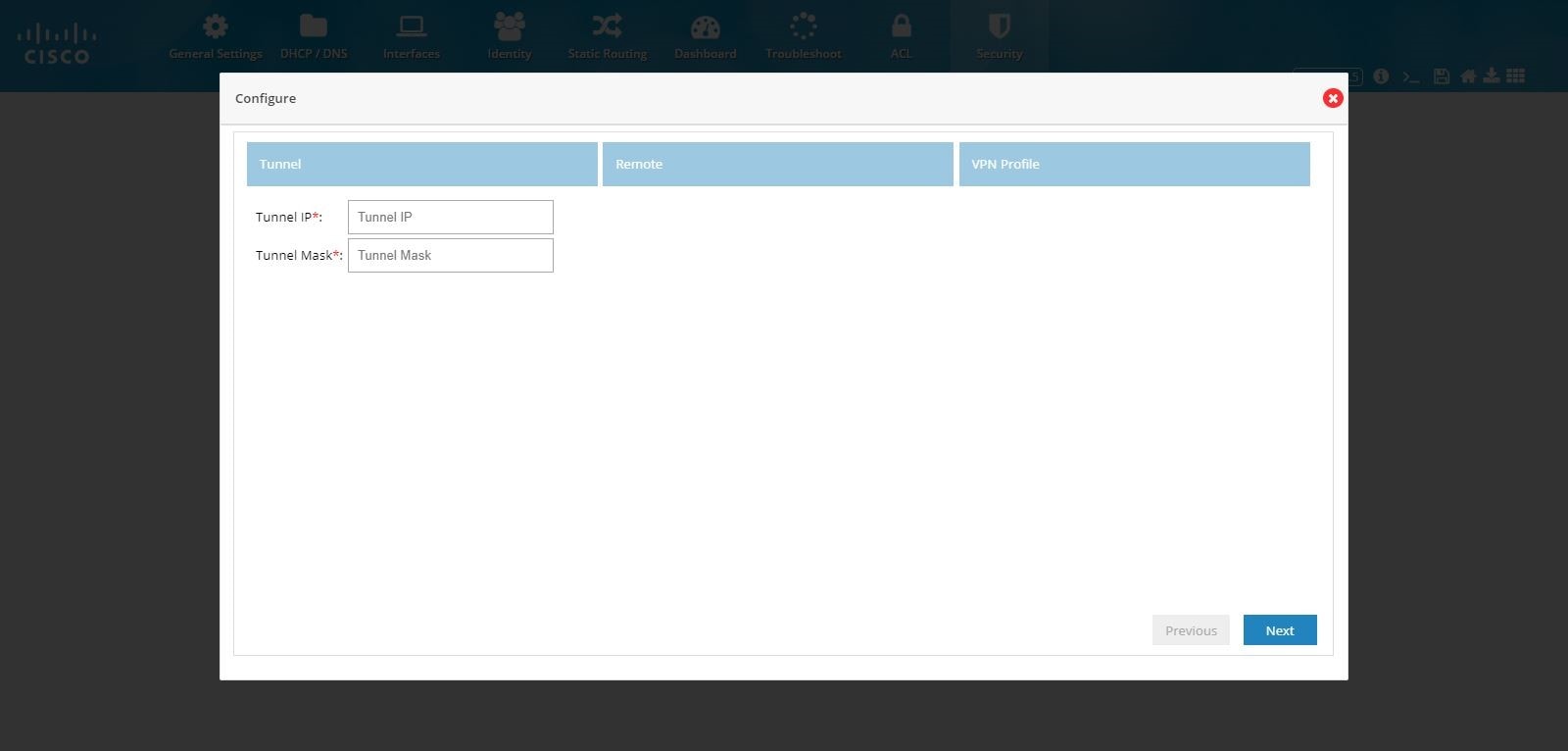
 3.
3.
Provide Tunnel IP and Mask for the site being configured.
Figure 110 IPSec Multi-Site and Remote Access Configuration Combination (Tunnel)
 Note:
Note: By default, from configuring site end, all the LAN side networks are allowed to access the other end through VPN tunnel.
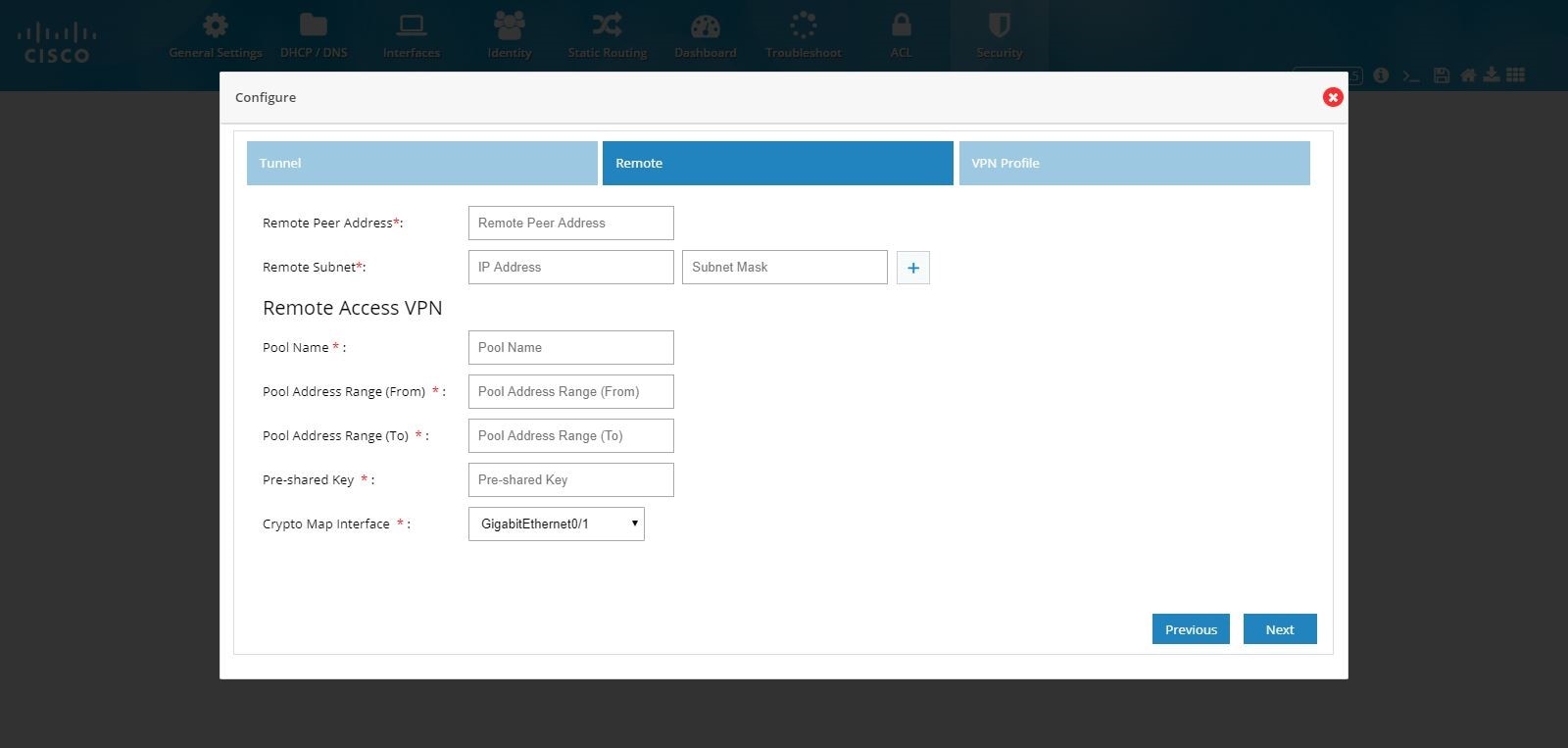
4.
Provide the Remote Peer Address (WAN IP address of the other end) information.
Enter the pool information, Preshared Key, and Crypto Map Interface.
Figure 111 IPSec Multi-Site and Remote Access Configuration Combination (Remote)
 5.
5.
Ensure that the IKEv2 is selected.
Note: IKEv2 is the only key exchange method available.
Figure 112 IPSec Multi-Site and Remote Access Configuration Combination (VPN Profile)
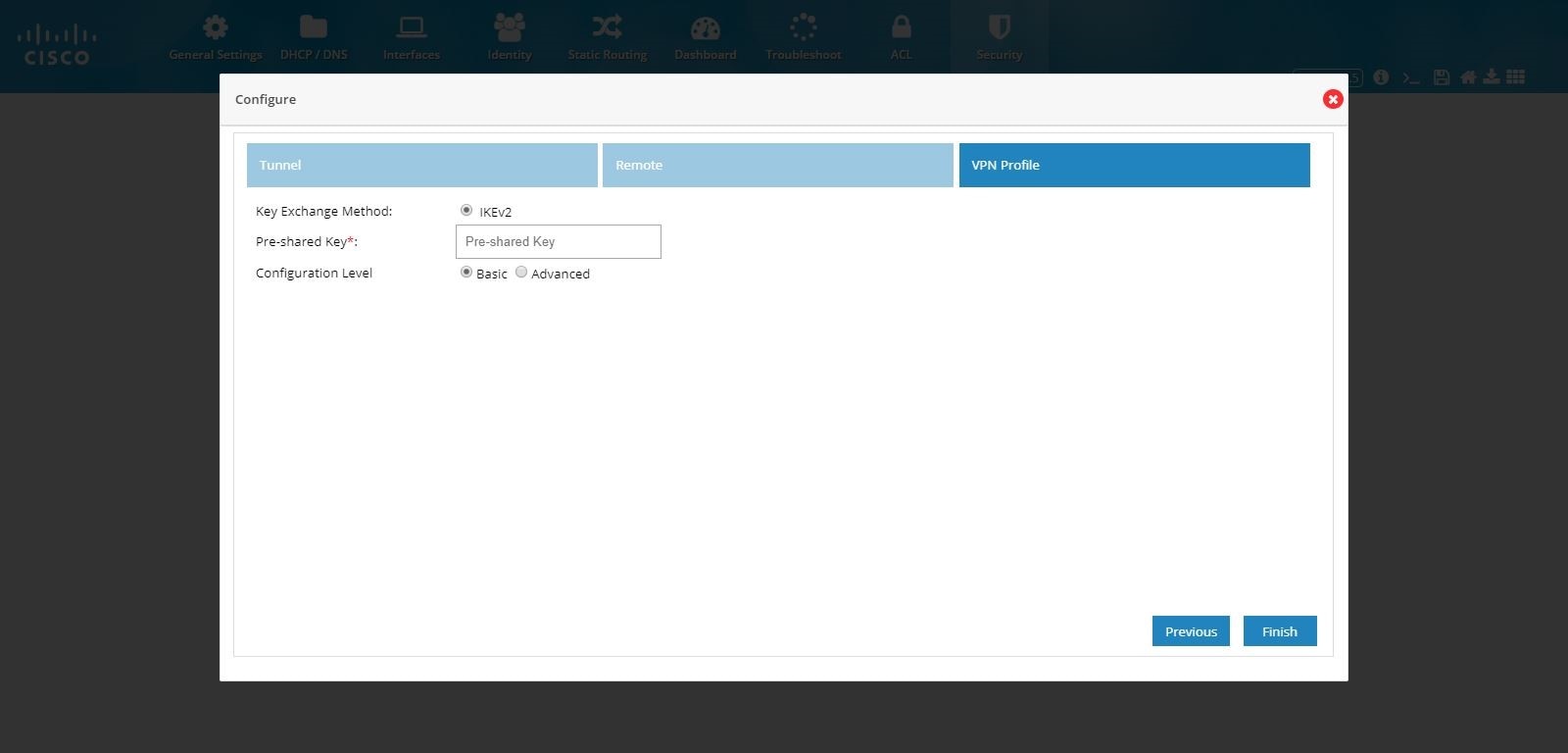
Figure 113 IPSec Multi-Site and Remote Access Configuration Combination (Advanced Options)
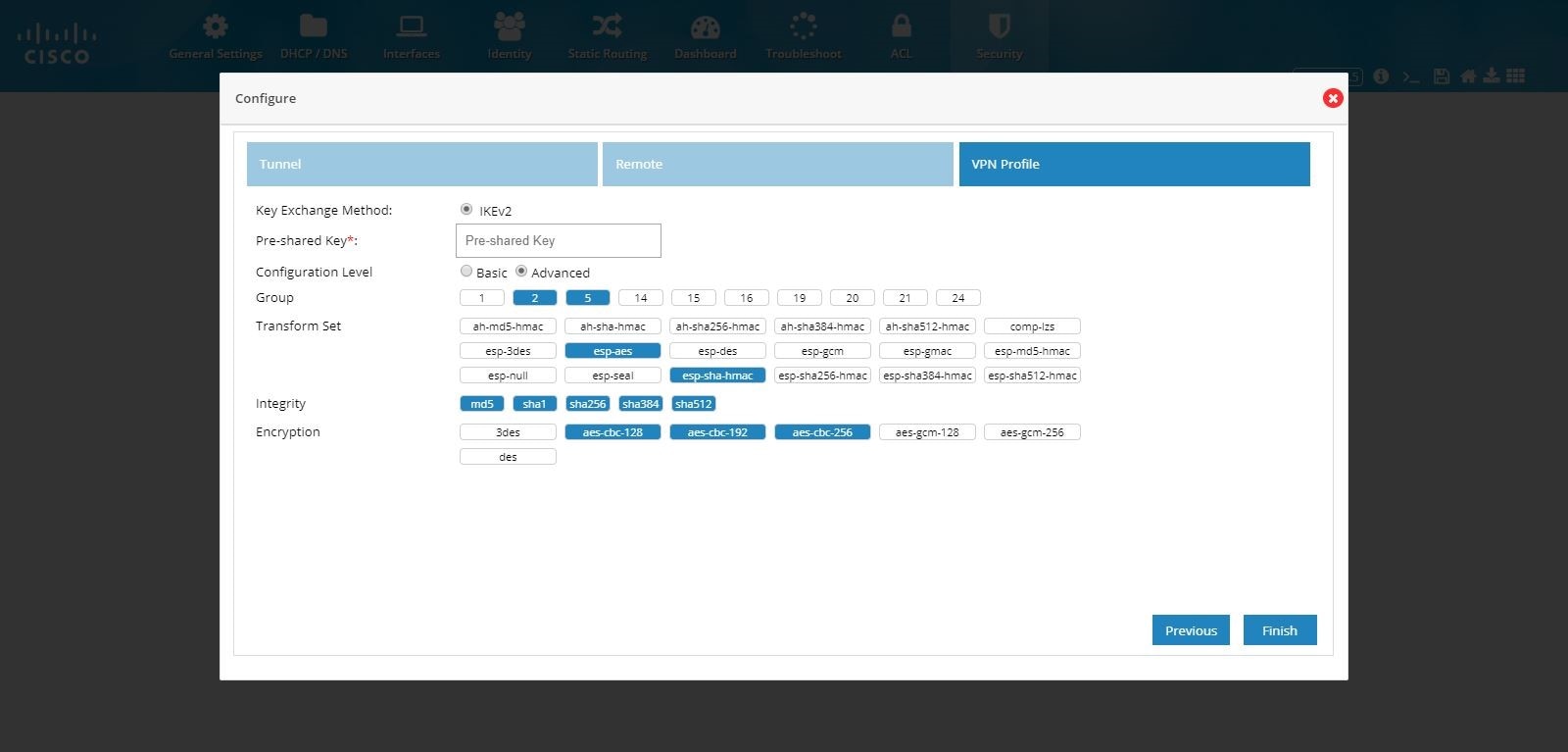 Note:
Note: If CCP Express is used
to configure the Multi-Site VPN, ensure that both the ends are
configured with CCP Express only. CCP Express internally uses the
transform set as esp-aes, esp-sha-hmac and IKEv2 Proposal with
encryption as 3des, integrity as md5 and Diffie Helman group as 2.
6.
Click
Finish.
Figure 114 IPSec Multi-Site and Remote Access Configuration Combination (Completed)
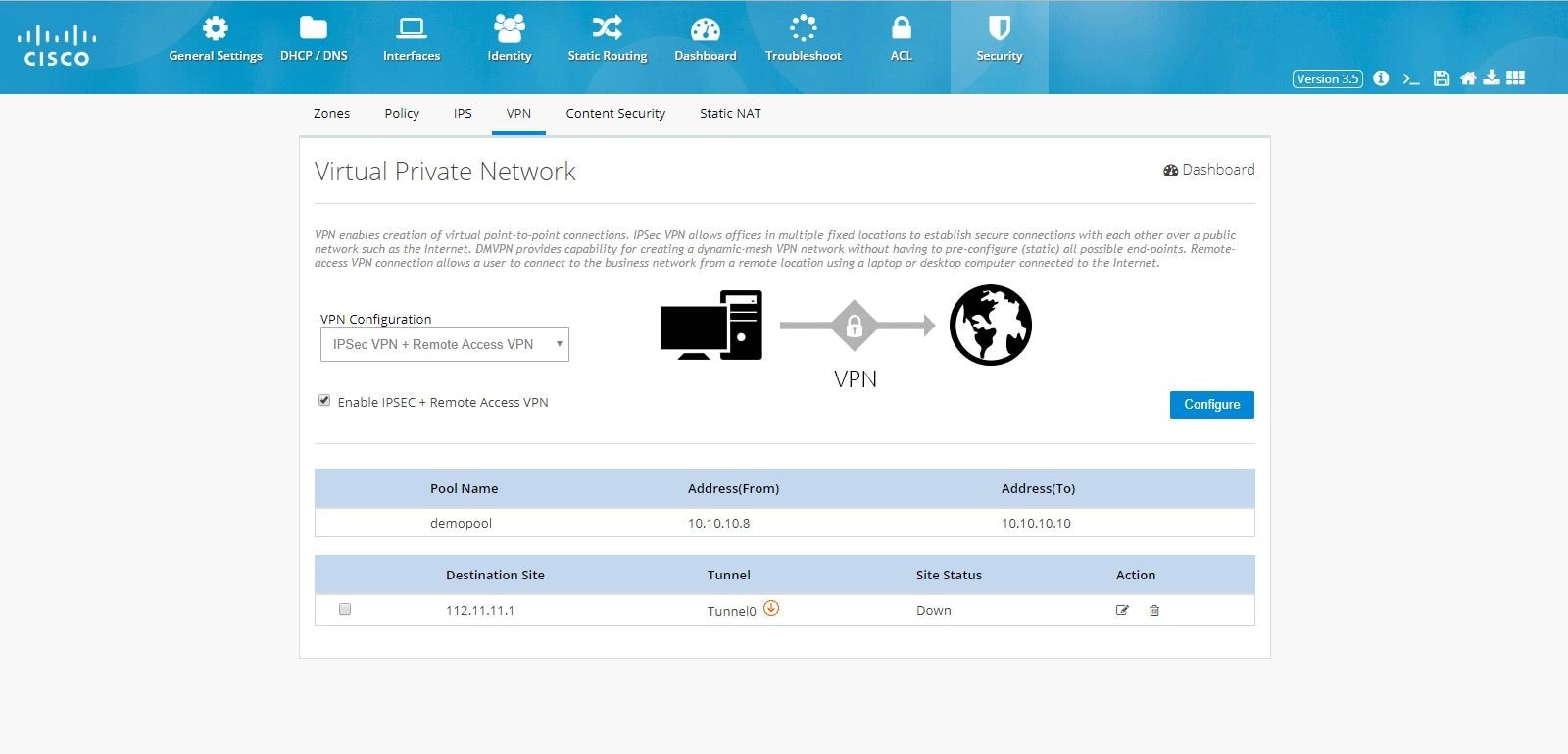
DMVPN Hub and Remote Access Configuration Combination
To configure the combination of DMVPN Hub and Remote Access VPN configurations:
1.
Click Security > VPN and select the DMVPN Hub + Remote Access VPN option from the VPN Configuration drop-down list.
2.
Click Enable DMVPN Hub + Remote Access VPN check box, and click
Configure.
Figure 115 DMVPN Hub and Remote Access Configuration Combination
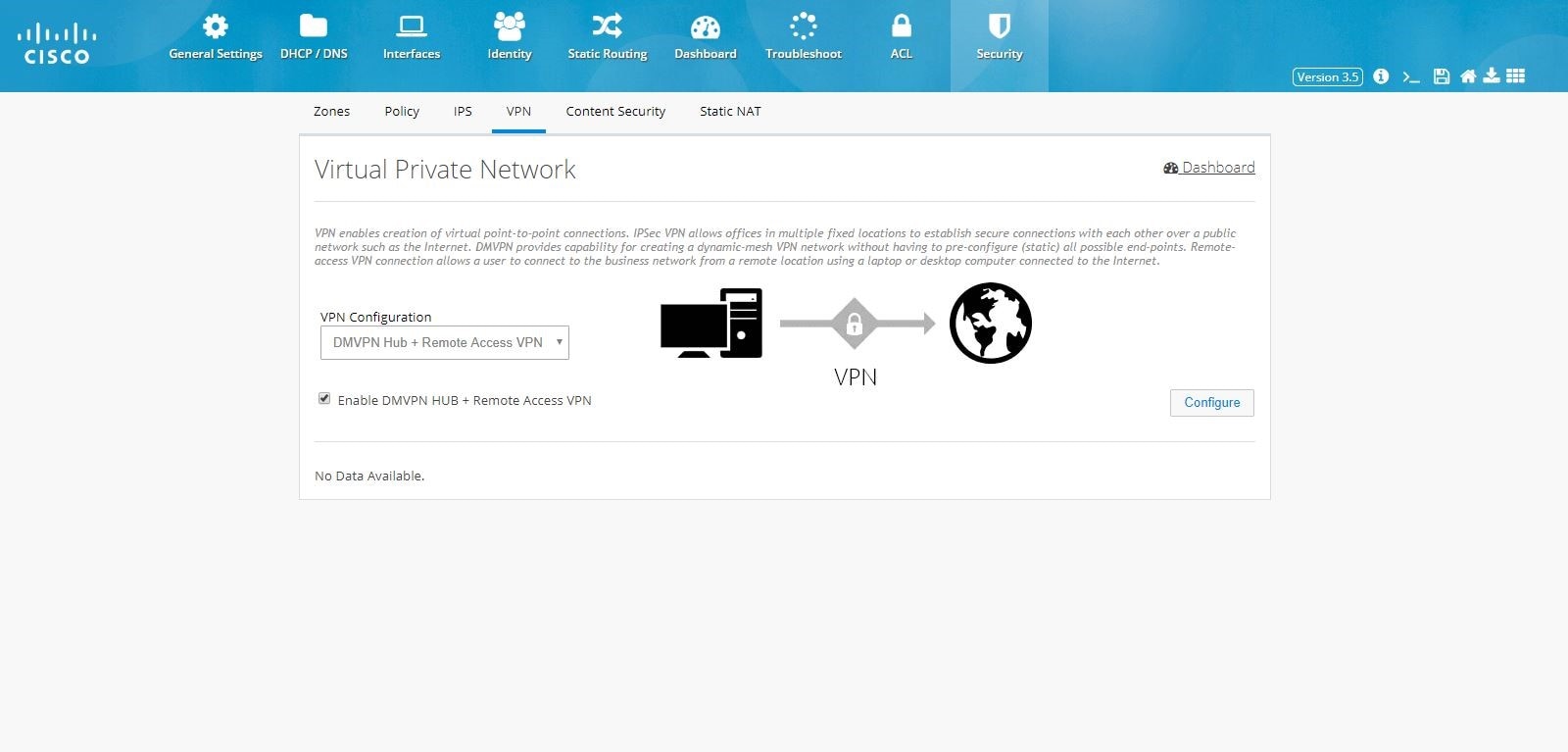 3.
3.
Provide Tunnel IP and Mask for the hub being configured.
Enter the pool information, Preshared Key, and Crypto Map Interface.
Figure 116 DMVPN Hub and Remote Access Configuration Combination (VPN Peers)
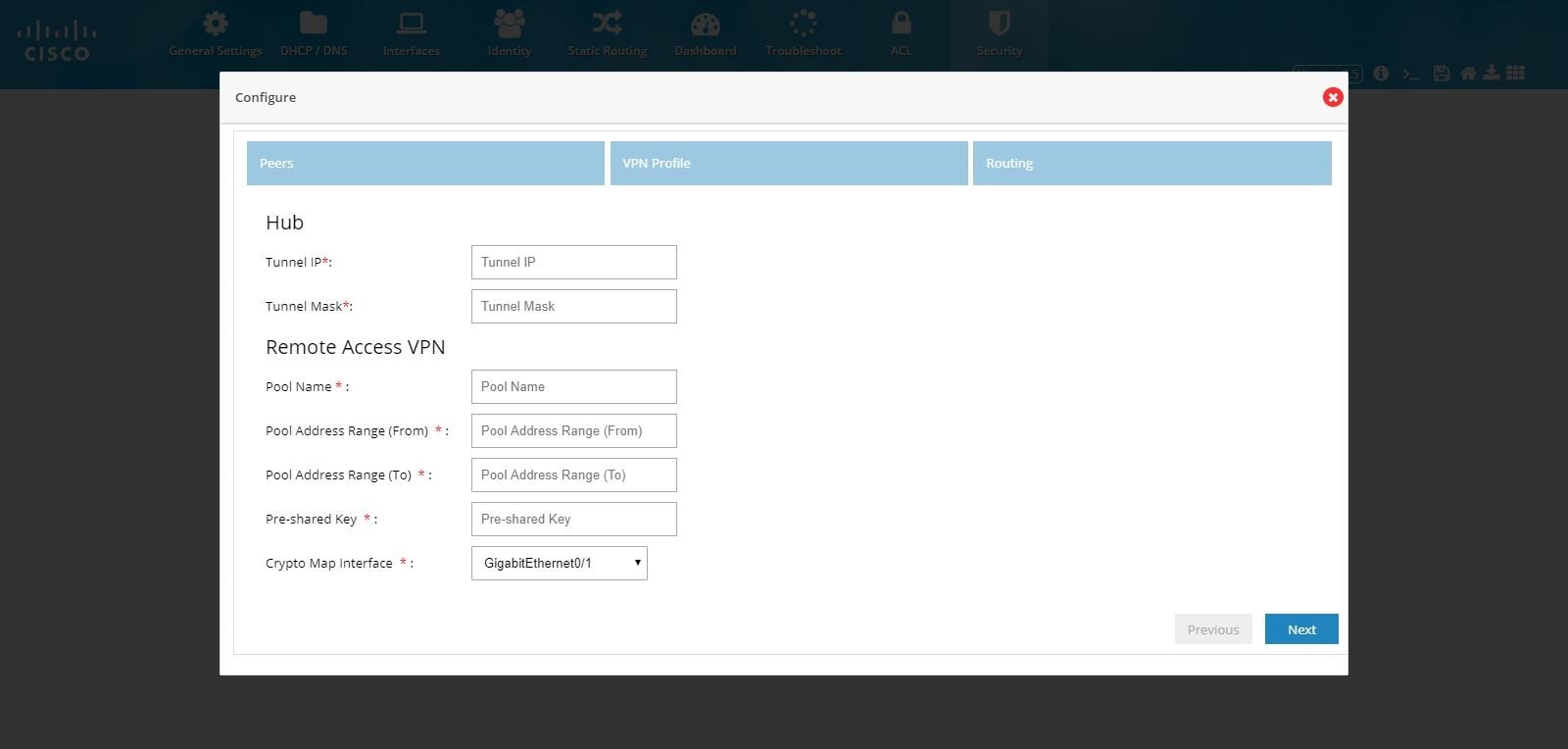 4.
4.
Ensure that the IKEv2 is selected.
Note: IKEv2 is the only key exchange method available.
5.
Provide the Pre-Shared Key.
Figure 117 DMVPN Hub and Remote Access Configuration Combination (VPN Profile)
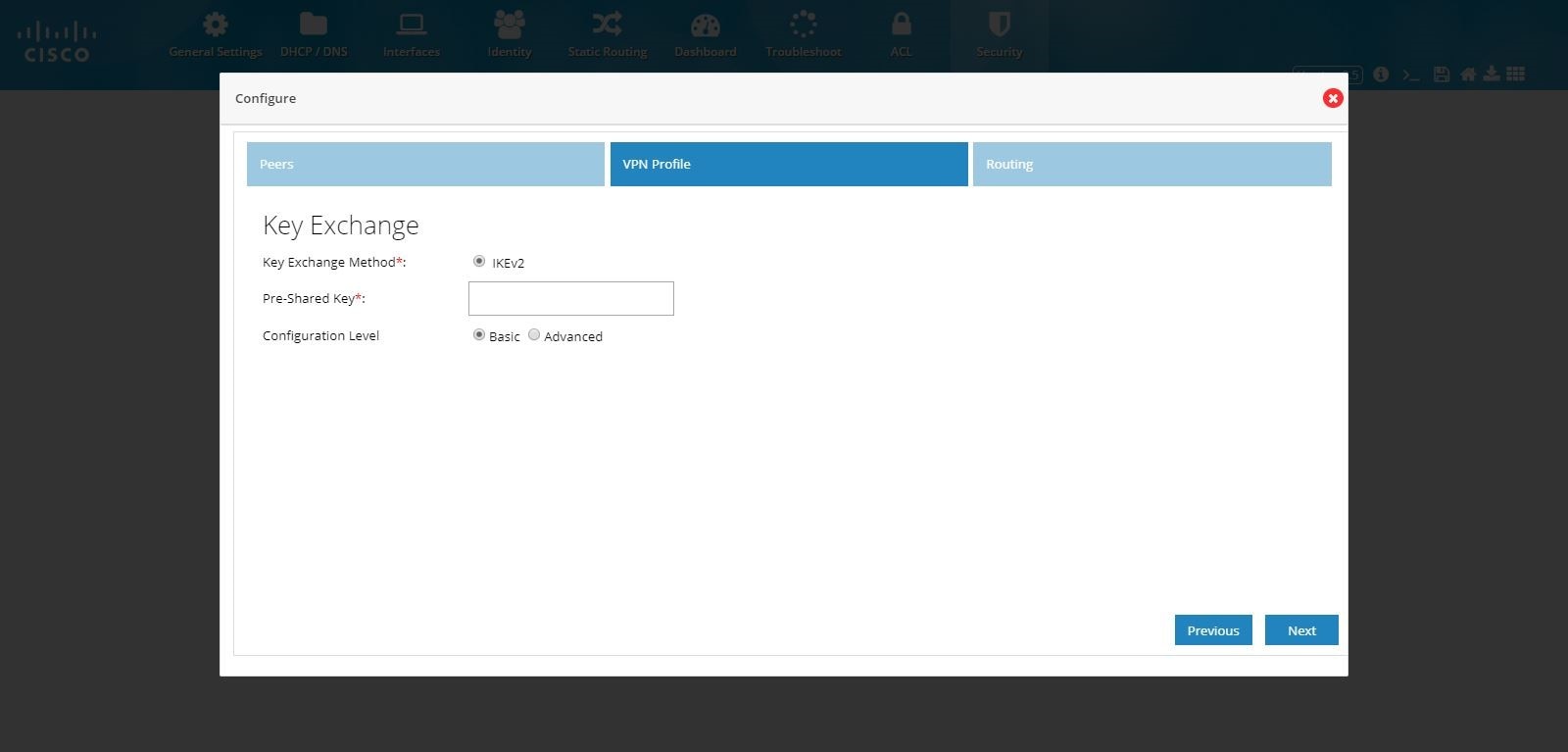
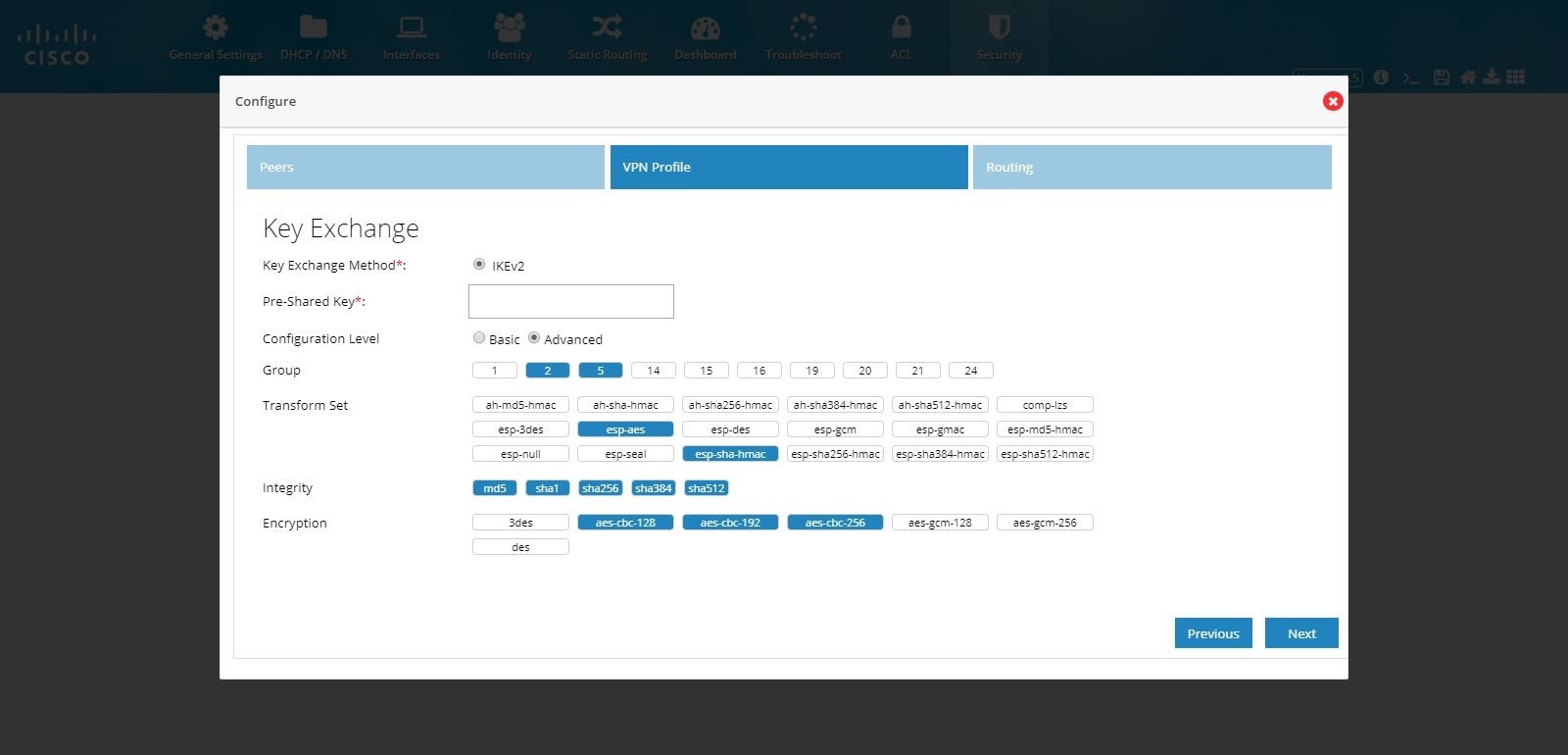
Figure 118 DMVPN Hub and Remote Access Configuration Combination (VPN Profile Advanced Options)
 6.
6.
Provide the routing configuration.
7.
Provide an EIGRP Autonomous number in the range 1–65535.
Figure 119 DMVPN Hub and Remote Access Configuration Combination (Routing)
 8.
8.
Click
Finish.
Figure 120 DMVPN Hub and Remote Access Configuration Combination (Completed)

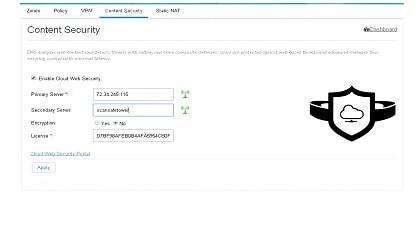
Content Security
Cloud based 'Security as a Service’
(SecaaS) such as Cloud Web Security (CWS) is a scalable means to provide
market-leading web security to quickly and easily protect the network
from web-based threats, such as Malware, while saving bandwidth, money,
and resources. CWS provides Anti-X functionality (anti-malware,
anti-bot, anti-virus, and anti-phishing) on ISR-G2 itself without the
need for expensive Security Appliances in branch, small offices.
To configure content security, perform these steps:
1.
Click Security > Content Security.
2.
Provide Primary CWS Server IP address or DNS resolvable hostname and Secondary server information.
3.
Provide the license key received from CWS service provider and specify if it is an encrypted or unencrypted key.
Figure 121 Content Security Page
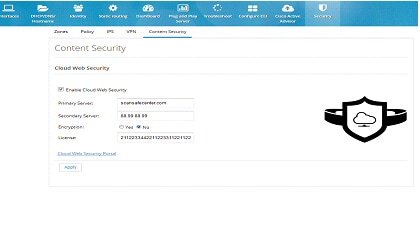
Edit Content Security
After CWS is fully configured and the
tower is reachable, a green tower icon displays as shown in the screen
below. Otherwise, the tower is displayed in red.
Figure 122 Content Security Page
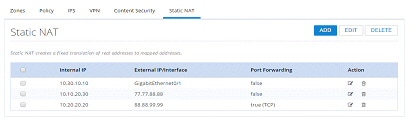
Static NAT
Static NAT creates a fixed translation
of unregistered real address to mapped registered address. Also with
port forwarding option, it is possible to open ports in response to
inbound traffic for a specified service.
To create a static NAT:
1.
Click Security > Static NAT. To add a Static NAT, click Add. A dialog box opens.
Figure 123 Static NAT Page
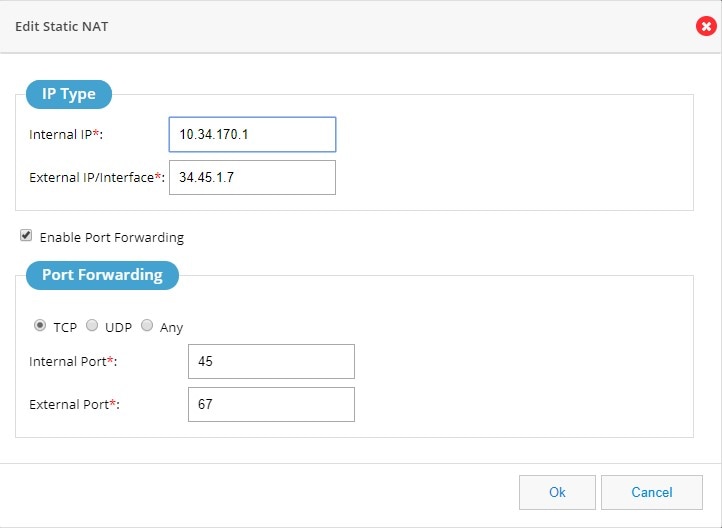
 2.
2.
Provide the Internal IP address which needs to be translated and the external IP address or Interface.
3.
If you need to send the traffic to specific port, click Enable Port
Forwarding check box, and select the type of port, for example TCP or
UDP. If the port type is not known, select Any option which supports
both the type of ports.
4.
After selecting the ports, specify the internal and external ports.
Figure 124 Edit Static NAT Page

 Aquí podemos apreciar las dimensiones de la placa Google Coral
En la web podrás encontrar también el Google Coral USB Accelerator (un dispositivo USB similar al Movidius de Intel), diseñado para acelerar la inferencia de machine learning en PCs y Raspberries que funcionen con Debian), así como una cámara de 5 Mpx, accesorio para la placa Google Coral disponible por 24,99 dólares.
Aquí podemos apreciar las dimensiones de la placa Google Coral
En la web podrás encontrar también el Google Coral USB Accelerator (un dispositivo USB similar al Movidius de Intel), diseñado para acelerar la inferencia de machine learning en PCs y Raspberries que funcionen con Debian), así como una cámara de 5 Mpx, accesorio para la placa Google Coral disponible por 24,99 dólares.
 Aquí podemos apreciar las dimensiones de la placa Google Coral
Aquí podemos apreciar las dimensiones de la placa Google Coral 














































































































